On September 4, 2020, Michael Stepankin published a proof-of-concept (PoC) exploit that took advantage of a fairly new application vulnerability dubbed “Spring View Manipulation.” The Spring View Manipulation vulnerability takes advantage of a recently discovered Thymeleaf Server-Side Template Injection (SSTI) vulnerability using Expression Language Injection. The PoC utilized Spring Boot to show how the vulnerability worked. The PoC allows malicious actors to create a specially crafted Expression Language injection payload to run local system commands. In the case of the PoC, the “id” command was run to return the local system user.
The good news is that Contrast Protect customers are protected from this vulnerability being exploited out of the box.
What Does the Exploit of Spring View Manipulation Look Like?
To confirm the vulnerability, Contrast Labs used the PoC from the Github. The exploit relies on crafting an Expression Language payload into the query string “lang” parameter. An example payload is provided below:

After running the payload with the “id” command against the path action, Contrast Labs was able to return the local user account id. Returning the local user account id showed that we could run code on the local system, thus confirming the Expression Language Injection and remote code execution.
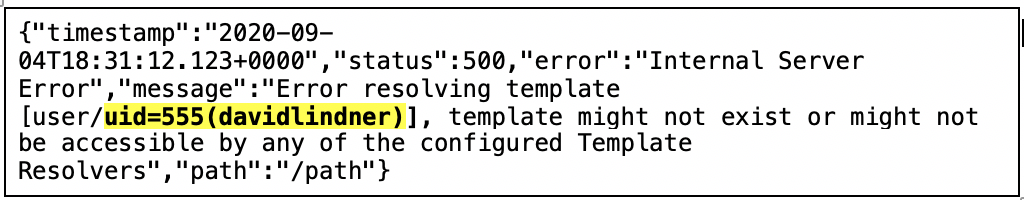
How Does Contrast Protect Block Spring View Manipulation?
Contrast Protect is equipped for out-of-the-box deployment without configuration to detect and block the Spring View Manipulation as it uses Expression Language Injection as the exploit. To show how this works, Contrast Labs’ internal security researchers ran the above-referenced PoC, but this time added the Contrast Protect Java. Once we had the Contrast Protect agent running in block mode, we ran the exploit and saw the following:
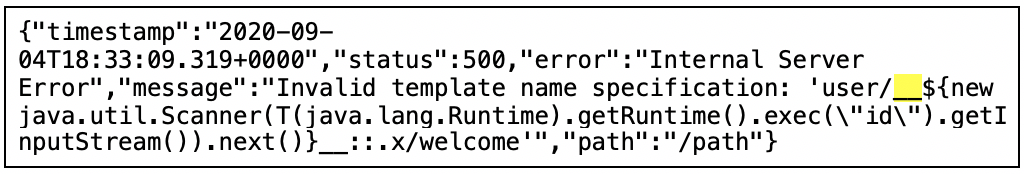
Readers will notice that the above is much different than when the exploit was successful: The “id” command was not run, so nothing was returned to the user. Finally, we browsed to the Contrast Protect UI and saw the detected and blocked attack:
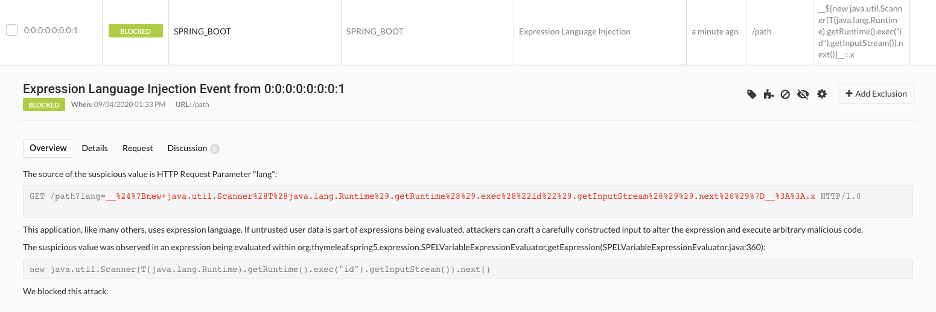
Contrast customers are actively protected from this vulnerability class if Contrast Protect is enabled and blocking mode is enabled for Expression Language Injection. If monitoring mode is enabled, the attack will be detected but not blocked.
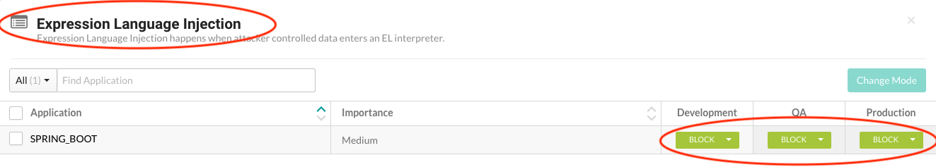
To enable the block mode on Expression Language Injection, users need to navigate in the Contrast Protect user interface to “Policy Management” -> “Protect Rules” -> “Expression Language Injection.” At that point, users need to verify the environment running their vulnerable instance is in “block” mode.
Useful References
Readers seeking more information on the Spring View Manipulation vulnerability can leverage the below links:
- GitHub: Click here
- Thymeleaf SSTI: Click here
In addition, readers without Contrast Protect can get more information by downloading a copy of our solution brief, “Contrast Protect with Runtime Application Self-Protection (RASP).”













