Detect and block run-time attacks on known and unknown code vulnerabilities with greater precision
Contrast Protect with Runtime Application Self Protection (RASP) is production application and API protection that blocks attacks and reduces false positives, helping developer teams prioritize vulnerability backlogs
Block attacks against vulnerabilities not yet fixed or patched
Unlike perimeter defenses, instrumentation and sensors accurately detect and block runtime application attacks. Get a firm yes or no on whether the exploit reached its target. Protects against many zero-day attacks without tuning or reconfiguration.
Game-Changing
Forensics
Give AppSec, SecOps & Dev accurate, detailed information: the lines of code, queries executed, files accessed, and more. Faster remediation.
APPLICATION PROTECTION FOR ALL ORGANIZATIONS
Whether it’s large scale enterprise IT environments, or mid-market growth companies, you get the application protection you need. Harden your applications against zero-day attacks and other vulnerabilities from the inside.

Contrast Protect for Log4j
Contrast Protect can stop the Log4j vulnerability today, in your application production systems, without requiring software upgrades. In addition, Contrast Protect defended the applications against the underlying vulnerability. This means, Contrast was protecting you against log injections long before it was disclosed as a CVE.
Continuous Security Observability from the Inside
-
Immediately know when things
go wrong and why -
Code-level telemetry with rich,
actionable guidance -
Prioritized, confirmed vulnerabilities with remediation help specific to your environment
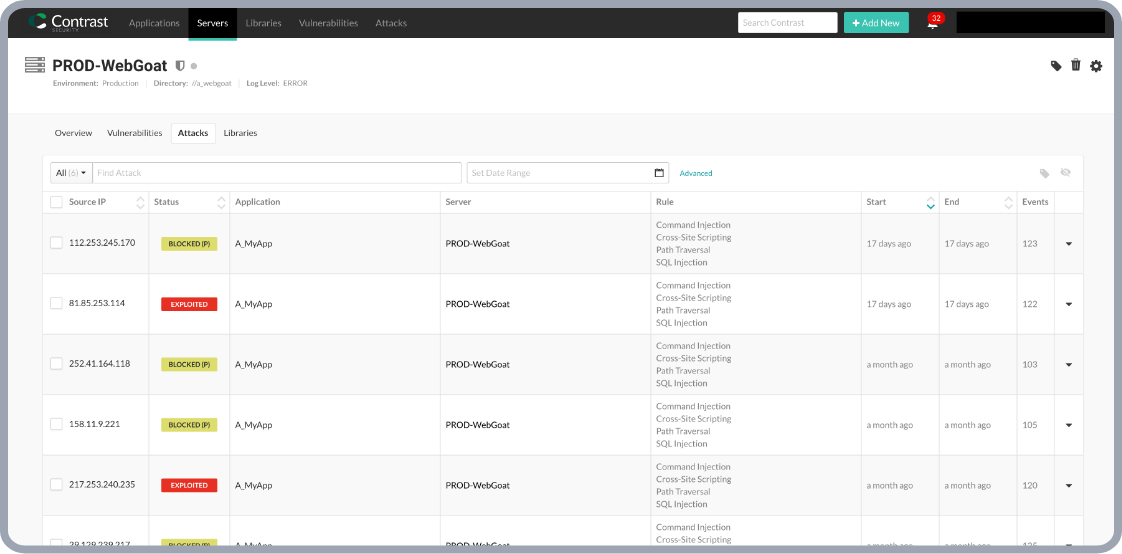
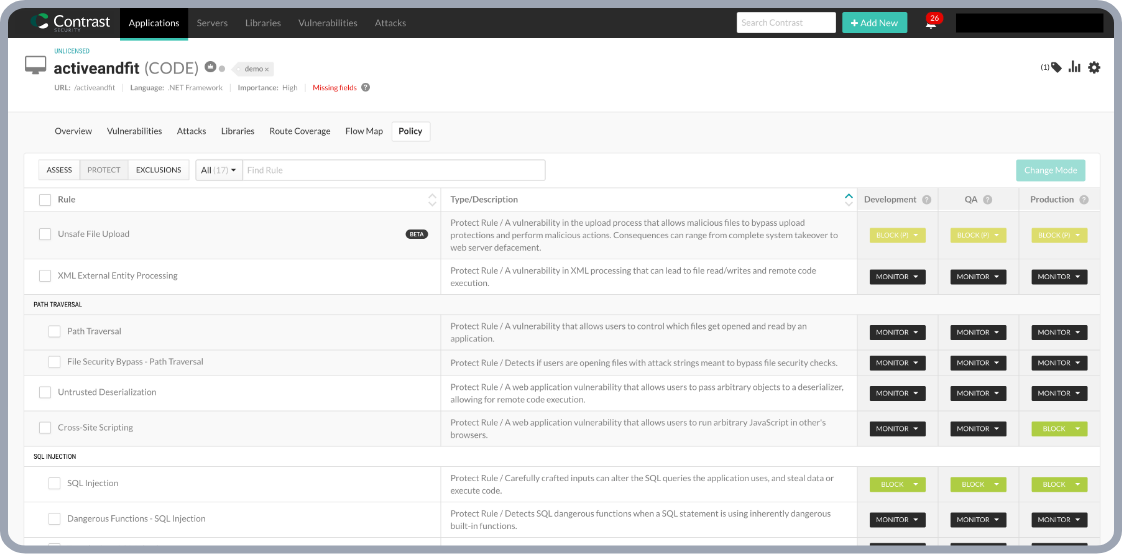
Embedded Runtime Application Self Protection Control (RASP Security)
-
Accurate, compliant, and dynamic
runtime exploit prevention -
Application runtime instrumentation on the
inside verifies exploitable attacks -
Dramatically reduces noise and accelerates
security posture
Simple Auto-Scaling and Security Portability
-
Simple auto-scaling protection in lockstep with your application runtime
-
DevOps-native process fit that deploys anywhere
without bottlenecks -
Seamless CI/CD and affordable total cost
of ownership (TCO)
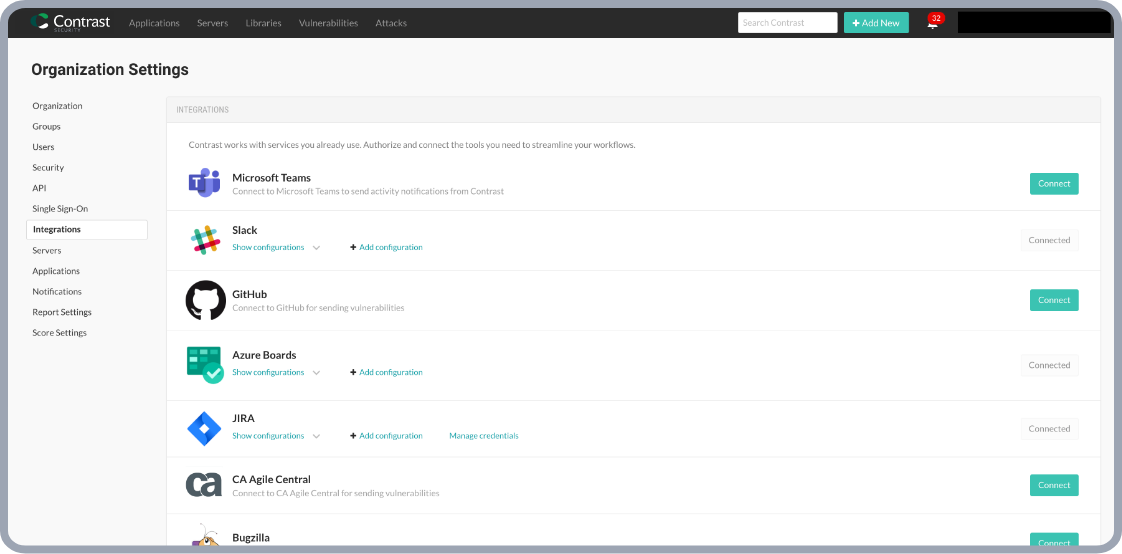
Zero days blocked before discovery hall of fame
Types of attacks stopped
- Command injection
- OGNL injection
- JNDI injection
- SSRF
- Template injection
- Unsafe file upload
- Path traversal
- Reflected XSS
- SQL/NoSQL injection
- Unsafe deserialization
- XXE
- ClassLoader manipulation
Contrast prevents zero days years before disclosure
- CVE-2023-22527 Atlassian Confluence – template injection
- CVE-2023-34040 Spring/Kafka – unsafe deserialization
- CVE-2023-22965 Spring4Shell – malicious data binding
- CVE-2021-44228 Log4Shell – JNDI injection RCE
- CVE-2021-26084 Atlassian Confluence EL injection
- CVE-2020-17530 Apache Struts2 – EL injection
- CVE-2020-11651 Python Salt – authentication bypass
- CVE-2020-11652 Python Salt – directory traversal
- CVE-2020-9484 Apache Tomcat – unsafe deserialization
- CVE-2019-2725 WebLogic – unsafe deserialization
- CVE-2019-0230 Apache Struts2 – EL injection
- CVE-2018-11776 Apache Struts2 – EL injection
- CVE-2016-0792 Jenkins XStream – unsafe deserialization
Resources to help you get
secure code moving
Whitepaper: Defense-in-depth web AppSec: The case for having both RASP and WAF
This white paper explores the value of having both RASP and WAF for web AppSec and how they can work together to provide a more comprehensive and effective approach.

