Applications are perpetually accosted by hackers intent on doing harm to your business. They'll dig and look under the covers for any exploitable entry point they can find. At the same time, development teams struggle to deal with a backlog of unremediated application vulnerabilities, especially if they’re using inaccurate legacy scanning tools.
Contrast Protect was created in response to these issues. We recognize that it is virtually impossible to create applications that are completely free of vulnerabilities. The Protect agent uses instrumentation to defend applications from the inside, preventing vulnerabilities in custom code or third-party libraries from being exploited. However, when monitoring malicious activity, it’s important to remember that your web application is only part of the stack. The application runs on a server, and that server is on a network. As a result, it is difficult and inefficient to monitor each individual layer in isolation.
To help address this problem, many organizations use a security information and event management (SIEM) tool to monitor events received from their security and operational technologies. A SIEM tool centralizes logging and monitoring to help security teams analyze trends and find signals among millions of security events. In the past, I struggled to get excited about SIEM tools—that is, until I learned about a relatively new entrant to the SIEM market: Microsoft’s Azure Sentinel.
Microsoft Azure Sentinel Integration With Contrast Protect
Azure Sentinel has been making waves since it became widely available in late 2019. Sentinel was launched with built-in support to harvest data from a plethora of Azure cloud services. Given Microsoft’s scale, threat intelligence, and computing power, it’s no surprise that Azure Sentinel has gone from being a new entrant to a leading solution in just two years.
What excites me most about Azure Sentinel is how it extends to visualize data—specifically, how it can automate actions from security events. Essentially, Azure Sentinel is both a SIEM and a security orchestration, automation, and response (SOAR) solution—and this is an exciting blend for Contrast Protect users.
Azure Sentinel also makes it very easy for users to consume events from almost any source, including our very own Contrast Protect agent, in common event format (CEF). The Contrast Protect agent sends threat data directly to Azure Sentinel, where it can then be used to create visualizations of attacks, automate incident creation, and even trigger automatic responses based on defined criteria.
Contrast wraps up all of this functionality into a package that is published to the Microsoft Azure Marketplace. It takes only a few clicks to install Contrast Protect With Azure Sentinel and to start receiving live attack events from your applications using the Contrast Protect agent.
How Does the Joint Solution Actually Work?
Let’s start with the attack visualizations. Azure Sentinel visualizes data in the form of workbooks and can present data in a variety of formats. (Microsoft has done an amazing job of making this simple and easy to customize.) The Contrast Protect workbook already includes some visualizations that highlight commonalities in the events received; however, if you want to customize these visualizations, you can do so. You can literally edit the workbook by adding, modifying, or removing components until you get the visualization that you need.
Here are some examples of the components in the workbook, including attacks by outcome, by rule, or by application.
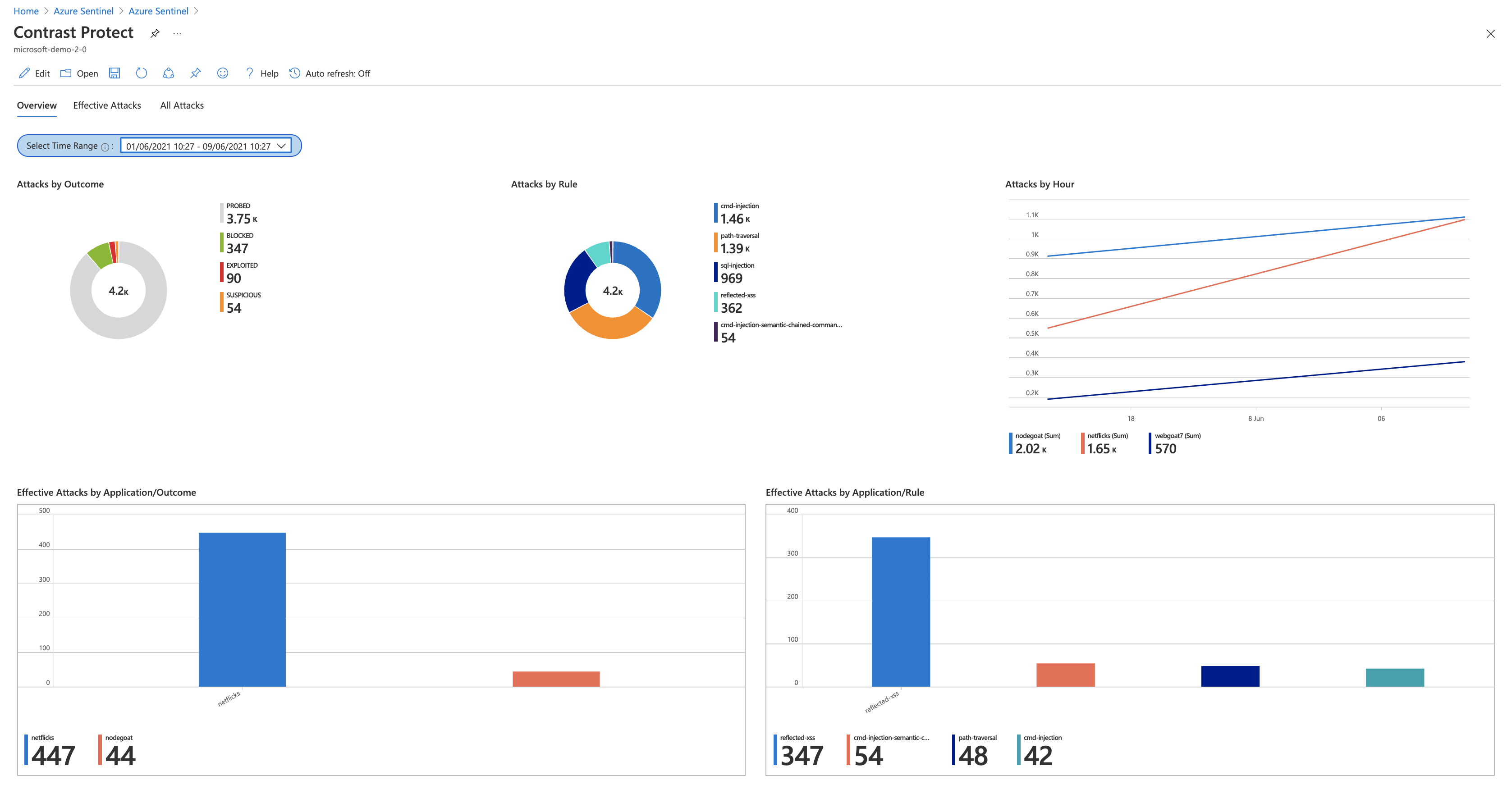
Workbook: Components include attacks by outcome, rule, or application
