Monitoring the Security of a Running
Application has Been a Guessing Game
Until recently, we knew little to nothing about the security state inside a running application – unless developers built in custom logging. Without security visibility, security pros would typically:
- Hope the developers wrote secure code
- Harden the platform (e.g., OS, server, container) the application is running on and hope nothing gets through
- Deploy an edge device (e.g., IPS, WAF) and hope blocking suspicious traffic is sufficient
- Hope your SOC finds the attack in time
- Hope that your incident response team can respond effectively
- Hope you have talented enough software engineering resources to fix an exploited vulnerability in code
Enter Application Security Monitoring
The advent of runtime instrumentation offers IT Operations and Security teams unprecedented visibility and control over the security of the application layer. Operations teams already use similar tools for monitoring performance of the running application: Application Performance Management (APM) solutions such as AppDynamics, New Relic or Dynatrace. These telemetry products use an agent based technology to instrument the running application and measure performance metrics.

Security teams can now extend that technology to monitor the security of the running application.
Key Questions to ask when evaluating ASM solutions:
- Do you know enough about an attack while it’s happening?
- Can you distinguish between an attack or a probe?
- How much time do your teams spend resolving false positives?
If using an edge solution:
- How long did it take you to set up your edge device?
- How often do you update your rules?
- How does your deployment change when your apps scale or move around?
- How much does it cost to add an extra device?
To see how Contrast Protect may fit your Application Security Monitoring needs, please continue reading.
Contrast Protect – Best in class Application Security Monitoring
With Contrast Protect, you get unprecedented visibility
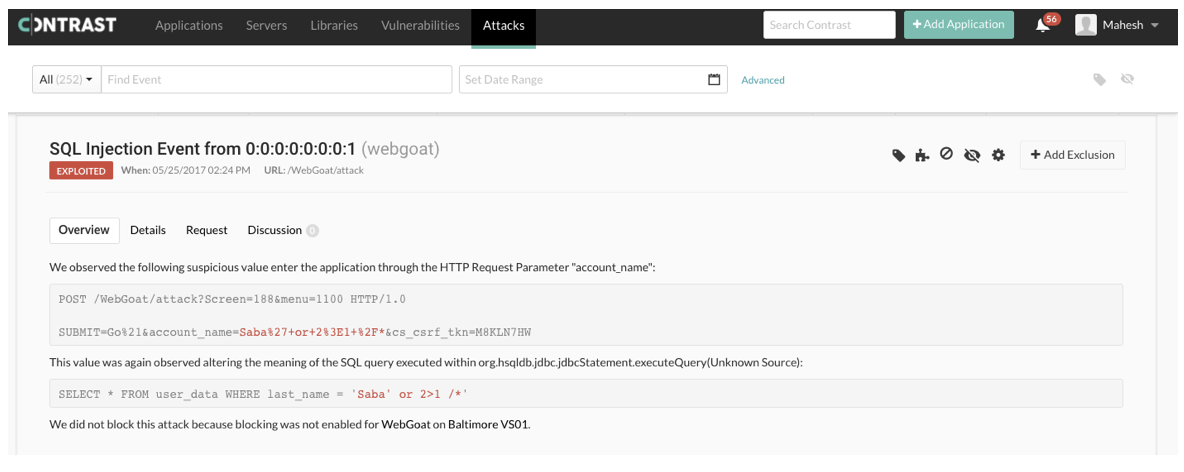
Contrast Protect’s patented deep security instrumentation allows it to go deeper into the application stack. This allows you to (1) protect the full application stack, (2) gather detailed information about an attack as it happens and (3) block the attack instantly. For each attack, Contrast sees:
- Full HTTP request
- Stack trace (including lines of code)
- Targeted web page/folder
- Targeted server
- Attack vector details
- Attacker IP address
- Application account associated with attack
- Attack specific data (not exhaustive):
- XSS: HTTP response data
- SQLi: Full database query
- Path Traversal: Full file path
- Padding Oracle: Exception details
- Command Injection: OS command
- Remediation guidance
- Time of event
- Rate of attack
- Severity of attack
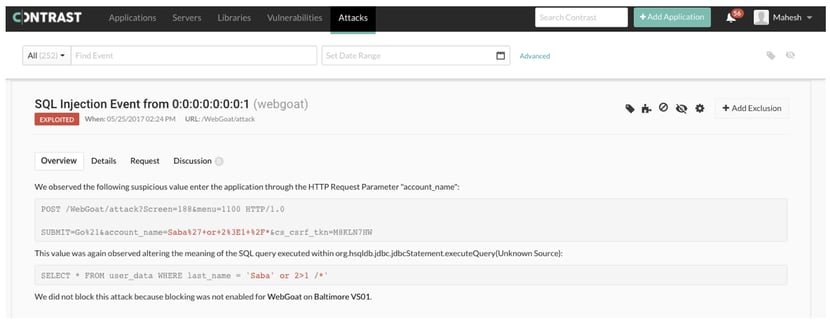
Figure 1: Contrast Protect – Attack Event Overview
In addition, instrumentation enables Contrast Protect to distinguish between probes and real attacks / exploitation attempts. These events can be sent to monitoring / SIEM solutions of choice using different syslog levels.
With Contrast Log Enhancement, monitor anything inside the application
As mentioned above, Contrast Protect monitor mode has standard attack and event logging that provides unprecedented visibility. However, Contrast Protect Log Enhancement extends this capability into the inner workings of application and user behavior. Log Enhancers enable users to log anything in an application and send that data to your log management or SIEM system of choice. Log in failures, privilege escalation, specific database calls and many other aspects of the application environment can be logged and used for correlation to identify indicators of compromise. Contrast seamlessly integrates into any existing monitoring infrastructure. This allows operations teams to leverage this newly available intelligence into their own systems instead of adding another screen or dashboard.
Contrast Protect provides best in class performance among current solutions. Protect was designed to be fundamentally more efficient (and secure) through deep application level instrumentation. While most edge device vendors typically have per request performance impacts in the 10-100ms range, Protect only adds 0.05ms (50 microseconds).
This performance testing was conducted by Contrast Labs, Contrast Security’s research arm, to measure the overhead of Contrast Protect on applications in normal, moderate attack and heavy attack scenarios.
In conclusion, if you are looking to optimize for performance when looking to secure your application production environment, Contrast Protect has demonstrably minimal impact.