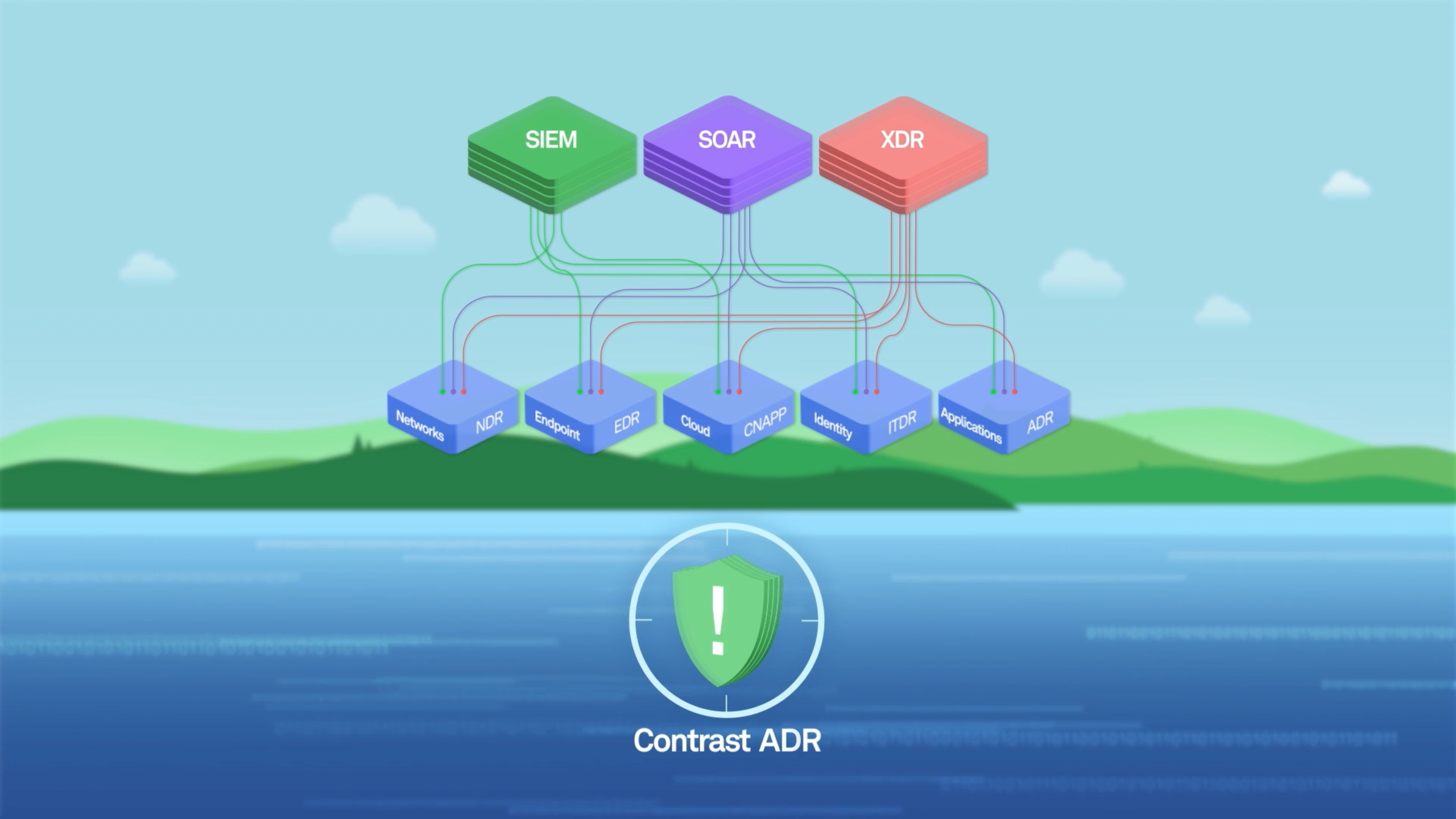
On Aug. 6, Contrast Security introduced a new security technology we call Application Detection and Response (ADR). ADR seeks to fill a critical gap in Application Security (AppSec) that leaves the application layer vulnerable to attack.
