 Not every vulnerability is a critical one. Let's face it: Not all vulnerabilities are created equal. Not every vulnerability is a major threat to national security, a financial database, or a commercial retailer's data collection on their customers. But because sometimes they are, you need to know which ones take priority when remediation time comes around.
Not every vulnerability is a critical one. Let's face it: Not all vulnerabilities are created equal. Not every vulnerability is a major threat to national security, a financial database, or a commercial retailer's data collection on their customers. But because sometimes they are, you need to know which ones take priority when remediation time comes around.
Knowing which vulnerabilities to focus on is just as important to knowing about the vulnerability in the first place. And though massive data leaks happen and breaches occur daily, to be clear, the sky isn't falling. This isn't a blog post about Chicken Little or Henny Penny with rants about "THE SKY IS FALLING. THE SKY IS FALLING!"
We simply think every application security product should have intuitive ranking system built into their continuously updated dashboard because it helps you prioritize your efforts *and* helps you do what needs to be done first.
Because honestly, in this day and age of DevOps and Agile SDLCs, who has time to wait for scans to be scheduled, reports to be run, false positives to be filtered, and remediation advice to be recommended. By the time all of that has happened, you'd need to do it all over again just to be current. You really need something updated continuously. You need information, and fixes, in the now. You need real-time application security analytics. <<insert shameless plug>> You really do need Contrast.
"Knowing which vulnerabilities to focus on is just as important as
knowing about the vulnerability in the first place."
The advanced instrumentation inside Contrast allows you to monitor what goes on inside an application, so you don't have to guess about vulnerabilities. Contrast identifies problems like the OWASP Top Ten, the SANS Top 25, and other important vulnerabilities in your code. It monitors for nearly 50 different types of vulnerabilities. Then it ranks them based on our decades of consulting experience within the application security industry to let you know where to start and what to focus on. And with Contrast, these things take seconds, not weeks or months, so you can get started fixing the vulnerabilities sooner rather than later.
How We Rank Vulnerabilities
We have an advanced approach to determine the level of risk that is associated with each of our findings. As part of that analysis, Contrast ranks both the likelihood of exploitation *and* the potential impact of exploitation. Likelihood is the probability that an attacker can find and attempt to exploit a vulnerability. Impact is the damage that can be done to the system if the vulnerability is exploited. Contrast ranks vulnerabilities in five main ways:
- Critical (purple): Critical issues are those that need to be resolved before the system is made publicly available. It has a low difficulty of discovery and/or exploit with high value assets or capabilities.
- High (red): Significant security issue that needs to be addressed. May be difficult to discover or exploit or may not involve highly valuable assets or capabilities.
- Medium (orange): Potential security issue that should be addressed in a future release. May be used for issues that are not currently exploitable but could become so later.
- Low (yellow): Minimal security risk in terms of likelihood and/or consequence. May be used for issues with an extremely low likelihood or impact.
- Note (green): Used to note particularly good practices, the failure to adhere to best practices, unsuccessful attempts to penetrate the system, or curiosities that may require attention but do not represent a security issue.
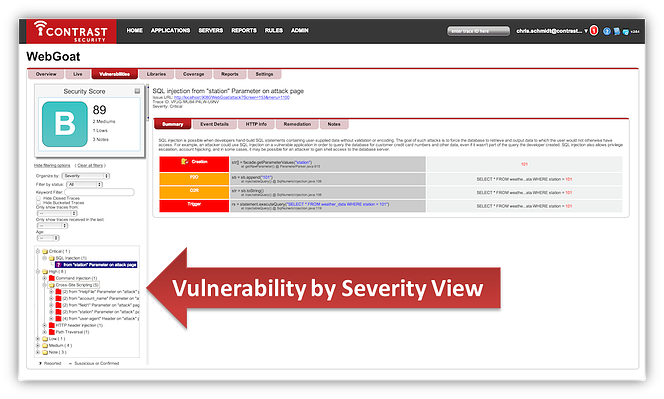
In the image above, you'll notice purple and red vulnerabilities. We thought we'd make it all a little easier to digest, so we've color coded the vulnerabilities as noted above.
"We simply think every application security product should have an intuitive ranking system built into their continuously updated dashboard because it helps you do what needs to be done first."
Identifying the level of severity of the vulnerabilities in your application portfolio allows you to focus on what matters most, and it lets you keep your system secure now *and* in the future. Because Contrast runs interactively and continuously on your portfolio of applications, you don't need to schedule times to do a hard scan and then wait for the results to be processed. It works while you sleep. Watch it in action when you schedule your free demo (or watch Jeff Williams test it on WebGoat).
At the end of the day, "Which application security vulnerabilities do I fix first?" is an easy question to answer: The vulnerabilities most likely to be exploited for damage. And you can find those vulnerabilities faster and more accurately with Contrast. Put Contrast to the test. You'll be glad you did.
Developing a robust application security program does not need to be a daunting task...
Perhaps, all it takes is rethinking your existing program and moving to one that leverages a continuous application security (CAS) approach. Organizations practicing CAS quickly determine how a new risk affects them, design a defense strategy, and measure their progress to 100% coverage. By implementing eight functions within an enterprise you can assemble an effective application security program.