But this high-level view is just a starting point. You can also dive into the details. Contrast Protect users already know that Contrast distinguishes between an ineffective attack (i.e., a probe) and an effective attack (i.e., an exploit). To be clear, if you’re seeing data in the effective attacks grid, then you should be concerned; it means an attack has reached a vulnerable part of the application.
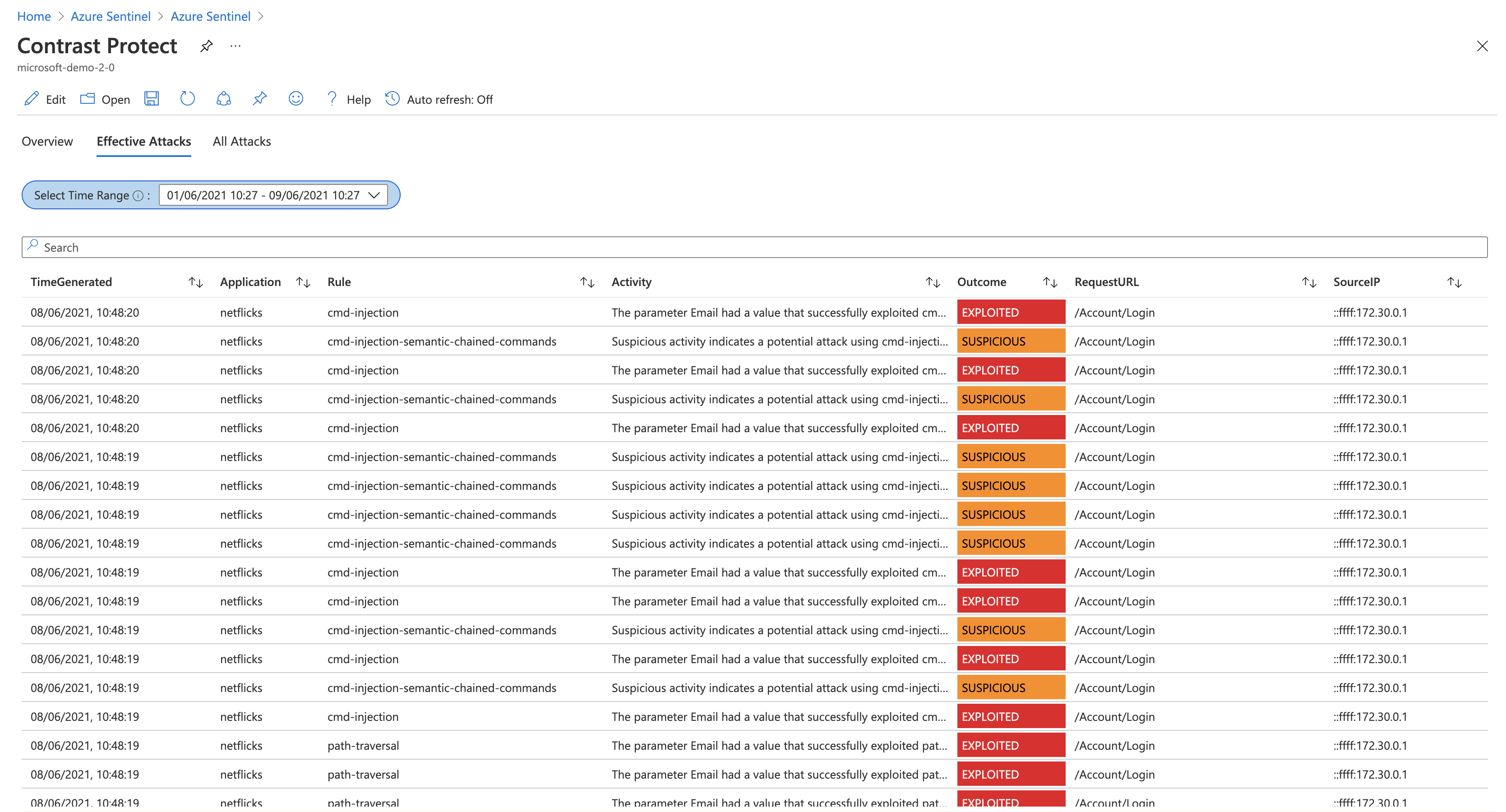
Contrast Protect: Effective attacks view
Analytics rules
Given that the Contrast Protect agent can determine that the application is being exploited, we can be more proactive and trigger an incident in Azure Sentinel for the security team to investigate. Azure Sentinel generates these incidents from analytics rules, which are mostly designed for dealing with large volumes of events. In consultation with Microsoft, Contrast concluded that a single exploit event from Contrast Protect is worth investigating. As a result, it was determined that we should ship some analytics rules out of the box—tailored to specific types of events.
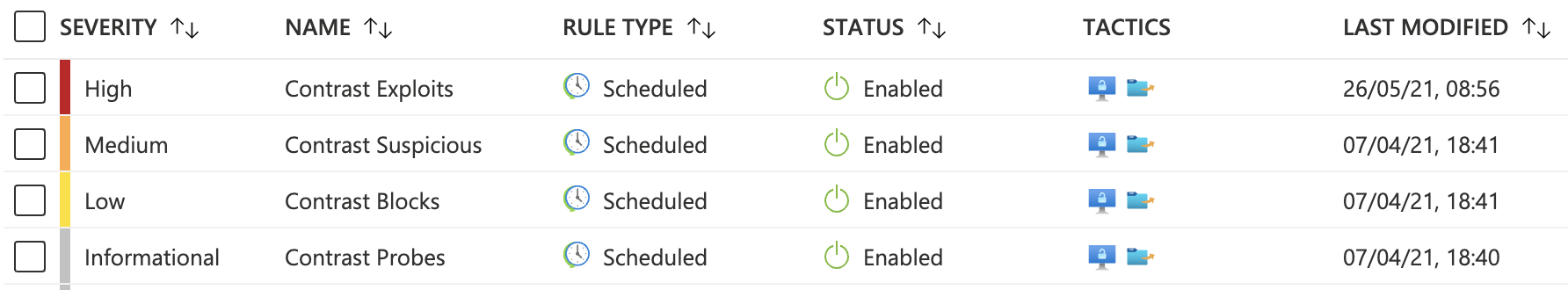
Contrast Protect analytics rules
Just like workbooks, analytics rules can be easily customized. Users can decide to create incidents based on their own criteria such as the severity, frequency, and volume of incoming events from Contrast Protect. The rules work by generating an incident (like a ticket) that can be assigned to a member of the security team for review.
The incident displays data from the attack and correlates this data with events you receive from other security or operational systems. For example, if an attacker had conducted some recon before attacking your web application (such as a port scan), Sentinel can link these events together to provide more intelligence on the attacker’s activity.
