Detect attacks on applications and APIs so security operations teams can respond before exploits occur.
Identify vulnerabilities and stop attacks in real-time with innovative, in-app technology
Try Contrast
Experience the power of instrumentation by embedding threat sensors that detect and secure applications from within.
Gain visibility and secure the entire application stack and software supply chain, auto-remediating exploitable vulnerabilities with Contrast AI.
Leverage context-rich application threat alerts to quickly triage, prioritize and respond to advanced threats.
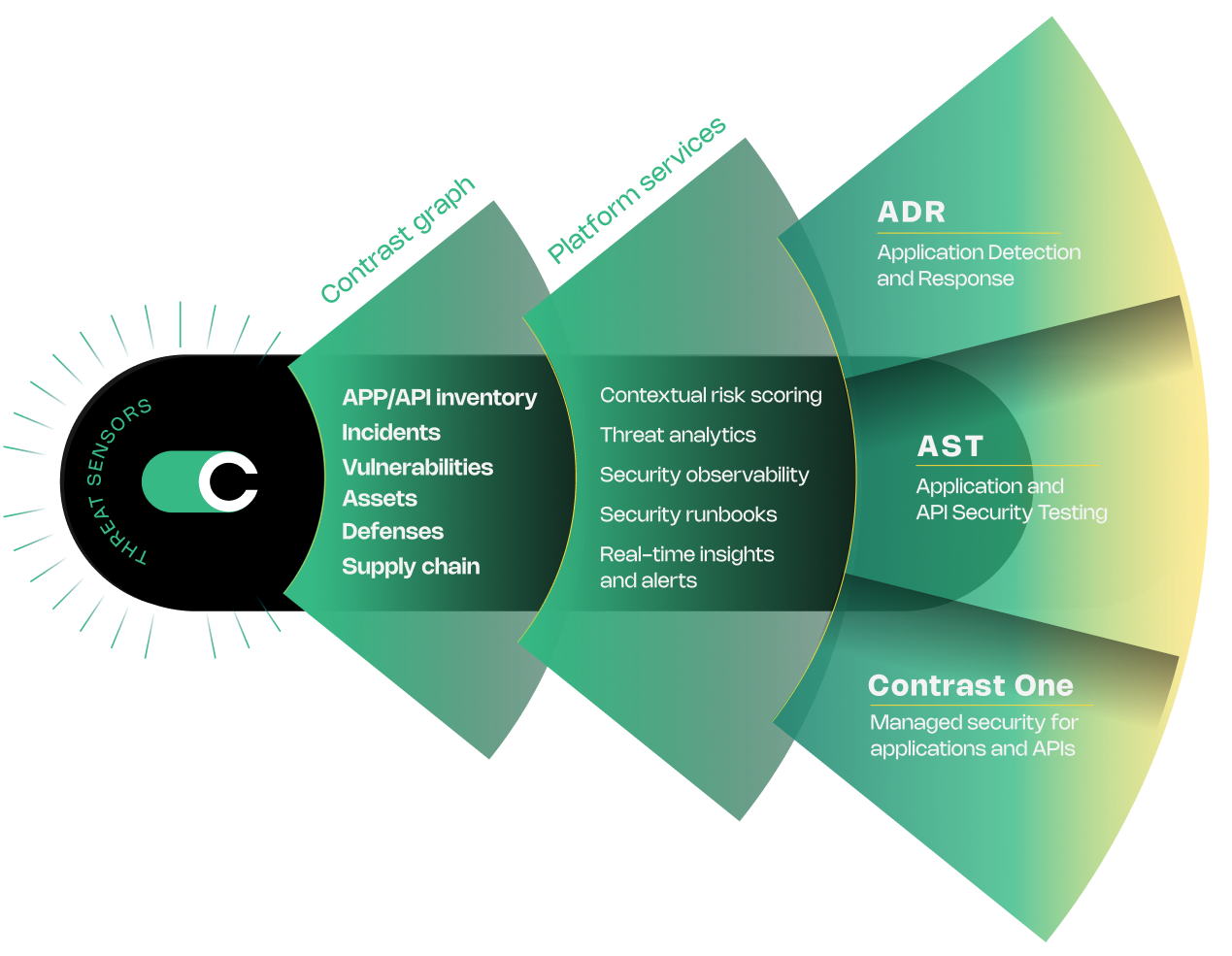
The Contrast Graph is the core of the platform, providing runtime intelligence that builds a unified, real-time security model for your entire application and API security ecosystem.
Learn moreUnify dev, security and ops with real-time correlated visibility into attacks and live vulnerabilities, with rapid resolution leveraging AI-powered remediation guidance.
Monitor applications in dev, staging and production to instantly flag policy violations.
Rich integrations with DevOps and SecOps tooling and workflows.
Detect exploitable vulnerabilities missed in development, without impacting performance.
Contrast AI SmartFix suggests and applies targeted code fixes within minutes or integrates into preferred AI models through the Contrast MCP Server.
Apply security rules instantly across all applications, without the need for re-deployment.
Secure the full application stack, including third-party applications, custom code and dependencies.
Real-time, integrated dashboards covering inventory, attack surface, vulnerabilities, threats, defenses, connections and more.
Analyze security data from hundreds or thousands of applications across all environments.
See and stop application attacks before vulnerabilities are remediated.
Fix code quickly and reduce backlog by identifying exploitable vulnerabilities at runtime.

Detect attacks on applications and APIs so security operations teams can respond before exploits occur.

Prioritize and address risks with faster vulnerability detection and fewer false positives.