Contrast Application Security in Government and Public Sector
Defend against entire classes of application attacks with Protect and build SBOMs in minutes.
Contrast Application Security for Federal and State Agencies and Public Sector
Contrast Security is committed to protecting American cyberspace. Application attacks and attacks against application programming interfaces (APIs) are surging. As government and public sector agencies digitally transform, they must do so with vigilance. The federal mandates for “zero trust” and continuous monitoring must extend to software development and application security. The recent White House memorandum regarding supply-chain security underscores this reality.

FedRAMP
President Biden’s Executive Order on Improving the Nation’s Cybersecurity
President Biden mandates that software security is a national security matter.
In May 2021, during the fallout of a successful ransomware attack on a pipeline that supplies nearly half of the U.S. East Coast’s gasoline, President Biden signed an executive order placing strict new standards on the cybersecurity of any software sold to federal agencies. The order called out several specific areas where agencies need to elevate their application security capabilities, including:
- Establishing effective application security policies
- Instituting a “zero-trust” architecture where appropriate
- Greater software supply-chain transparency via Software Bills of Materials (SBOMs)
- Defining more stringent standards for testing, monitoring, protection and reporting
- Standardizing a federal playbook for cybersecurity responses
With limited security expertise available, agencies must be able to detect vulnerabilities within the software life cycle to ensure rapid, cost-effective remediation and enable developers to secure as they code.
Contrast Secure Code Platform for Public Sector and Government
The government and public sector’s only development-to-production code application security platform.
The Contrast Secure Code Platform directly supports the majority of the goals presented in President Biden’s executive order, along with many other government directives. Contrast application security for government and public sector detects vulnerabilities as developers build and test code and protects applications in real time. This level of automation results in unmatched efficiency, scale and risk reduction.
Improves Efficiencies
Accelerates efficiencies by detecting vulnerabilities in real time during development, resulting in secure code delivered 10x faster at lower cost.
Enterprise Scale
Designed for modern software, Contrast detects vulnerabilities in custom and open-source code as well as in APIs, regardless of where the code is run — all while offering embedded protection in production.
Prioritized Remediation
Reduces alert fatigue, triage time and remediation expense with accurate detection and prioritization of vulnerability fixes.
Lowers Risk
Improves security awareness across the entire software development life cycle with orchestrated code run-time observability and security telemetry.

