OWASP Top Ten Most Rampant Vulnerabilities
|
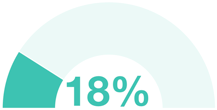
#5 Broken Access Control - affects
Broken Access Control combined two previous OWASP Top 10 from the 2013 list: Insecure Direct Object References and Missing Function Level Access Control. Together, this category represents flaws and gaps that allow an attacker to act as users or administrators of the application.
|
 |
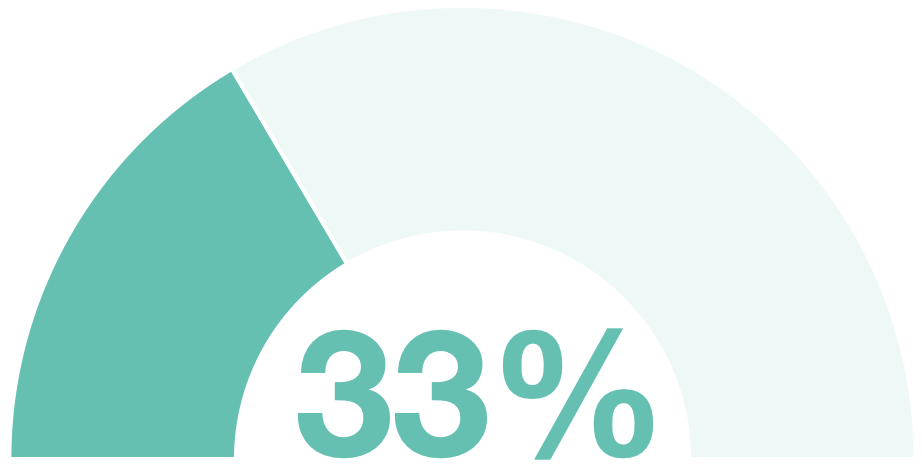
#4 Injection - affects 25% of applications
Injection vulnerabilities allow malicious inputs into an application. They lead to 4 out of the top 10 most prevalent attack types: OGNL, Expression Language, Command, and SQL injections. During an injection attack, untrusted inputs, or unauthorized code are “injected” into a program, which are then interpreted as part of a query or command.
|
 |
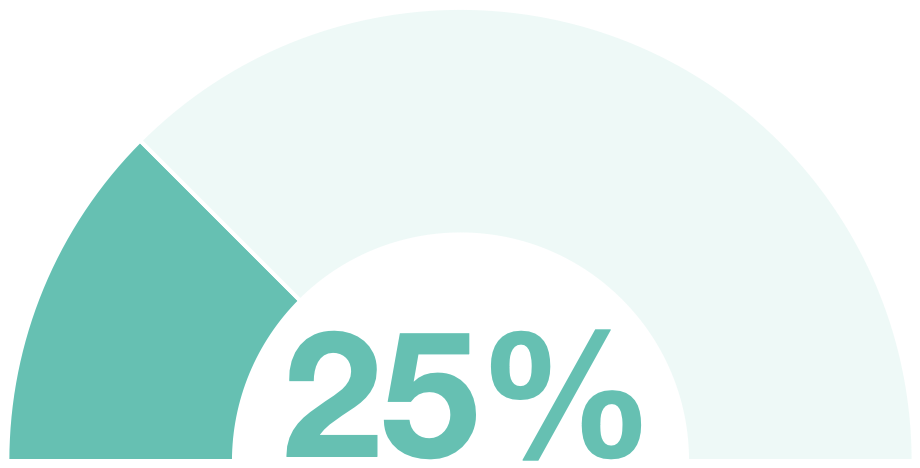
#3 Broken Authentication - affects 33% of applications
In 2017, this vulnerability affected 41% of applications. Due to poor design and implementation of most identity and access controls, the prevalence of broken authentication is widespread.