eBook: State-of-the-Art Protection and Observability Is AppSec Exactly Where It Is Needed--In Production Runtimes
This eBook examines how runtime application protection and observability delivers a state-of-the-art approach to application security. Readers will gain the information needed to evaluate runtime application protection and observability solutions and how they augment perimeter defenses (such as WAFs).

Podcast: Protecting Apps from Known and Unknown Attacks
Contrast Security's Vikas Phonsa and Blake Connell are experts when it comes to application production runtime protection. In this Inside AppSec podcast, they discuss how perimeter-defense approaches are ineffective in blocking many types of threats and are highly inefficient to deploy and manage—often stretching SecOps teams to breaking points.
Webinar: Stop SQL Injection application attacks in their tracks.
Last year, 98% of organizations experienced three or more successful application exploits. In response, President Biden issued an executive order to strengthen cybersecurity. Contrast Protect meets this mandate by securing production applications from the inside, offering unmatched insights and remediation capabilities beyond traditional perimeter defenses.

WAF and RASP: Raising the bar for application protection
Read this eBook to learn two technologies: Web Application Firewall (WAF) and Runtime Application Self Protection (RASP) technology and why they are better together.

Blog: Contrast Security Protect shields applications from zero-day attacks
Contrast Security’s Protect solution helps midsize and growth companies defend against emerging zero-day vulnerabilities and application security attacks.
Experience Contrast Protect
Learn how instrumentation works to find vulnerabilities in custom and open-source code and how it compares to legacy application security approaches.
Discover other products on the
Contrast Runtime Security Platform
Contrast Scan
Identify and fix real vulnerabilities faster with unparalleled scan accuracy
Contrast SCA
Test and protect third party, open-source code moving through your software supply chain






