Application flow maps are the cool feature you can use to discover that needle in a haystack—how does my running app work and what does my app connect to?
HOW CAN ENTERPRISE TEAMS UNDERSTAND Application Flows?
Developers will often architect systems that cater only to business requirements and skip identification of security threats and vulnerabilities until later on when it's much more costly. Enterprises can improve overall protection and understand app flows by gathering an accurate asset inventory with connection discovery—basically mapping out your running apps and data flow—and along the way help reduce developer remediation times, security response efforts, and avoid the many costs associated with breach events.
Of course teams could document application flows and evaluate manually by using Excel spreadsheets or Office docs, but why would use a labor-heavy and static format that cannot scale easily? The combination of high complexity together with a siloed (and non-live) approach will cost the enterprise even more time and effort and, ultimately, human-reported results are not reliable. The most useful format for asset and flow discovery is an automated application flow map.
What EXACTLY is an Application Flow Map?
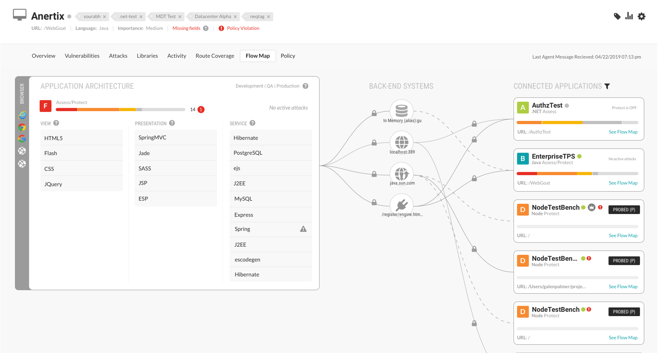
An application flow map is a simple interactive visualization that shows the vital relationship between your data and resources with the ability to drill down into details. An application flow map creates an accurate and explorable representation of your running applications and associated layers of technology, including back-end connected systems.
An application flow map can be built on string credentials discovered through application instrumentation (database connection strings, URIs, unique host and port combinations) which are visually represented as connected applications. A clear perspective of linked applications using a map modeled from these unique keys means every time you exercise an application you get up-to-date representations of all your applications and back-end systems in a user-friendly and interactive format.
If you have an application flow map you can quickly see what is connected to your running applications and rapidly visualize how an application stack interacts with other assets on your network. Do you feel something is slightly 'off' but you're not sure what it might be exactly? An application flow map is the cool tool you can use to explore and find that needle in a haystack.
Why is an Application Flow Map INVALUABLE for Application Security?
What is more important to know, connections to your application or application technology stack details? Well, a bit of a trick question, but it is knowing all app connections to other apps and shared resources, which libraries are in use, etc., that help augment the threat modeling process, automatically filling in basic details so that security professionals can focus on meaning.
Using an application flow map you gain understanding of the nature of your information systems, the most likely attack vectors, and the assets likely desired by attackers. An application flow map answers questions like “Where am I most vulnerable to attack?”, “What are the most relevant threats?”, and “What do I need to do to safeguard against these threats?” And, unlike application security questionnaires, flow maps do not require waiting on actions from developers. Instead, accurate and trusted results arrive directly from the running application itself.
A valuable use case may be determining how data is shared within the organization. For example, a security engineer might not be aware that their HR database is connected to their front-end e-commerce store or similar situations. When you visualize data and see everything together in a single location, visually exploring connections and relationships (instead of relying on mental conceptions in your head or static documentation), then you can rapidly discover the answers you need. Everything is faster and easier if you have a map!
- Visualize entire landscape of systems and resources associated with an application
- Identify exact way apps connect to each other through shared back-end systems
- Show all shared resources between apps and understand how to defend against lateral movement
- See where app data flows and connects to back-end systems and other apps, connection security
- See what browser layer technologies are accessing the app in real-time
- Single-click reveals of access privileges (user and application) plus associated PII and sensitive data flow
- Discovery of all significant app details (deployed environments, risk letter grade, vulnerability and attack status, assessment and protection status)
These are the detailed answers—quickly made discoverable by a visualized application flow map interface—that security professionals and developers seek when asked to investigate applications or backend systems.
Flow maps enable self-exploration for all connections to your apps and surfaces hard-to-find, valuable insights into the actual technologies that a running application is using across View, Presentation, and Service layers.
-
View visibility may expose rendered content details (HTML, JSON, XML) that clients connected to your application consume including, in the case of HTML pages, assets that the client is instructed to render or process (images, Flash, JavaScript, CSS, audio and video)
-
Presentation visibility may show how your app interprets and responds to the client requests (templating libraries like Mustache or Jinja), transpiling code (SASS to CSS, TypeScript to JS), or handling and routing client requests (Django, Express.js, Ruby on Rails, ASP.NET, Vert.x)
-
Service details may show external technologies like data stores (NoSQL or SQL) that are interacting with your application or technologies related to messaging queues, job schedulers, authentication and authorization services, and data processors (JSON, XML, SOAP)
The best application flow maps support easy accessibility to this important application and security data to inform security and development decisions and make your complex running systems instantly understood and fully traceable.
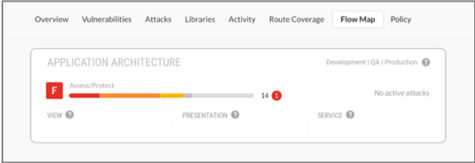 A risk summary of all this metadata in the form of a card—including an instantly recognizable score or grade—is the final piece of an application flow map that adds the most value to any business.
