Continuous Compliance Testing for the SDLC
Always-on continuous code security assurance across the software development life cycle for NIST, PCI, and beyond.
The Software Compliance Challenge
Organizations are overburdened by the speed and scope of government and industry regulatory changes, while balancing the rapidly evolving landscape with the lightning pace of digital transformation.
Always-evolving regulatory landscape
Problem: The rising business criticality of software, coupled with recent highly visible software security incidents, have instigated key changes to the regulatory landscape. This has led to a set of net-new security mandates—and more are on the horizon. These prompt teams to play a balancing act between prioritizing security controls and the ability to ensure and demonstrate alignment with key mandates. A good example of this is NIST 800-53 SA-11 and SI-7.
Implication: Security teams struggle to prioritize and demonstrate compliance.
Point-in-time audits, always-changing risk
Problem: Audit and assurance teams must take a "point-in-time" approach to assessing an organization's risk and compliance posture. An organization's assets and associated risks, however, are constantly changing due to the rapid pace of code generation (brought on by Agile and CI/CD) and the ephemeral nature of cloud workloads.
Implication: Audit team assessments do not reflect true risk posture.
Manual, DISPARATE
Reporting
Problem: Demonstrating alignment with key standards requires pulling reports from disparate systems. Evidence for secure developer training differs from risk assessment reports, which differs from proof-of-attack protection coverage.
Implication: Compliance reporting is time-consuming, incomplete, and not continuous.
The Contrast Solution
Continuous compliance testing provides software security assurance
across the software development
life cycle
Continuous, Integrated, Demonstrable Reporting
Integrates across the software development life cycle (SDLC)
With a single integration point, the Contrast platform delivers software composition analysis (SCA), application security testing, and exploit prevention capabilities, allowing developers to instrument security across the software development life cycle (SDLC).
The Contrast platform makes compliance reporting (and subsequently assurance) automated, continuous, and integrated. In addition, the platform also offers flexibility in reporting formats, including (1) in UI, (2) exportable reports, and (3) through REST API calls.
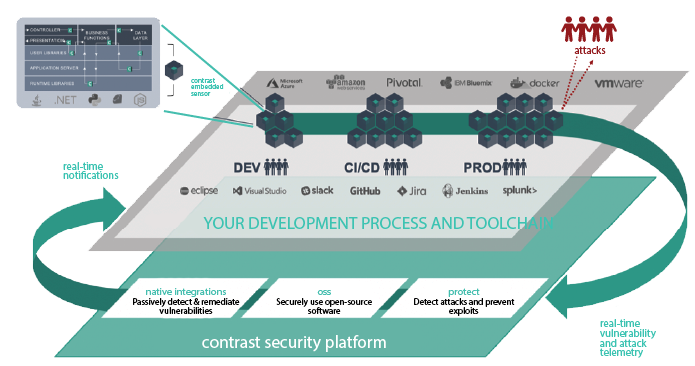

Instrumented Security for NIST 800-53 Rev 5 and Beyond
Contrast’s security instrumentation delivers NIST-compliant interactive application security testing (IAST) that is comprehensive, continuous, and demonstrable for standards beyond NIST. Specifically, Contrast allows the developer of a system, system component, or system service to employ IAST tools to identify flaws and document the results. Going beyond NIST, Contrast’s integrations deliver the results instantly to developers and line-of-code level,“how-to-fix” guidance that empower developers to fix vulnerabilities quickly without security expertise.
In addition, Contrast’s instrumentation also delivers NIST-compliant runtime application self-protection (RASP) that allows the implementation of key security controls for application self-protection at runtime.
Alignment with the PCI Software Security Framework (SSF)
The Contrast Secure Code Platform provides a suite of capabilities that help businesses meet PCI standards head on – aligning to both technical and process requirements of the PCI Software Security Framework (SSF).
By connecting industry-leading secure code coverage across applications, APIs, serverless, and open-source libraries within a common platform, Contrast Security is uniquely positioned to enable operational shifts for more informed security policy decisions, advanced threat detection, and stakeholder communication.

