LOG4J2 Vulnerability Exploit: What Steps to Take Now
Stop Log4j2 exploits now without patching.
what IS LOG4J
Log4j is a programming library (ie. pre-written code) that appears in millions of computer applications globally. It is free, open-source, and has been widely-used since 2001. The updated version of LOG4J is the LOG4J library.
Applications use Log4j to write short amounts of information into files/databases for “logging” purposes.
results overload
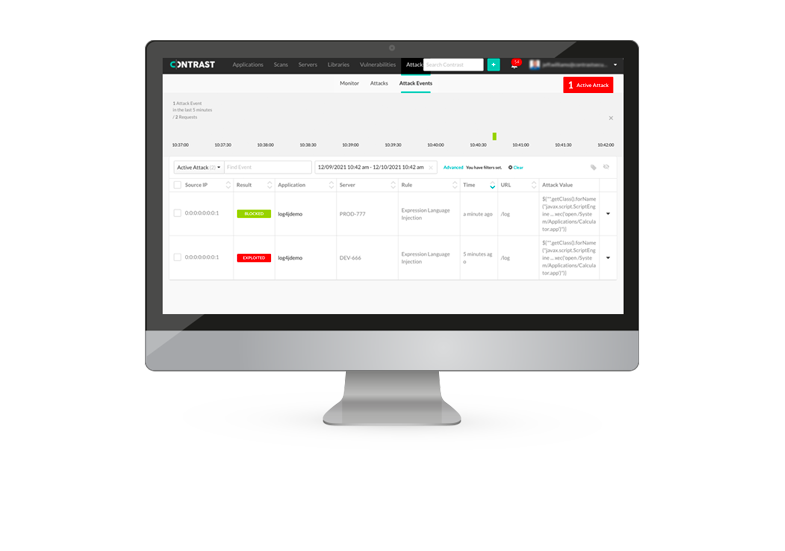
On Dec 9th, 2021, users discovered that by exploiting the Log4j library, they could access unauthorized information or control a computer remotely.
Hackers then began using Log4j to hack into large enterprise (Apple, Amazon, Twitter, Baidu, etc.) and government systems. The extent of the Log4j exploit impact globally is still unfolding.
why does the Log4j exploit matter to me?
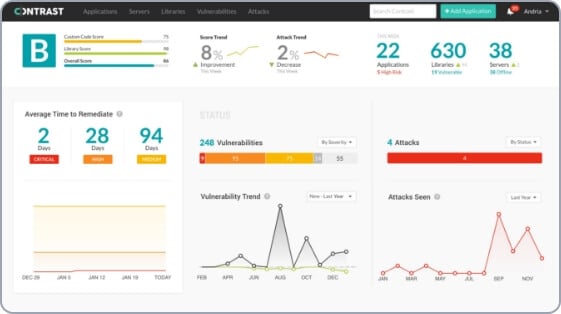
Any vulnerable system can be easily exploited by a remote attacker. The Log4j exploit is easy to do, and ~3 billion systems globally are exposed. A patch has been released, but most organizations can’t find all instances of Log4j in their code. Completing the patch across all systems is labor intensive and will take a long time. This incident is worse than the 2017 Equifax hack, which cost that company $425M+ in fines.
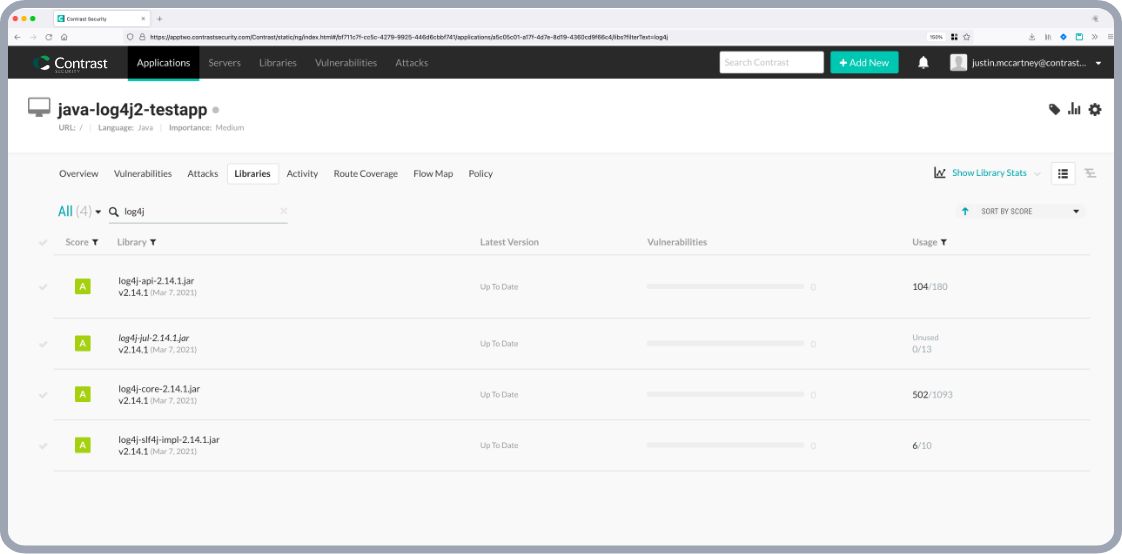
We were able to analyze whether our own built software would be vulnerable to the Log4j zero-day, using the Contrast Secure Code Platform, and got the answer within 30 seconds by just looking at the Libraries menu! How fast is that!
Sandor Incze
CISO

Contrast VS The Log4j2 CVE - a Demonstration
Contrast Security co-founder, Jeff Willams demos the Contrast Secure Code Platform and finds the vulnerability that caused CVE-2021-44228 and stops attacks against it, without updating versions or using a WAF.
Contrast Security Experts Weigh in on the Recent Log4j2 Exploit
Hear from Contrast Security’s Director of Developer Relations, Erik Costlow on what can be done to mitigate the 0-day now, recommended best approaches, and how you can prevent Log4j2 exploitation right now.
The Contrast Secure Code Platform
Is explicitly engineered for security events like the current ongoing Log4j remote code execution vulnerability.
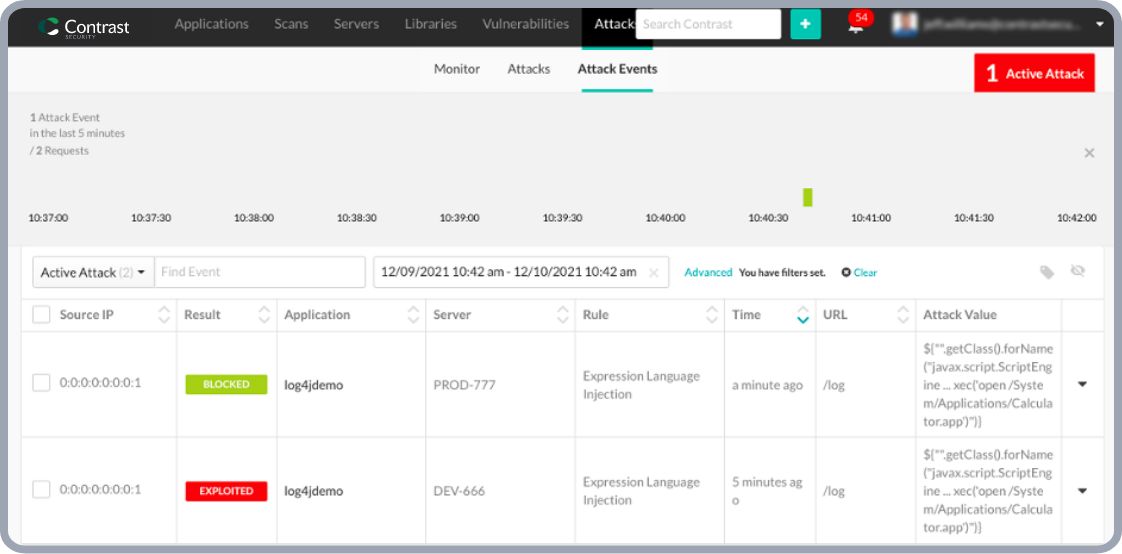
Contrast Protect
Can stop the Log4j vulnerability today, in your production systems, without requiring software upgrades.
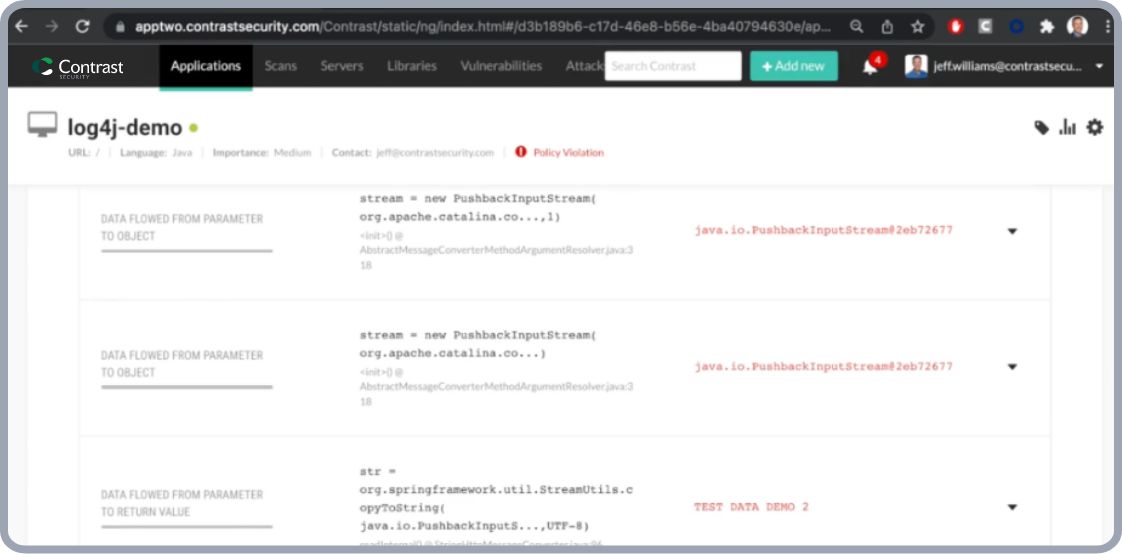
Contrast Assess and Contrast SCA
Enable development teams to find the vulnerability in applications before they’re released to production.
Contrast consolidated everything into a single platform with accurate and fast results that we were not aware of before... As an example, Contrast is protecting us against the recently disclosed Log4j vulnerability without having to patch or update our servers.
Brian Vlootman
CISO

Additional Resources
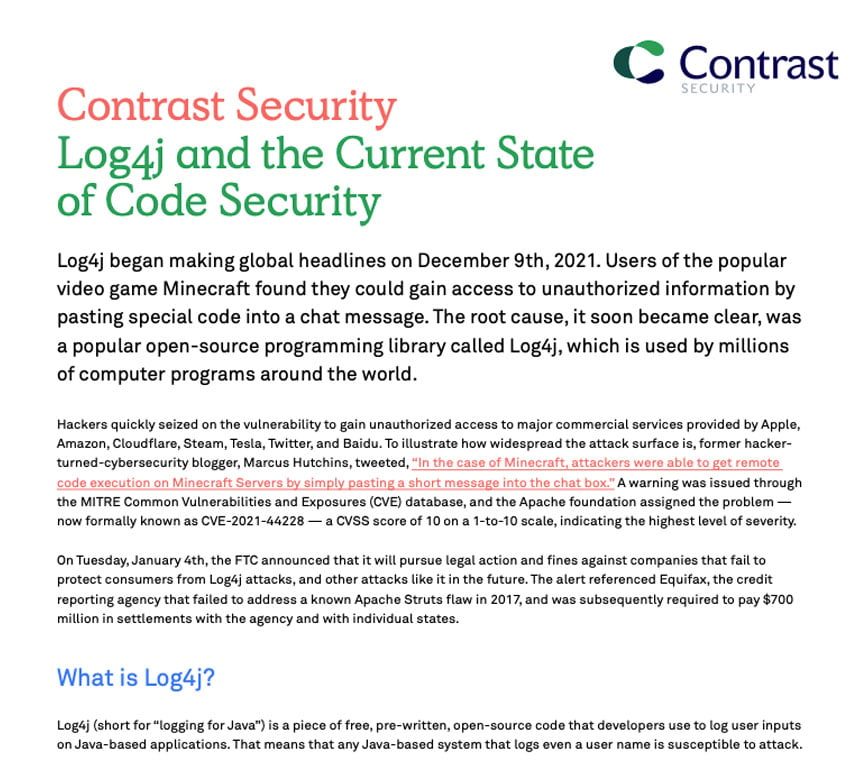
Executive Summary: Log4J and the Current State of Code Security
The Log4J exploit saga has caused many organizations to reconsider their zero-day rapid response plan. Our new executive summary gives a general, easy-to-understand overview of the Log4J vulnerability, how current software security mainstays like SAST, SCA, and WAF fell short in responding to it, and how Contrast was able to quickly identify, contain and protect customers against attacks.

[UPGRADE TO 2.17] UPDATED GUIDANCE ON ADDRESSING LOG4J CVES
This morning, the Apache Software Foundation provided another update to log4j (version 2.17.0) to address a new CVE-2021-45105. Contrast recommends using this most secure version.

EXPRESSION LANGUAGE AND DESERIALIZATION ATTACKS ON THE RISE IN LEAD-UP TO LOG4J VULNERABILITY
It’s been a couple of weeks since the first public disclosure of the Log4j vulnerability. A lot has happened - perhaps the understatement of the year. Several rounds of new patches have been issued from the Apache Software foundation and others as new information about this unprecedented security issue is discovered. We’re now learning about some of the more sinister aspects of this situation with nation state actors exploiting the vulnerability.

THREE REASONS WHY CONTRAST SCA IS BEST SUITED FOR LOG4SHELL RAPID RESPONSE
Tools that present a deluge of irrelevant findings lead security teams to chase their developers to patch libraries that aren’t actually used by their application! In short, in the event of a zero-day incident response scenario, SCA tools need to enable teams to easily identify applications at risk, confirm which of them are actually vulnerable, and provide a quick means to institute some form of protection in place. Enter Contrast and its cross-platform approach to Software Composition Analysis.

LOG4J ON-DEMAND WEBINAR
ON-DEMAND RECORDING AVAILABLE
The most serious of vulnerabilities was just found in the most used logging framework, but DevSecOps teams can quickly identify what’s impacted and where they focus their time.

LOG4SHELL BY THE NUMBERS
We monitor many thousands of applications with Contrast Assess (IAST), Contrast SCA, and Contrast Protect (RASP) so we have a unique data set compared to others and, so far, we have some really interesting takeaways.

UPDATED GUIDANCE ON ADDRESSING LOG4J CVES
The Apache Software Foundation provided updated guidance that the patch to fix Log4Shell (version 2.15.0 and below) was insufficient – a new update (version 2.16.0) fixes these issues.

INSTANTLY INOCULATE YOUR SERVERS AGAINST LOG4J WITH NEW OPEN SOURCE TOOL
Contrast is releasing SafeLog4j, a free and open-source, general purpose tool that can detect/verify vulnerable log4j applications and protect them.
WAF, RASP AND LOG4SHELL
Log4Shell has done an excellent job of making the case for Runtime Application Self-Protection (RASP). Here’s the quick summary: our Contrast Protect customers have been secure against the remote code execution (RCE) in this vulnerability for...
Contrast Security Protects Global Enterprises and Fortune 500 Customers from Log4j Attacks
Press Release - Dec. 17 2021
The Contrast platform secures the world’s largest organizations against applications using Log4j without patching while protecting against future vulnerabilities.
Learn How
Leverage the Contrast secure code platform and service offerings to stop attacks at runtime with Contrast Protect at no charge for a limited time.