A risk summary of all this metadata in the form of a card—including an instantly recognizable score or grade—is the final piece of an application flow map that adds the most value to any business.
Rapid understanding how interactions between applications and external systems affect overall security along with analysis reporting including simple scores and letter grades allows anyone to effectively manage risk and to control and improve policy and processes based on this valuable insight.
Start Using Application Flow Maps—Free, Full Community Edition
Try for yourself the free, full-strength, Contrast Community Edition to find out first-hand how an application flow map can make life easier, allow you to see many correlations and 'the big picture', and help your teams solve complex problems in your system architectures.
"Seeing is believing" is what should come to mind when asked about how valuable application flow maps are to speeding up application security, testing, security assessment, incident response, or any type of architecture analysis. Ask someone who has used (and seen with their eyes) application flow maps to describe its value and immediately they will say in response, "Well, that's easy, let me show you so you can immediately see for yourself too."
Thank you for helping us protect the world by protecting their applications.




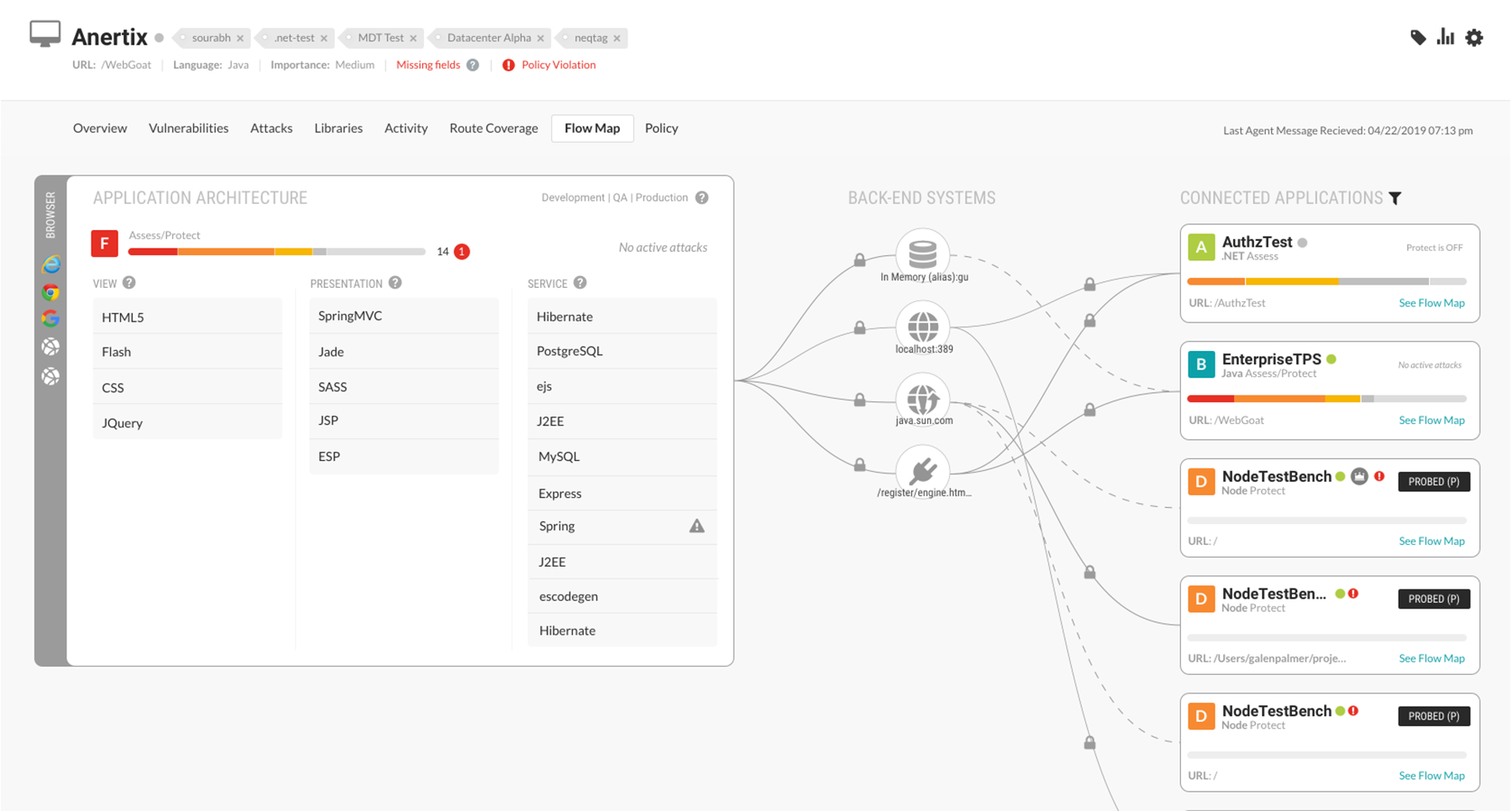

 A risk summary of all this metadata in the form of a card—including an instantly recognizable score or grade—is the final piece of an application flow map that adds the most value to any business.
A risk summary of all this metadata in the form of a card—including an instantly recognizable score or grade—is the final piece of an application flow map that adds the most value to any business.