|
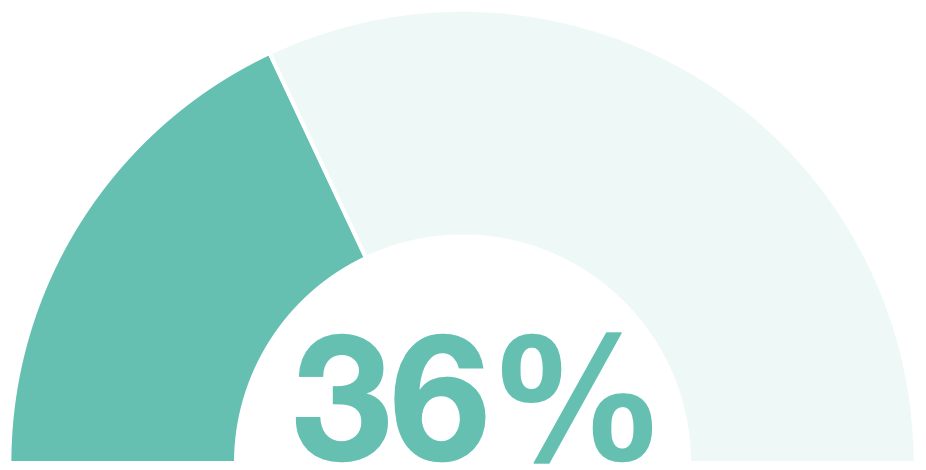 |
#2 Security Misconfiguration - affects 36% of applications
Security Misconfiguration can happen when there is a failure to implement all of the security controls securely for an application. It can happen at any level of an application stack including the platform, web server, application server, database, framework, and custom code. It currently affects the same proportion of applications as it did in 2017.
|
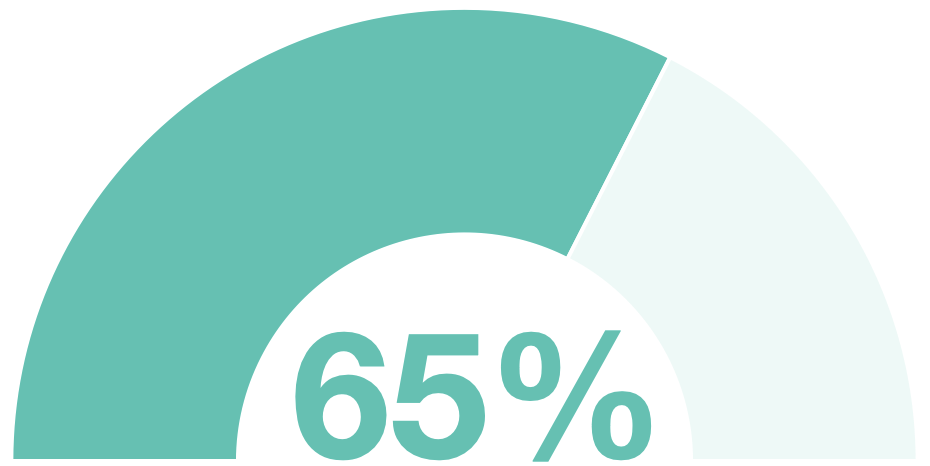 |
#1 Sensitive Data Exposure - affects 65% of application
The top vulnerability in 2017 (affecting 69% of applications) remains the most rampant in 2019. The importance of encrypting both web traffic and sensitive data in storage cannot be underestimated. This vulnerability is limited to flaws that put sensitive data at risk of being exposed or stolen. The potential impact of a hacker accessing this information is massive. Development teams should focus on creating a unified strategy to identify sensitive data and encrypt it wherever it goes.
|
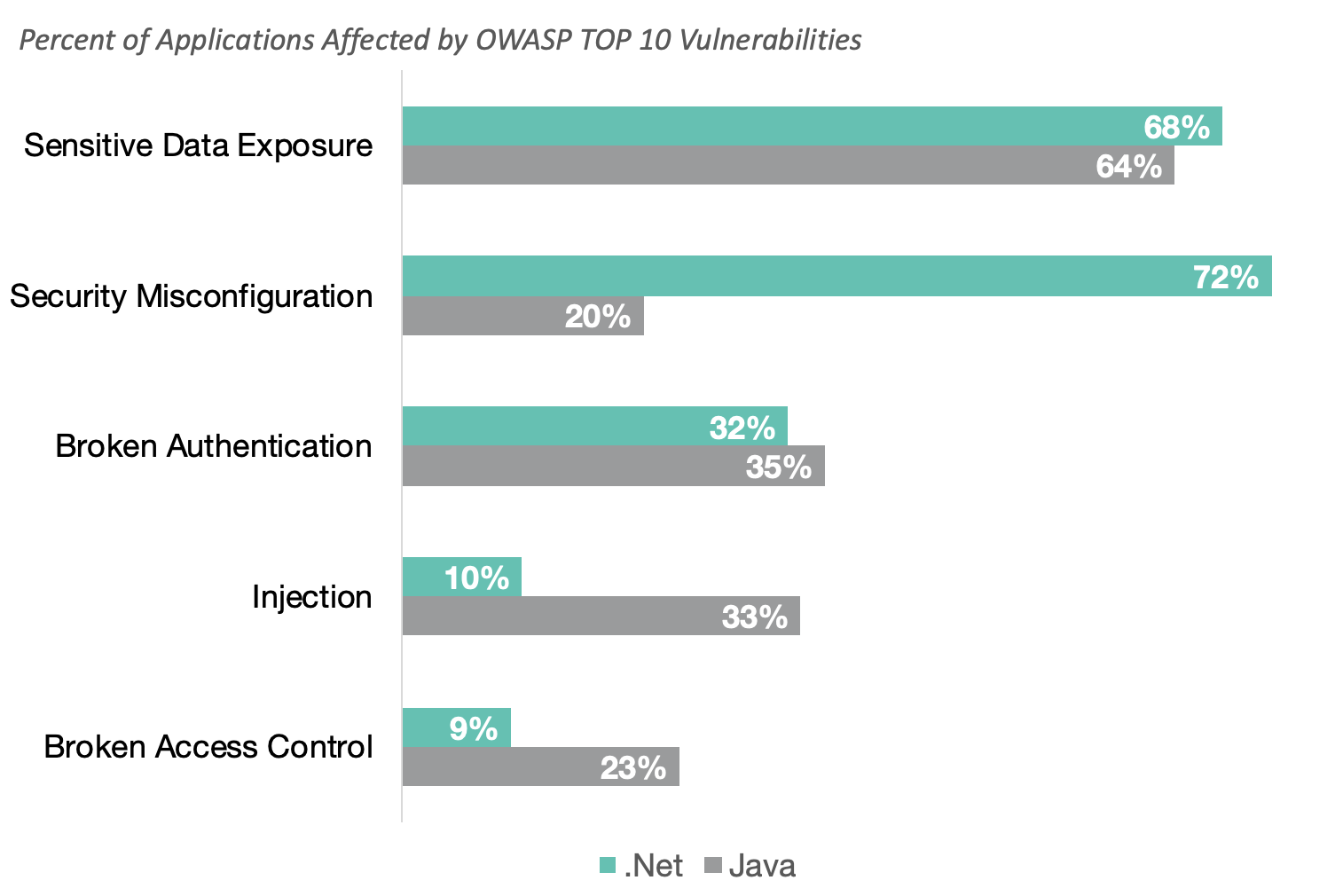
OWASP Top Ten Vulnerabilities By Application Language
To dissect the trends further, Contrast Labs compared the OWASP top 10 vulnerabilities across two of the most popular web application development languages. There was minimal movement in these metrics over the last two years.
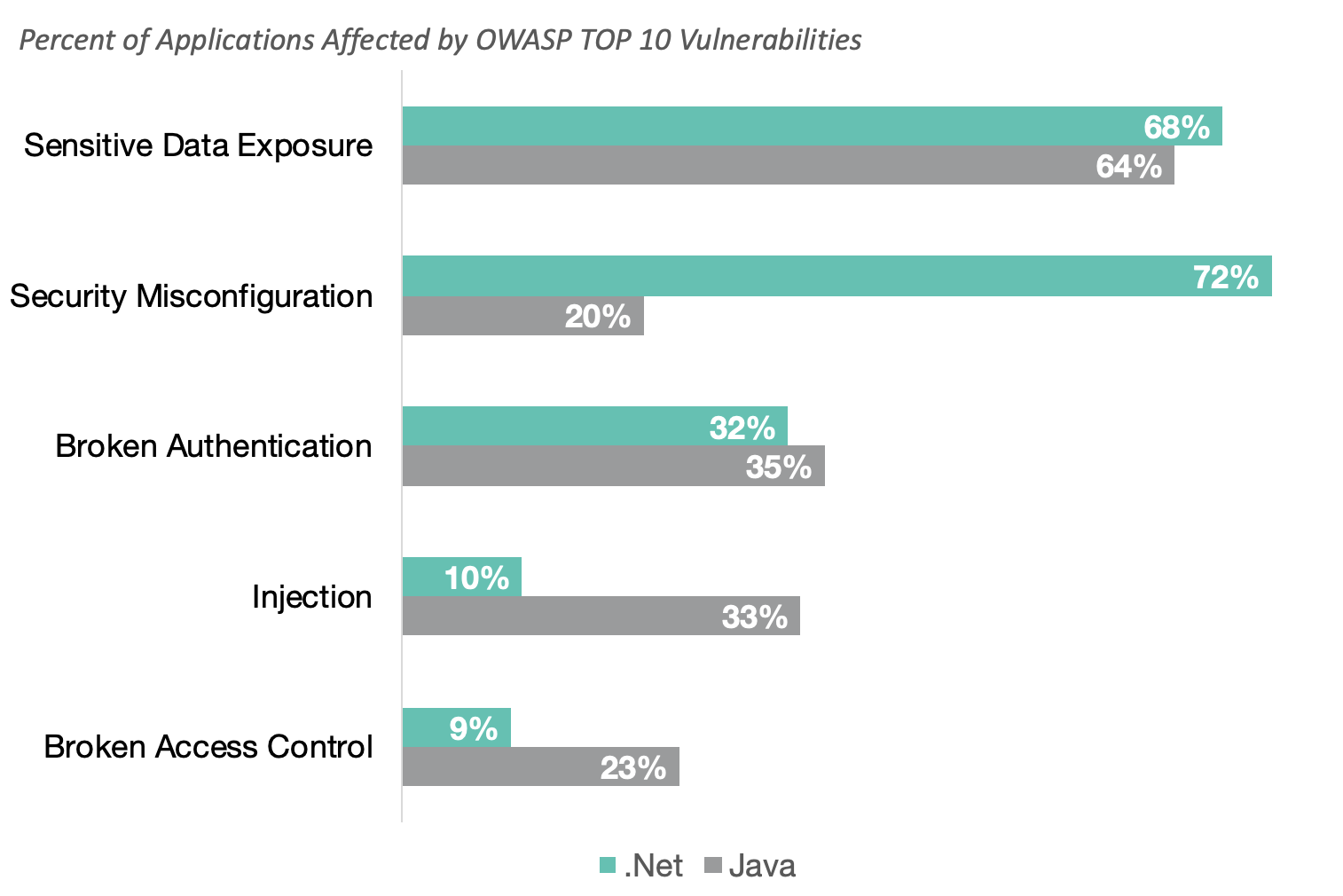
The definition of insanity is doing the same thing over and over again and expecting different results. None of the vulnerabilities above are new. We must enable everyone across the software lifecycle to perform security testing within their normal workflow. By identifying and reporting results in real-time, Contrast Assess provides accurate results to everyone, empowering each person responsible for the app to be responsible for its security as well.