Detect and respond to attacks on applications and APIs before exploits occur.
Try Contrast
surge in the number of application and APIs attack in 2024 1
attacks bypass the WAF and exploit vulnerabilities in the average app monthly 2
of application security events take more than 12 hours to resolve 3
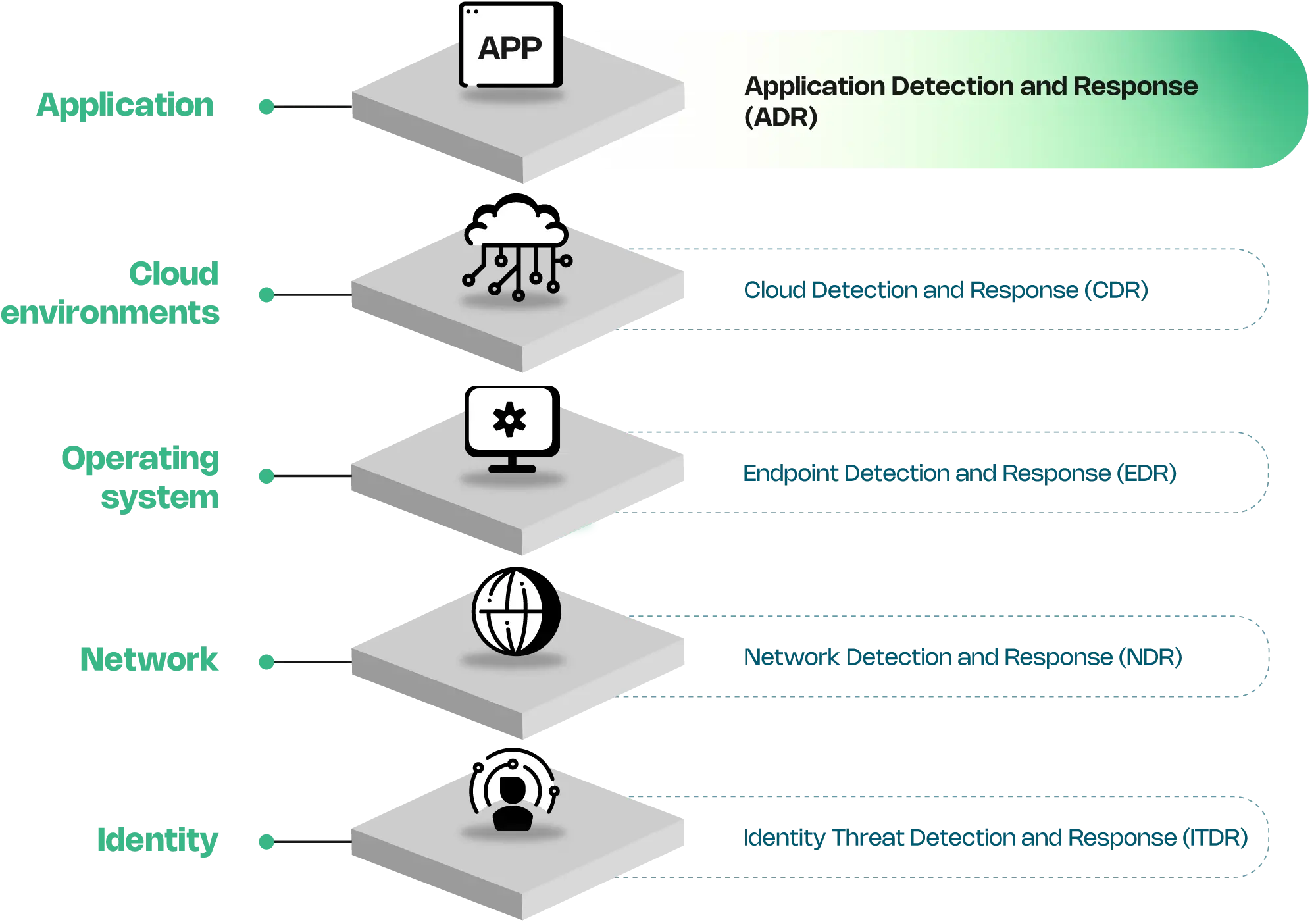



Runtime protection blocking for application attacks, even if the exploit is novel.
Detects and alerts on anomalous behavior within the application layer.
Continuous application and library vulnerability monitoring in production.
Clear, actionable steps to quickly identify true positive attacks and contain threats.
Gain context from application alerts related to suspicious activity, payloads, IoCs and more.
Real-time security blueprints provide context to incidents better to assess the impact of an attack.
Integrate accurate ADR alerts to monitor and triage across the SIEM, XDR, SOAR and CNAPP.
Respond efficiently with insights from inside your applications.
Continuous visibility into exposure of your applications in production, enabling proactive risk mitigation.
Add context to attack vectors with vulnerability data, enabling faster and more effective triage and response.
Focus on the vulnerabilities that truly matter, reducing backlogs and accelerating remediation efforts.

Managed runtime security powered by the people who built it.
Learn more