Airport security is a lot like cybersecurity. Each is a cumbersome process aimed at protecting valuable assets. Both involve detection and response. In both airport and cyber security, the approach is to find threats that have made it inside the exterior walls — e.g., detect threats via x-raying luggage at the airport or by uncovering zero-day vulnerabilities in application code in production. Then, respond by blocking the threat, be it by removing forbidden materials from luggage or blocking exploitation of a web application vulnerability by surrounding dangerous functions with trust boundaries.
Detection and response are critical control layers in the cyber defense stack. This article examines how they work and contribute to security posture. In particular, it looks at detection and response as part of Contrast Security’s Application Detection and Response (ADR).
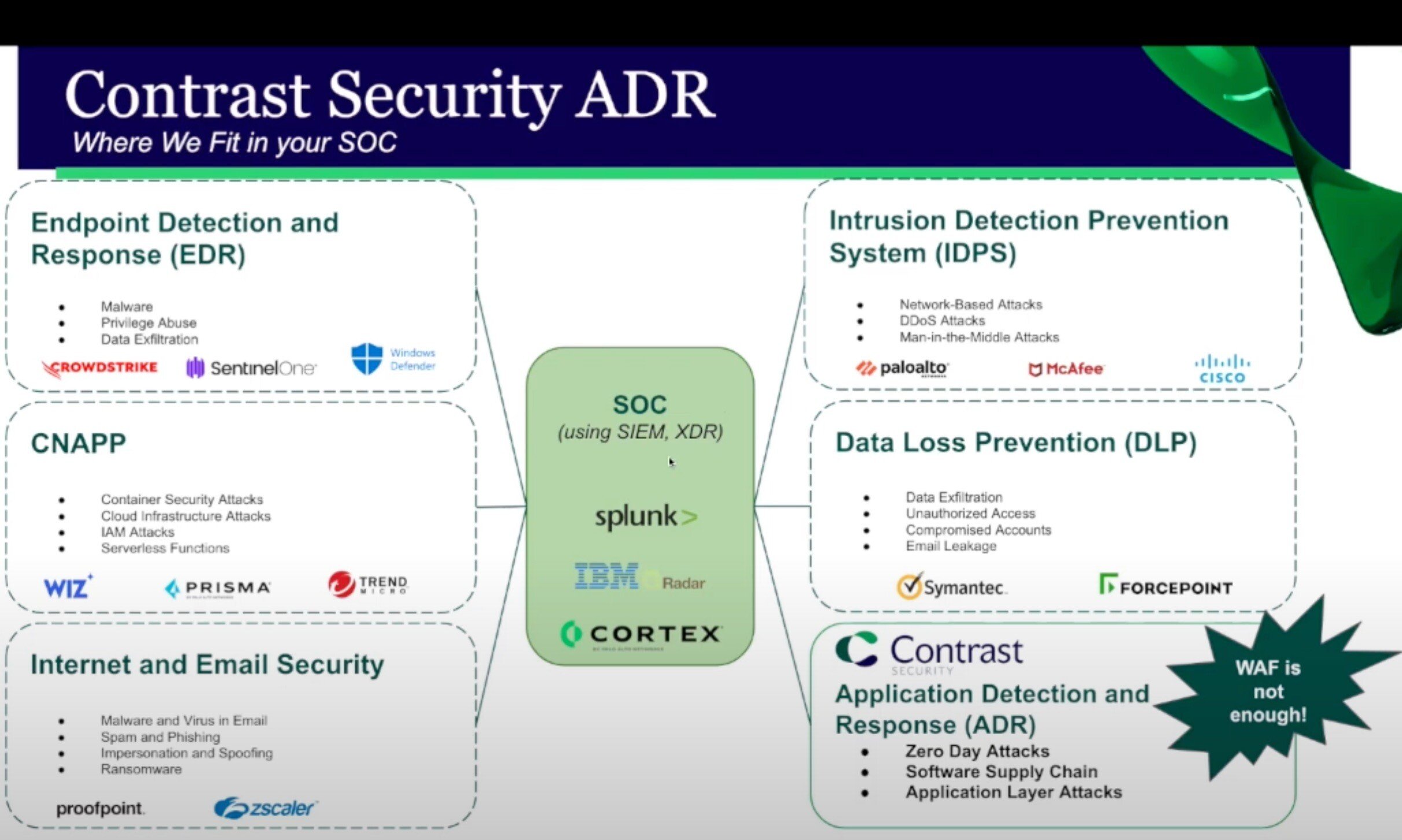
ADR fills the critical AppSec gap left by other detection and response solutions by instrumenting applications and application programming interfaces (APIs) to protect, detect and respond to threats in real time. An ADR solution provides continuous visibility into the security behavior of the entire software stack — identifying anomalies that indicate security incidents and automatically taking action to mitigate these threats using highly contextual feedback to operations and development teams.