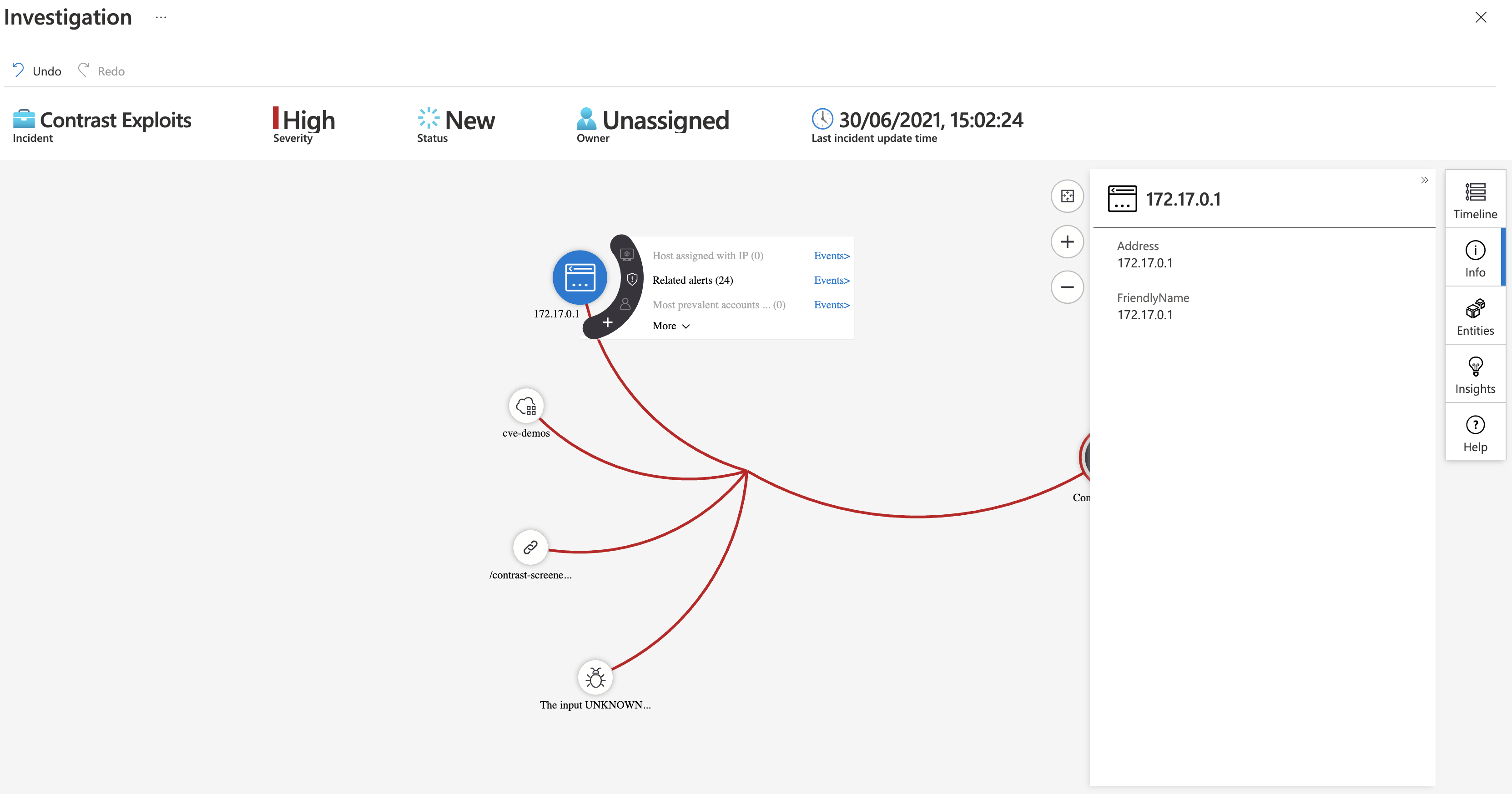
Sentinel provides an intelligent view of coordinated attacks
Automated responses to attacks
This brings me to perhaps my favorite part of Azure Sentinel: the response options. Azure Sentinel allows you to create threat responses that trigger either manual or automated defensive actions. The automated responses are triggered by analytics rules and they take the form of Azure Logic Apps. Let’s explore how these are generated and how they can be used.
Building logic apps for automated responses in Sentinel
Picture for a moment that the Contrast Protect agent sees an attack on one of your applications. These attack events stream into Azure Sentinel, enabling you to build logic apps to decide the actions you would like to take in response to the threat. For example, perhaps you want to block this IP from reaching any of your applications. In this case, you can build a logic app. In another instance, you might want to add this IP to a database of known offenders or cross-check to see if it comes from a botnet. Or maybe you want to provide an easy WHOIS lookup of all IPs for the SOC team. In each of these cases, Sentinel would guide you through the process of building the necessary logic app for the desired security response.
Holistic Reduction of Application Risks in Production
Contrast Protect is the only runtime application protection and observability partner in the Azure Sentinel solutions program. This integration delivers an easy-to-deploy and easy-to-operate solution that helps organizations reduce outstanding application vulnerability risks.
Best of all, the Contrast Protect/Azure Sentinel joint solution is available today, so why not go ahead and install it. We look forward to your feedback!
To learn more about this integration, be sure to read the Contrast Protect With Azure Sentinel joint solution brief.