Texas Risk and Authorization Management Program
Contrast Security has earned provisional status certification under TX-RAMP. We anticipate full TX-RAMP certification achievement by early 2024.
Unleashing Security Observability
Empowering public sector and government application developers to get secure code moving faster.
Contrast Security offers public sector and government agencies working with limited security resources full transparency of their application risk layer while also protecting against targeted attacks and zero-day events. By embedding security sensors within the code itself, the Contrast Security platform shifts security left in application development, empowering DevOps to secure as they code and to dramatically reduce application security incidents in the public sector.
Software supply-chain transparency
Contrast automatically catalogs your proprietary and third-party software assets into a digestible SBOM while also providing insights regarding dependency risk and flagging new vulnerabilities in real time.
Embedded software security policies
Integrated security policies help provide oversight and governance within pre production environments and protection rules to block targeted attacks in production.
Protection in the wild
Contrast blocks attacks targeting vulnerable components and offers mitigating controls against zero-day events with no patching required.
Continuous monitoring
Designed for modern software, Contrast continuously monitors and detects from within software regardless of where the application runs.
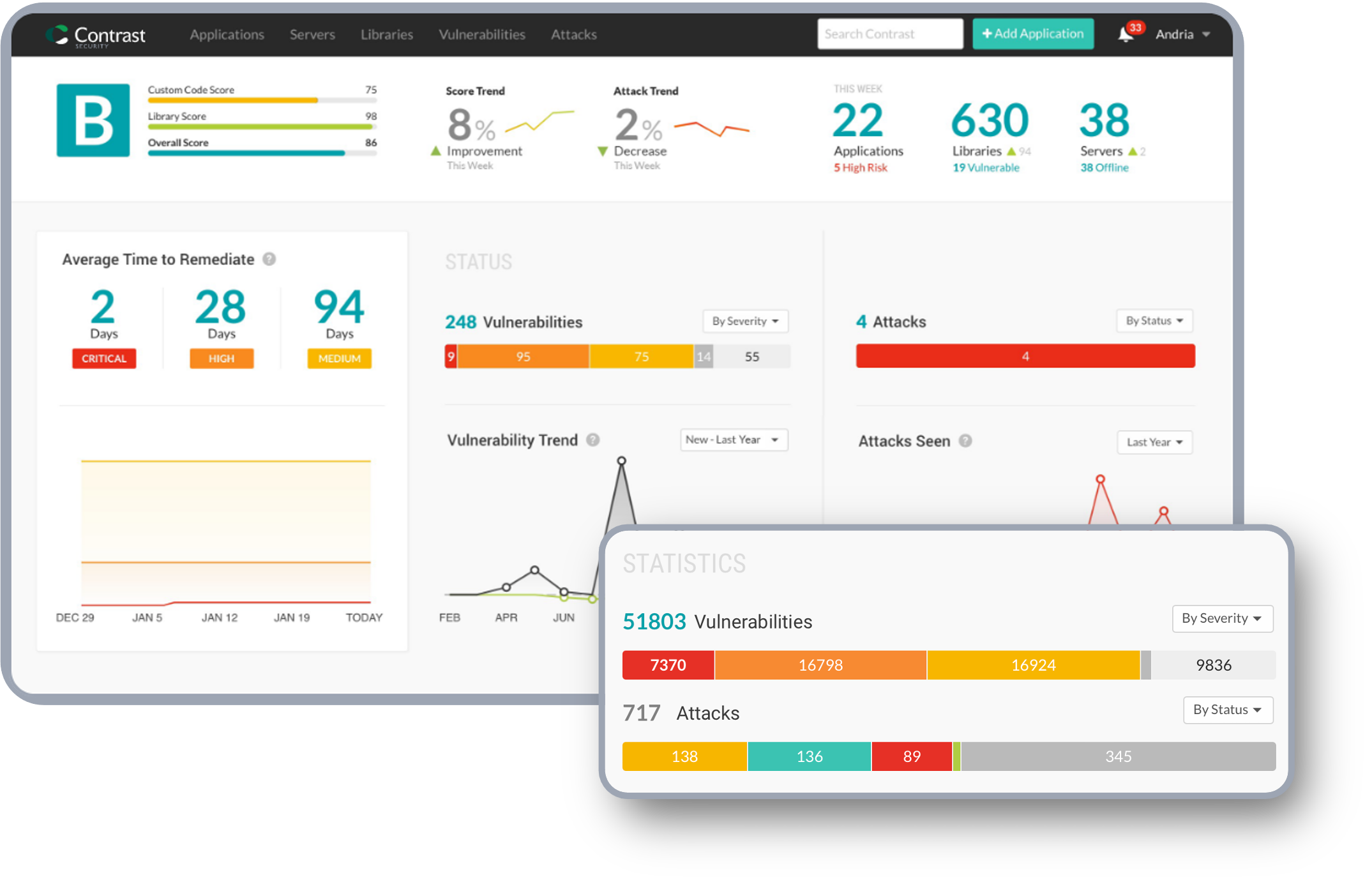
Create SBOMs in Seconds
Maintain up to date SBOMs across all your applications and APIs.
Contrast Maps To The Latest
Federal Directives
OMB 22-18 Requirements
Datasheet
In 2023, application attacks and attacks against application programming interfaces (APIs) are surging. As agencies digitally transform, they must do so with vigilance. The federal mandates for “zero trust” and continuous monitoring must extend to software development and application security.
DEFEND FROM WITHIN
Blog
In recent years, geopolitical tension has been escalating in cyberspace, with the war in Ukraine spawning systemic cyberattacks against Western critical infrastructure. In 2023, defending from within will be paramount.
How to create SBOMs for free with CodeSec by Contrast
Blog
A recent Executive Order from the Biden Whitehouse instructs various government agencies to take action to improve our nation’s cybersecurity. One of those actions is to provide guidance and standards on Software Bills of Materials (SBOMs).
CISA Zero Trust Maturity Model
Contrast maps to the directives of the Application Security pillar (Pillar 4).
NIST 800-53, Rev. 5
Blog
Contrast employs Runtime Application Self-Protection (RASP) to address SI-17(7) and Interactive Application Security Testing (IAST) to address SA-11(9) in the latest NIST 800-53 revision.
Biden administration 2021 cybersecurity executive order
Blog
Agencies can meet requirements outlined in EO Sections 2, 3, 4 & 7 for the purposes of modernizing federal app security and software supply-chain observability.
CISA binding operational directive 22-01
Blog
Agencies can leverage Contrast to help remediate over 250 vulnerability classes mentioned in the directive while providing real-time protection as a mitigating control.
The U.S Department of Defense is Expanding its Security Framework to Include Continuous Monitoring Controls
Solution Brief
Government and federal agencies have long observed the National Institute of Standards and Technology’s (NIST’s) Risk Management Framework for security frameworks to help agencies select suitable safeguards relating to cybersecurity, privacy and supply-chain risk management.
FedTalks 2022
Impact of the Cybersecurity Executive Order on Transparency and Security in the Software Market
Jeff Williams, Contrast co-founder & CTO, on the impact of the Cybersecurity Executive Order on transparency and security in the software market.
Federal Partners





Welcome to the New Era of Accountability
Protect your entire software development lifecycle with complete security transparency
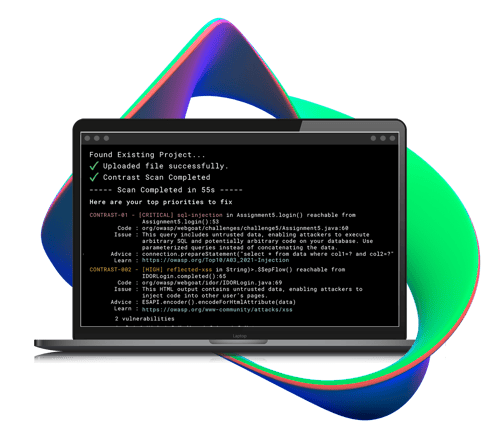
Additional Resources
Certification
Public agencies can “lean in” on digital transformation with confidence.

GENERAL SERVICES ADMINISTRATION
Proven application security experience for technical and service contracts

SEWP V
SEWP V Simplifies buying application security solutions

NIST 800-53 COMPLIANT
Complies with both the IAST and RASP requirements

DOD PLATFORM ONE
Preapproved Authorization to Operate (ATO) the Contrast Application Security Platform

IRON BANK - DOD CENTRALIZED ARTIFACTS REPOSITORY (DCAR)
Authority to Operate (ATO) achieved via Platform One

AICPA SOC2 TYPE II
Integrated service offerings that provide rapid time to deployment

Texas Risk and Authorization Management Program
Contrast Security has earned provisional status certification under TX-RAMP. We anticipate full TX-RAMP certification achievement by early 2024.
Helpful Links
Get in Touch
See how the Contrast Secure Code Platform can help your business defend against entire classes of application attacks and build SBOMs in minutes.










