On August 25, Atlassian released security updates to address a remote code execution vulnerability (CVE-2021-26084) affecting some versions of Confluence’s team collaboration server software. As of September 3, mass exploitation of the CVE was being detected in the wild—prompting the Cybersecurity & Infrastructure Security Agency (CISA) to issue a warning for users to immediately update systems. A USCYBERCOM Cybersecurity Alert specifically recommended not waiting until after the Labor Day weekend to take action.
In a nutshell, the vulnerability could be exploited by an attacker to bypass authentication and inject malicious Object-Graph Navigation Language (OGNL) commands. This carries a very high-risk exposure—one with a CVSS score of 9.8 out of 10. The pre-auth nature of the vulnerability itself and the fact that there are a lot of older, unpatched, on-premises versions of Confluence floating around make this a serious problem.
What Does the Exploit Look Like?
CVE-2021-26084 is an OGNL injection vulnerability that allows an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance.
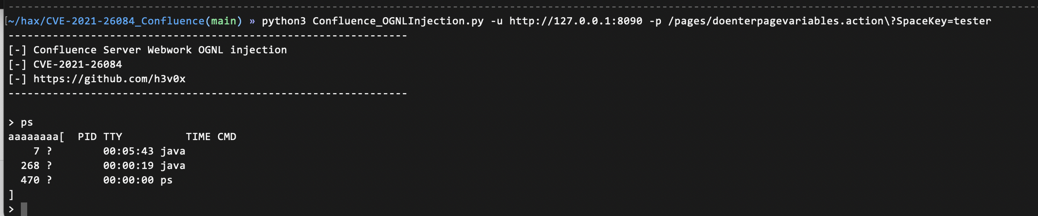
Confluence Server OGNL injection (CVE-2021-26084)
An attacker can exploit this vulnerability—easily bypassing web application firewall (WAF) defenses—to take control of an unpatched system. When this happens, an attacker gains “godlike” access to Confluence. They can access anything else stored on that box—including data, tickets, attachments, and keys to things like AWS infrastructure. Lateral movement beyond the server, across the network and other applications, is even possible.
Has the Confluence Vulnerability Been Patched?
The vulnerability was discovered in late July by a researcher participating in Atlassian’s public bug bounty program. Thus, about a full month passed between the original discovery of the CVE to when it was publicly disclosed and patches were released. As is often the case, the critical window for CVE-2021-26084 came after the August 25 announcement. Nine days after Atlassian released its patches for vulnerable Confluence systems, large numbers of attacks were still occurring around the world. Once attackers are tipped off about a CVE, it becomes a race against time to get all the affected systems patched. Even then, rare instances still exist where patches can also be compromised.
How Contrast Provided Automatic AirCover for Customers
With this particular vulnerability in Confluence, there were really two major windows of risk exposure. First, even while the vulnerability remained an unknown threat to the public and the risk of an attack was low, a bot or hacker might stumble upon the opportunity and take advantage. Second, after the CVE announcement, but before patches could be installed, the likelihood of an attack skyrocketed—with the period between patching and exploit becoming a race against time. To make matters worse, a public exploit code was released on September 1. As this CVE is an example, the time frame between vulnerability detection and notification and patching can be significant. It can take days or sometimes even weeks—depending on the severity of the problem, the availability of developers and security staff, and other concurrent projects/problems/organizational change processes.
But this is precisely where Contrast customers have an advantage over organizations using WAF-only defenses. With CVE-2021-26084, Contrast Protect’s OGNL protection rule automatically spotted and blocked these attacks—right out of the box.
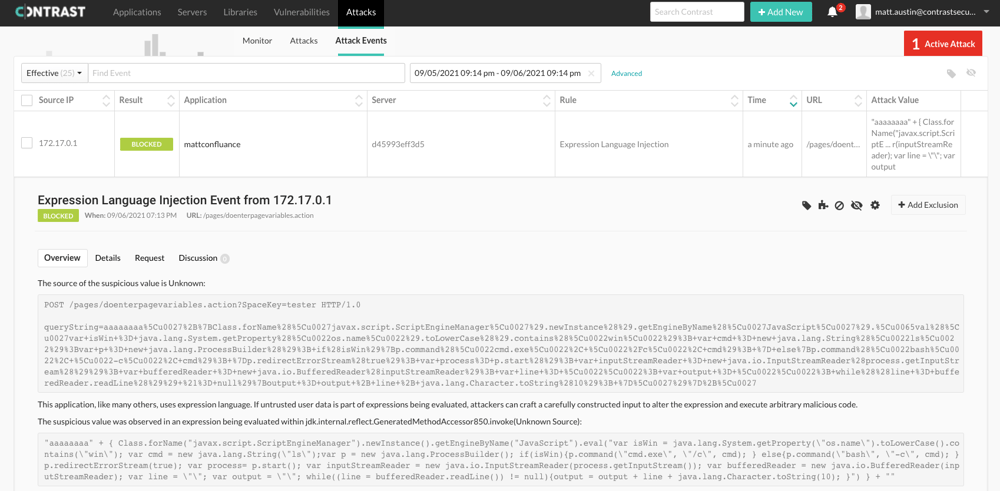
Contrast Protect blocks CVE-2021-26084 attacks (Contrast dashboard)
Unlike a WAF that benefits from known CVE signature detection at the application perimeter, Contrast instrumentation works inside the application. This internal visibility allows Protect to observe what’s happening in the application runtime and prevent exploitation in real time, as the attack takes place. In the event an attacker targets an unknown or newly disclosed vulnerability and bypasses a WAF, Contrast provides aircover to automatically block attacks.
Watch a video walkthrough of how Contrast Protect blocks CVE-2021-26084 attacks
The Need for Complementary Application Security
While no organization has admitted yet to a major breach due to a successful exploit of CVE-2021-26084, widespread detections of public exploits and honeypots have been—and continue to be—reported. For example, an infrastructure team at Jenkins identified a minor example of a successful attack against a deprecated Confluence service.
This is another example of a popular software tool introducing significant risk. The more ubiquitous the tool, the bigger the opportunity for mass exploitation from attackers staging widespread, automated attacks. While WAFs provide necessary protection against known vulnerabilities, they cannot provide the comprehensive protection required in a world where bad actors constantly probe applications for vulnerabilities and can execute malicious, targeted attacks in near real time once CVEs and corresponding patches are revealed. Modern application security requires layers of protection—and the best defense for applications in production combines traditional WAF deployments with Contrast’s instrumentation-based approach.
For a quick overview of the Confluence CVE and how Contrast protects against it, make sure to download our Fact Sheet (“Confluence CVE-2021-26084: What You Should Know”).
Other Resources
Fact Sheet: Confluence CVE-2021-26084: What You Should Know
Solution Brief: Contrast Protect: Runtime Application Protection and Observability
Video: Protection for Confluence CVE-2021-26084 with Contrast Protect