Compliance: From Point-in-Time to Continuous
| Strategic Compliance Objective |
HITRUST Maturity Requirement1 |
How Contrast addresses those requirements |
Key Improvements over Legacy AppSec |
|---|---|---|---|
|
Improve sustainability of control environment
|
• Policies, procedures, implementations, and tests are continually reviewed and improvements are made
• Security vulnerabilities are understood and managed |
• Contrast provides real-time, continuous compliance verification to listed regulations
|
• Continuous measurement, not just “point-in-time” • Works at all stages of the SDLC, not just at the latter stages when cost to fix is higher |
|
Enhance PII / PHI protection at rest and in motion
|
• Controls are adapted to emerging threats and the changing information security environment
|
• Contrast maintains integrity and confidentiality of data as they are transmitting as well as by identifying and protecting against threats to PHI
|
• Information collected and stored by Contrast is always encrypted - with mutually authenticated TLS communications and full-disk encryption in storage
• Continuous measurement, not just “point-in-time” |
|
Enhance risk assessment methodology and depth
|
• Security vulnerabilities are understood and managed
• Effective corrective actions are taken to address identified weaknesses |
• Contrast provides a real time application risk assessment score and vulnerability assessment details
|
• Contrast risk-scores applications in real time and assesses applications by SDLC environment (dev, QA, production)
• Dramatically increased visibility – including (but not limited to) line of code, stack trace, data flow analysis and resolution steps – for fast, accurate risk assessment |
|
Provide flexibility and granularity in reporting
|
• Status metrics for the information security program as well as individual information security investment performance measures are met
|
• Contrast reports on PCI DSS – 2.0, PCI – DSS 3.0, OWASP Top 10 and DISA ASD STIG
• Contrast provides full REST API for sharing inventory, vulnerability, and attack data with other reporting systems |
• Contrast provides compliance reporting instant and on-demand
• Reports contain detail that can directly address key controls and remediate gaps • A flexible API allows security and compliance teams to pull and analyze application risk data that can only be delivered by deep security instrumentation |
| SUPPORTED FRAMEWORKS (Not exhaustive) |
|---|

| COVERED REGULATIONS (Not exhaustive) |
|---|
| HIPAA Measure | How Contrast addresses those objectives | Key Improvements over Legacy AppSec |
|---|---|---|
|
Risk Analysis & Management
|
• Contrast enables organizations to assess and safeguard the key risks and vulnerabilities in their applications that handle PHI
|
• Contrast monitors and risk-scores applications continuously and in real time.
• Contrast’s multi-factor analysis has significantly better coverage and accuracy than legacy tools, including the full application stack and a broad range of vulnerabilities. • Contrast provides a view of application in risk by environment (dev, QA, production). |
|
Protection from Malicious Software
|
• Contrast both identifies malicious code and prevents attempts to exploit applications.
|
• Contrast’s deep security instrumentation enables protection measures across the full application stack (source code, data flow, libraries, frameworks, app server, platform, etc.). Legacy AppSec scans only the source code.
• Contrast protects applications from attacks targeting both known and unknown vulnerabilities, including CVE Shields to protect against the latest vulnerabilities in 3rd party code. |
|
Integrity
|
• Contrast provides integrity protection for PHI at rest and in motion by continuously scanning for vulnerabilities as well as blocking attacks on system integrity.
|
• Contrast provides continuous assessment and protection.
• Contrast provides integrity protection across the full application stack and not just source code. |
|
Authentication
|
• Contrast ensures the application transmits data via appropriate channels using strong and properly configured encryption.
|
• Contrast provides continuous assessment and protection.
• Contrast identifies a broader range of misconfigurations and encryption misuse. |

Full Life-Cycle Security & Assurance With Contrast
learn more about how to use Contrast SCA, Assess, and Protect to integrate continuous software security assurance across the SDLC.
Experience Contrast today
See how you could get secure code moving on the Contrast Secure Code Platform