There’s a gap because traditional forms of detection and response — a range of platforms that cover endpoints, cloud, identity and network, among others — simply don’t work well at the application layer. Indeed, they often even fail to see, much less respond to, threats and vulnerabilities in production code.
We take a deep dive into these issues in our new white paper, The Case for Application Detection and Response (ADR), which we invite you to read (PDF).
Why protect applications and APIs in production?
The application layer is where you run your software applications and application programming interfaces (APIs). The more your business relies on software, the more critical the application layer is. This is all the more true if your business strategy is based on software innovation and connectivity through APIs, as is the case with digital transformation.
The application layer is also a point of great vulnerability. Not only can a malicious actor disrupt your business by attacking the application layer; they can also access the rich streams of data that flow through this layer, including data related to our finances, healthcare, government and social life. For these reasons, attacks on the application layer are quite common, with web application and API breaches appearing among the top three attack vectors in the 2024 Verizon Data Breach Investigations Report.
How current AppSec detection and response measures fall short
Despite being a source of significant risk, the application layer has proven difficult to defend. For one thing, modern applications are dynamic and interconnected, especially for organizations that engage in agile development and continuous integration and continuous deployment (CI/CD) of new code. Most AppSec has fallen to developers, who fix vulnerabilities in the development stage. Once code is running in production, zero-day threats and many other hidden vulnerabilities are virtually invisible to web application firewalls (WAFs) and traditional security operations (SecOps) tools like extended detection and response (XDR).
ADR: A new approach to AppSec
ADR addresses these security deficits at the application layer by embedding agents in applications and APIs. From this inside position, ADR can protect, detect and respond to threats in real time, providing continuous visibility into the security behavior of the entire software stack. ADR identifies anomalies that signal that a security incident is underway and automatically takes action to mitigate these threats. It also provides enriched data with contextual feedback to the security operations center (SOC) and development teams. This capability helps SOC analysts respond more quickly and effectively to threats at the application layer.
E.g., an unsafe deserialization incident
The example of an unsafe deserialization incident reveals the deficiency of existing AppSec countermeasures and the potential of ADR to defend the application layer. Picture an enterprise web application that exchanges data with a JavaScript user interface in the browser. The developer who built the application followed common coding patterns and “serialized” data objects in the browser into a stream of bytes that are “deserialized” back into objects in the web application. In doing so, the developer didn’t realize that they had inadvertently introduced a serious unsafe deserialization vulnerability.
Regular Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) missed this problem. As a result, a malicious actor can exploit the deserialization vulnerability with a malicious serialized object that includes a payload designed to execute arbitrary code on the server. Using this attack vector, the threat actor can take over the server.
A WAF won’t stop the attack from reaching the application because it lacks visibility into the serialized object and can’t tell that the malicious payload is any different from normal traffic from a legitimate user. The company’s endpoint detection and response (EDR), extended detection and response (XDR), security information and event management (SIEM), and cloud-native application protection platform (CNAPP) solutions will also miss the attack because they’re focused on monitoring endpoints, networks and logs for known attack patterns and anomalies.
The good news is an ADR platform can continuously monitor the entire application stack in real time — detecting the unsafe deserialization vulnerability as it is being exploited. The system generates a detailed incident report containing the complete HTTP request details. The report includes the payload, along with a stack trace of the deserialization operation that is captured directly from the running code. It also contains a contextual diagram that provides the security context of the route being attacked. SOC analysts can act quickly with this information, perhaps initiating an incident response workflow from a security orchestration, automation and response (SOAR) solution or assigning an incident response team with all of the context they need to address the attack.
Conclusion
The application layer is vulnerable to attack, and existing countermeasures are not up to the job of protecting it. ADR is a new approach — one that leverages an inside-out approach to monitor code running in production, identifying anomalies and threats and sending data-intensive alerts to SOC teams for rapid incident response.
To learn more, read the white paper (PDF), The Case for Application Detection and Response (ADR).
Read the white paper
Related: