Since the advent of static analysis tools around the year 2002, there hasn't been much innovation in the automation space in application security. Contrast represents a completely new approach to finding vulnerabilities and much more. Gartner recently positioned Contrast in the "Visionary" Quadrant of their latest "Magic Quadrant Report for Application Security Testing." This article was written during the Duke's Choice Award process and describes how Contrast works.
The AppSec Bottleneck
In the past, application security tools either scanned the source code or dynamically scanned the web interface. These tools were designed for experts in application security, took days or weeks to use, and generated huge numbers of false alarms. Many organizations are stuck with large application portfolios that they can't get secure because their expert-based approach is a frustrating bottleneck.
"You have something better?" It happens that we do!
Contrast Works Differently
Because Contrast is passive, drop-in tool, it doesn't require the use of experts. And because Contrast works inside your running applications, it has unprecedented access to security relevant information, making it exceptionally accurate. All this means that ordinary developers can find their own vulnerabilities and fix them before they even check in their code. This in turn eliminates the bottleneck and allows teams to produce secure code the first time around.

"
How does it work?" Let's take a look.
The Contrast Engine and TeamServer
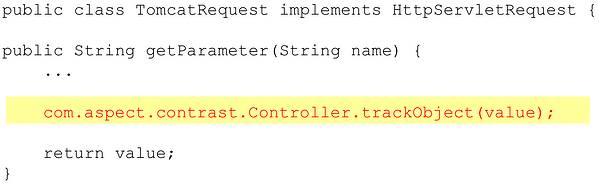
Contrast consists of two parts. The Contrast Engine is a 3MB JAR file that you drop onto your web application server. The Engine is a standard Java agent that uses the Java Instrumentation API (JSR 163) to passively monitor your running application and gather security critical information. The flexibility of Java byte code allows us to weave security sensors in very easily.
How does this work? Let's look at a simplified example of the technique we use to mark data that comes from an untrusted source:
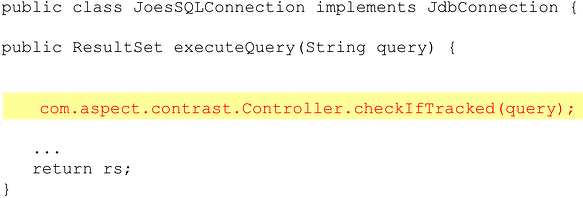
Now we weave in another check into the SQL code to make sure that the data used in queries isn't from an untrusted source:
"How do you weave these calls in?" Boy, you got a lot of questions.
Weaving a Tangled Security Sensor Web
Using JSR-163, we can make direct changes to a method's bytecode. Here's an example of what such a change would look like at the byte code level, from one of our test cases:
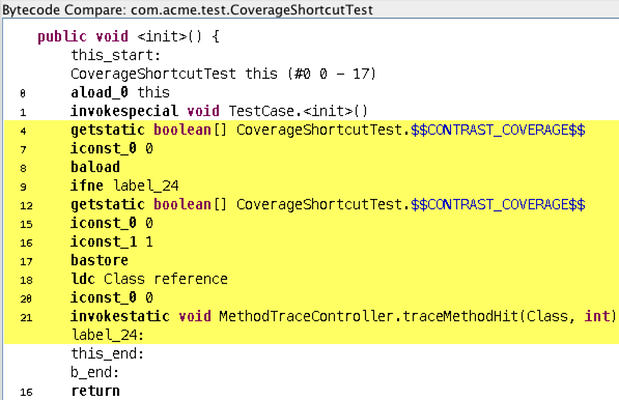
"How does this scale?" You keep asking the right questions! Do you want a job?
Using the Contrast TeamServer to Visualize Security
When then Engine identifies a vulnerability or other interesting security information using this technique, it sends it to the Contrast TeamServer, a web app for processing and viewing these analytics. In 5 minutes, you can be up and running, monitoring all the applications on your container for critical vulnerabilities. Contrast can monitor applications with millions of lines of custom code and hundreds of libraries easily without any extra hardware or effort.
The Contrast TeamServer provides insight into application security across an organization's entire portfolio. The TeamServer is built using a powerful Java EE stack including Tomcat, Spring, Hibernate, and many other community-driven libraries. This simple web platform allows us to scale the processing of sensor data from hundreds or thousands of applications. The inversion-of-control in Spring allowed us to easily develop both a SAAS and on-premise version of the product, with the magic of injection making our code easy to read and maintain. The database abstractions from JSR-317 (via Hibernate) gives our customers the flexibility to choose their own persistence option.
But all the end user cares about is the fact that the technology behind TeamServer automatically builds an application inventory across your entire portfolio, and provides up-to-the-minute insight into application security. You can even manage your security rules centrally, and push new rules out in real time. Every application gets a main dashboard that summarizes the security relevant information for that application.
What kind of vulnerabilities does it find? The ones that exist, and no others.
Amazing Web Application Vulnerabilities Coverage!
