What Does PCI DSS Compliance Mean?
 In 2004, Visa, MasterCard, Discover, American Express, and JCB combined their minimum security standards for credit card processing together and crafted the Payment Card Industry Data Security Standard (PCI DSS). This ensured that merchants met minimum security standards when they stored, processed, and transmitted cardholder data. Updated through the years, the current standard is version 2.0 which contains 12 specific requirements for merchants to be considered compliant. (Note: In January 2014, version 3.0 takes effect.)
In 2004, Visa, MasterCard, Discover, American Express, and JCB combined their minimum security standards for credit card processing together and crafted the Payment Card Industry Data Security Standard (PCI DSS). This ensured that merchants met minimum security standards when they stored, processed, and transmitted cardholder data. Updated through the years, the current standard is version 2.0 which contains 12 specific requirements for merchants to be considered compliant. (Note: In January 2014, version 3.0 takes effect.)
No merchant wants to compromise the security of their clientele. They want to be compliant. They want to be secure. They want their customers data to be safe. But sometimes PCI DSS requirements can be taxing on resources and manpower. Imposed requirements often are, well, imposing. That’s where Contrast Assess comes in. Contrast Assess can help you with two major components of that standard, both related to systems and applications.

Develop and Maintain Secure Systems and Applications
Requirement number 6.5 on the PCI DSS Requirements List, pages 38-43, is designed to help merchants ensure security of their proprietary computer programs and software applications. It helps make sure they are meeting the minimum standard, to be sure, but to be truly secure you'll probably need to do more than what they are asking. Either way, it isn't as easy as a check mark in a box. It requires merchants to "Develop applications based on secure coding guidelines..." and prevent common coding vulnerabilities, including:
- Injection flaws, particularly SQL injection, OS Command injection, LDAP and XPath injection flaws
- Buffer overflow
- Insecure cryptographic storage
- Insecure communications
- Improper error handling
- All "High" vulnerabilities identified via processes established to discover security vulnerabilities
- Cross-site scripting
- Improper access control
- Cross-site request forgery
That's a long list, and it's just the tip of the iceberg if you've got aging applications undergoing constant code reviews and updates. Requirement 6.6 states, "For public-facing web applications, address new threats and vulnerabilities on an ongoing basis and ensure these applications are protected against known attacks...." In addition, the standards expect you to regularly test security systems and processes.
Regularly Test Security Systems and Processes
Requirement numbers 11.2-11.5 on the PCI DSS Requirements List, pages 61-63, are designed to ensure merchants regularly test security systems and processes. After all, new hacks, new threats, and new vulnerabilities are being discovered on a continual basis. To ensure security controls continue to reflect on the changing environment, components, processes, and custom software should be tested frequently. Merchants can do this in many ways. The requirements list includes the following:
- Run internal and external network scans at least quarterly
- Run internal and external vulnerability scans at least quarterly
- Run internal and external scans after significant change in the network
- Perform external and internal penetration testing at least once a year
- Perform external and internal penetration testing after any significant infrastructure or application upgrade or modification, including network-layer penetration tests & application-layer penetration tests
- Use intrusion-detection systems, and/or intrusion-prevention systems
- Keep all intrusion-detection and prevention engines, baselines, and signatures up-to-date
And the list keeps on going. Lots to check off the list, and lots to stay on top of. So what's the best way to stay on top of all of the requirements in the PCI DSS list? That's for you to decide. But we'll put in our two cents anyway because Contrast is entirely scalable, constantly monitoring, and wildly affordable.
Four Ways Contrast Can Help You With Your PCI DSS Compliance
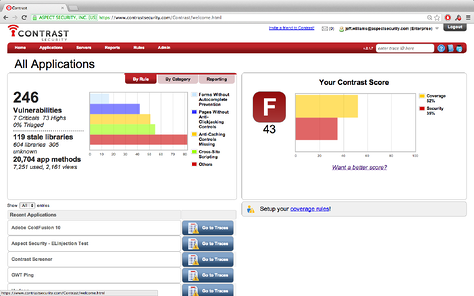
That's an image of the Contrast Assess dashboard. It lets you quickly know the type and severity of vulnerabilities. And it shows you where in the code you are experiencing the insecurity so you can fix it quickly. Because Contrast doesn't give false-positive results, you can spend your time fixing what needs to be fixed instead of chasing ghosts. In addition:
- Contrast provides continuous status of security of application and supporting components rather than snap-shot in time
- Contrast helps you avoid the effort of scheduling testing, interruption to development team, etc. because you can use Contrast to create a PCI application security report anytime
- Developers can fix vulnerabilities as they are found which reduces remediation costs and avoids the pre-audit push
- Contrast provides coverage details to ensure security testing is achieving reasonable coverage – including libraries
We've dedicated ourselves to making your life, your work, easier and more manageable. Give us 30 minutes to give you a live demonstration of what Contrast can do for you and by this time next year, you'll be glad you did.
Thanks for reading.


.jpg)







 In 2004, Visa, MasterCard, Discover, American Express, and JCB combined their minimum security standards for credit card processing together and crafted the Payment Card Industry Data Security Standard (PCI DSS). This ensured that merchants met minimum security standards when they stored, processed, and transmitted cardholder data. Updated through the years, the current standard is version 2.0 which contains 12 specific requirements for merchants to be considered compliant. (Note: In January 2014, version 3.0 takes effect.)
In 2004, Visa, MasterCard, Discover, American Express, and JCB combined their minimum security standards for credit card processing together and crafted the Payment Card Industry Data Security Standard (PCI DSS). This ensured that merchants met minimum security standards when they stored, processed, and transmitted cardholder data. Updated through the years, the current standard is version 2.0 which contains 12 specific requirements for merchants to be considered compliant. (Note: In January 2014, version 3.0 takes effect.)

