EBOOK
Contrast Protect your RASP solution
Detecting zero days and protecting applications in production
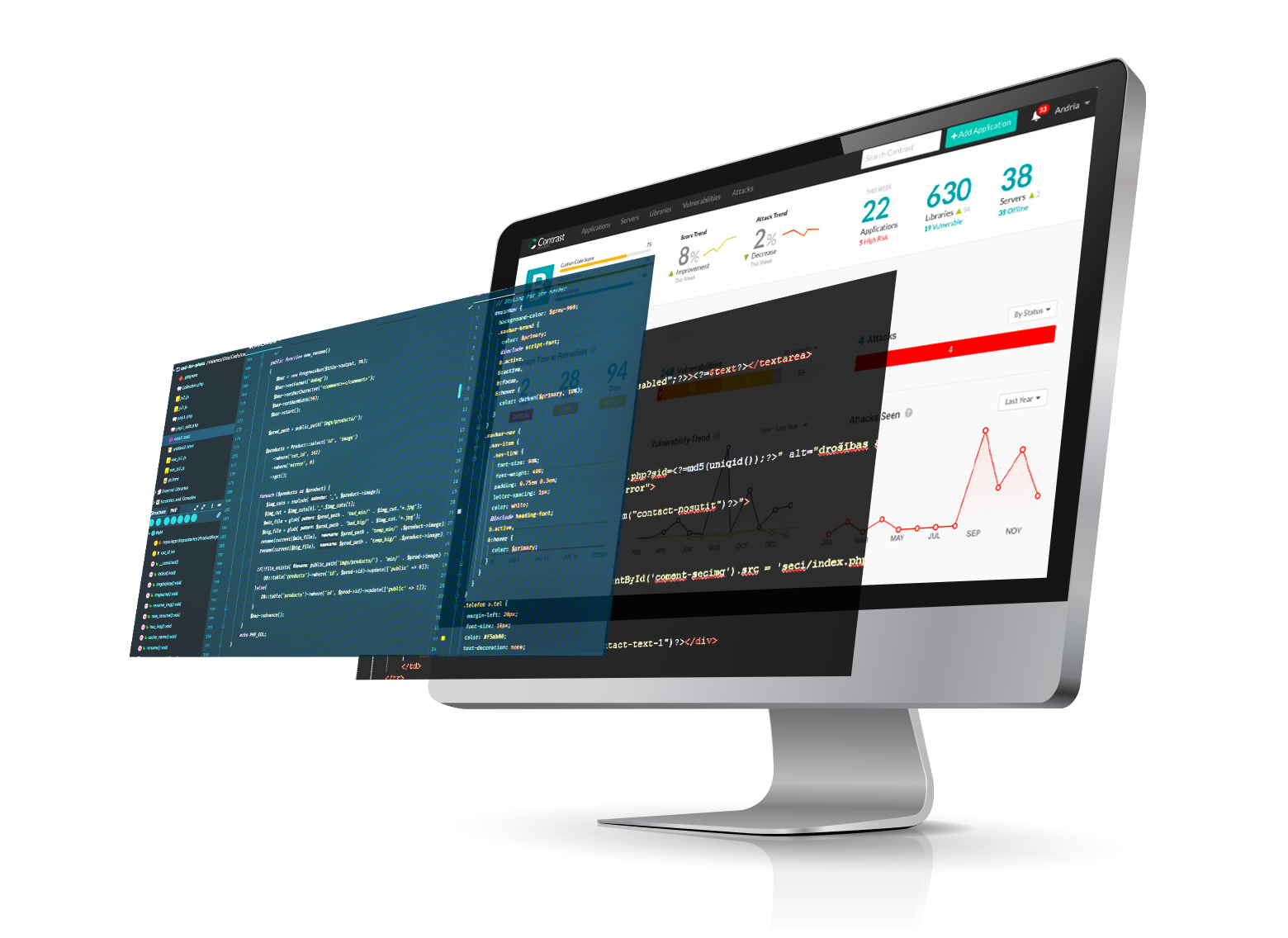
The application protection problem
Untrustworthy software hurts business...
lost revenue, reputation, potential legal liability
- New zero-day attacks are wreaking havoc (log4shell, spring4shell)
- US Executive order and OMB-22-18 requires AppSec “attestation statement”
- Custom code and libraries are full of vulnerabilities (avg: 30+ serious vulns)
Traditional remediation is untrustworthy
Too much trust in...
PEOPLE
You trust your people... but they can’t afford the time to conduct exhaustive security testing and remediate all the problems
PERIMETERS
Web Application Firewalls (WAFs) and API Gateways don’t have enough context to accurately defend 100% of attacks and prevent exploitation
How can we put the right defenses in the right places?
What would ideal defenses look like?
-
Very fast
-
Simple and verifiable
-
Highly accurate
-
Automatic without tailoring or tuning
-
Safe to use
-
Not intrusive to your teams
What should defenses do?
-
Prevent exploits
-
Detect attacks and snapshot context
-
Enable incident response
The application protection agent
A zero friction agent
For production applications:
- Automatically hardens the runtime, libraries, open source software, the appserver
-
Integrates with your SIEM and SOC
-
Mitigates top vulnerability classes & zero-days
-
Supports attestation reporting & compliance
Not fixing your code, fixing security at the underlying language environment
- Make exploits not possible

Runtime protection
Uses instrumentation to inject automated trust boundaries into software as it loads
Eliminate time-consuming and ineffective manual effort
-
Eliminate impact on developers
-
No code changes
-
No configuration needed
-
Fixing security at the root
Your App/API Stack

Untrusted data boundary
Deserialization attacks exploit a fundamental process within many applications. Applications often serialize data – converting objects into a format suitable for storage or transmission. Later, this data is deserialized back into objects for use by the application. Attackers can craft malicious payloads that, when deserialized, trigger unexpected or harmful actions within the application.
Simply prevents untrusted data from reaching a potentially dangerous module
-
Completely prevented Log4Shell attacks
-
Impossible to do accurately at the perimeter

Surrounding dangerous functions with trust boundaries

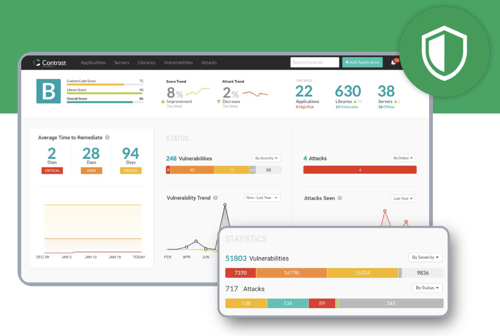
Contrast Protect
The digital vaccine for vulnerabilities
-
Zero Trust for the application layer
-
Extremely high performance, no bottlenecks
-
Broad vulnerability remediation for libraries AND custom code
-
One time install. No change to how you build, test, deploy apps
-
You’ll never know it’s there unless you’re an attacker
Contrast Protect helps organizations comply with mainstream industry standards such as the National Institute of Standards and Technology (NIST) and the Payment Card Industry Software Security Standard (PCI-SSS). NIST standards are used for things such as measuring equipment and procedures and quality control. PCI-SSS are new requirements for the secure design and development of modern payment software.
RASP technology is already a requirement in NIST 800-53—which covers recommended security-control selection—and already a requirement in PCI-SSS 9.1, 10.2a, and 10.2b which defines security requirements to ensure payment software protection.
Contrast Protect – enterprise deployment
Deploy automatically via:
- Kubernetes operator
- Gold server
- Container build
- Ansible
- CI/CD pipeline
- Platform engineering and more

Reduce App/ API risk |
|
Unlock Dev productivity |
|
Strengthen the SOC |
|
Zero days blocked before discovery hall of fame
Contrast detects & prevents exploitation against entire classes of vulnerabilities via embedded detection rules
Examples of zero days that Contrast mitigated before they were discovered (before CVEs were issued):
-
Spring/Kafka — Deserialization opens risk to Remote Code Execution - CVE-2023-34040
-
Spring4Shell — Command Injection/ClassLoader manipulation - CVE-2023-22965
-
Log4Shell — Expression Language Injection - CVE-2021-44228
-
Confluence OGNL Injection — CVE-2021-26084
-
Apache Struts2 — CVE-2020-17530
-
Python Salt CVEs — CVE-2020-11651 & CVE-2020-11651
-
Tomcat Server — CVE-2020-9484
-
WebLogic Remote Code Execution (RCE) — CVE-2019-2725
-
ApacheStruts2 — CVE-2019-0230
-
ApacheStruts2 — CVE-2018-11776
-
Jenkins XStream — CVE-2016-0792
Contrast studies new exploits and CVEs to enhance/harden the Protect rules for real-time protection (e.g., improved JDNI rules and added ClassLoader Manipulation detection).
Large insurance company |
|
Affinity membership group |
|
$120B global medical devise company |
|
Secure your apps and APIs from within
Schedule a one-to-one demo to see what Contrast Runtime Security can do for you