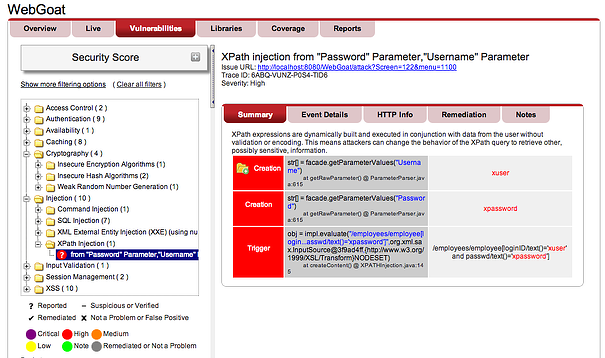
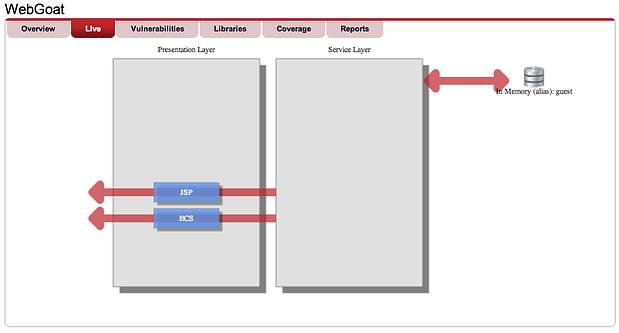
Contrast identifies a broad range of web application vulnerabilities, including the OWASP Top Ten and CWE Top 25 without the false positives that plague other tools. In the screen below you can see the main dashboard for the WebGoat application, a deliberately vulnerable application from OWASP. Contrast has identified 35 vulnerabilities and provides the developer the information necessary to eliminate it.
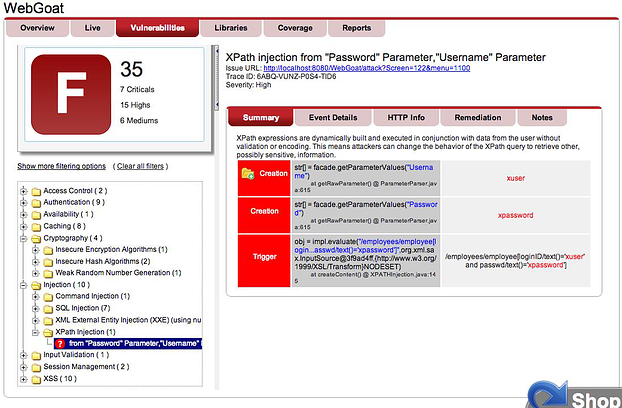
"What kind of info do I get about each vulnerability?" Lines of code, how to reproduce, and more.
The Contrast "Trace"
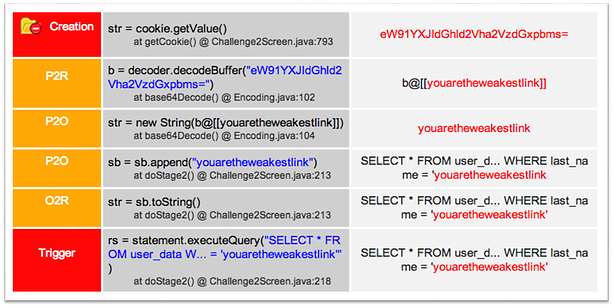
Every vulnerability is clearly identified for developers with a full vulnerability trace. In the trace below, a Base64 encoded cookie is accepted from the HTTP request, decoded into a byte array, and concatenated into a SQL query. An attacker could use this vulnerability to send a SQL injection attack and compromise the application's database. Contrast provides the exact lines of code, full remediation instructions, and even the HTTP request for retesting.
"Wow! Anything else?" That would be enough, wouldn't it? We took it further and solved problems the others can't hope to address.
Application Security Architecture Diagrams Directly from your Code
With rapid development and technology integration, it can sometimes be difficult to maintain accurate software and security architecture diagrams. This can be dangerous if decisions are made based on out-of-date or incorrect information. To help, Contrast automatically generates an architecture diagram based on the actual behavior of the running application. For example, whenever Contrast sees a database connection, it captures the metadata and adds it to the architecture diagram. It works the same for web services, directories, security controls, frameworks, UI libraries, and even client side technologies like JQuery, Flash, and Java Applets.
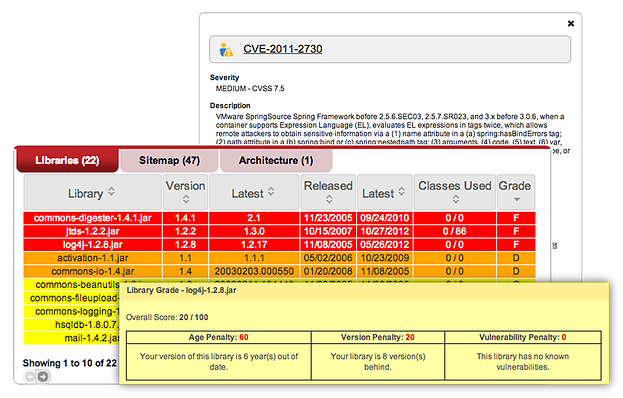
Contrast even examines the libraries in use in your application. We carefully analyze whether the libraries are out-of-date or have known vulnerabilities. This allows you to easily know which libraries need to be updated in order to prevent costly security exposures.
"What about my open source libraries? Can you check those?" You're right to be concerned about those. Thankfully, Contrast can help.
TheUnfortunate Reality of Insecure Libraries
Contrast even examines the libraries in use in your application. We do this in two ways. First, we carefully analyze whether the libraries are out-of-date or have known vulnerabilities. This allows you to easily know which libraries need to be updated in order to prevent costly security exposures.
We also analyze the way your custom code uses libraries, to make sure that you don't inadvertently make a call that exposes your application. For example, if you pass untrusted data into a library call, and somewhere inside that library, your data is appended to a command sent to Runtime.exec(), you might have just allowed an attacker to take over your entire application server. Contrast detects these problems easily where other tools cannot.
Developing and maintaining a robust application security program does not need to be a daunting task...
Perhaps, all it takes is rethinking your existing program and moving to one that leverages a continuous application security (CAS) approach. Organizations practicing CAS quickly determine how a new risk affects them, design a defense strategy, and measure their progress to 100% coverage. By implementing eight functions within an enterprise you can assemble an effective application security program.