What is detection?
The detection control layer is all about finding and analyzing possible cyber threats and evidence of attack. At the airport, detection comes in the form of x-ray machines, bomb-sniffing dogs and observant security personnel. It’s too late to keep the threat off the airport property, but there’s still time to keep it off the planes. ADR similarly operates at the application layer, offering detection that involves continuous monitoring of software in production. ADR constantly searches for software attacks as well as signals of zero-day attacks and other anomalies in the code.
The detection control layer parses a great deal of data to identify indicators of compromise or other adverse events. For example, an SQL injection (SQLi) attack — the attack behind the widely exploited CVE-2023-34362 MOVEit vulnerability — would reveal itself when untrusted data gets passed to a database function.
Contrast tackles the root cause of AppSec issues such as SQLi by automatically introducing security checks into powerful, dangerous functions, like the SQL commands attackers use to craft malicious SQLi. Contrast ADR takes the innovative approach of simply tagging and tracking untrusted data wherever it goes within the application. Contrast ADR’s detect layer also tracks all the validation and escaping that happen to that data along the way. Then, anytime unsafe data gets written to the database, you know if it's an SQLi problem, because ADR’s detection reports both the vulnerability and all its contextualized details.
Specifically, Contrast ADR pinpoints web application attacks down to the exact line of code. Contrast ADR can tell you the line of code that’s being attacked: specificity that’s impossible for a web application firewall (WAF). Unlike WAFs or external scanners, Contrast ADR analyzes and protects applications from within by integrating security safeguards into the running application, thus making it self-protecting.
Check out a demo of Secure from Within application instrumentation
What is response?
If airport security finds a utility knife hidden in a passenger’s coat, it will show up in an x-ray. That’s the detect part of the security process. The response part is when security then detains the passenger and removes the knife. Similarly, if an ADR solution detects a threat, such as a zero day lurking in production code, it “detains the passenger” by forwarding information about the threat to an analyst at the security operations center (SOC) and/or by auto-blocking, depending on how an organization wants to use ADR. Whether ADR is set to block or not, the SOC analyst can enrich the alert by looking up the threat signature.
ADR deployments vary by organization, so no single pattern of response is the norm. Users will configure ADR based on their requirements and priorities. For instance, the threat signature alerting process is often automated, with the goal of sparing the analyst from a manual task.
The response layer includes functions like incident management, threat analysis, threat mitigation and reporting. In some cases, the response layer initiates an incident response workflow, e.g., through a security orchestration, automation and response (SOAR) platform.
This process, sometimes called a “playbook,” could encompass internal and external communications, such as to the legal department.
Response may involve multiple tools working in concert. For instance, ADR can flag a security event and send an alert to an extended detection and response (XDR) solution or SIEM platform for further monitoring of lateral movement by the attacker. Response may also include blocking.
Analysis of the response itself is also often part of the response layer. ADR reports on how well it performed. For example, it measures mean time to respond/remediate (MTTR) and indicates if that time meets a specified service-level agreement (SLA).
Detection and response work together for strong security posture
The detection and response layers are essential for maintaining a strong cybersecurity posture. Like the carefully choreographed interplay between x-ray machines and Transportation Security Administration (TSA) procedures at the airport, they represent vital action steps that defend digital assets against threats. Detection discovers threats. Response deals with them. They go together.
Indeed, it’s not possible to respond to a threat that hasn’t been detected. This is of particular importance at the application layer, where most security tools are not set up either to detect or respond.
ADR offers a solution, enabling the security teams to mitigate threats for software in production.
Read more:






%20video%20screen%20grab.jpg)
