Detect application and API vulnerabilities in third-party software and libraries at runtime.
Try Contrast
of modern applications rely on third-party libraries 1
of applications use open-source components. 2
of security vulnerabilities originate from third-party libraries. 3
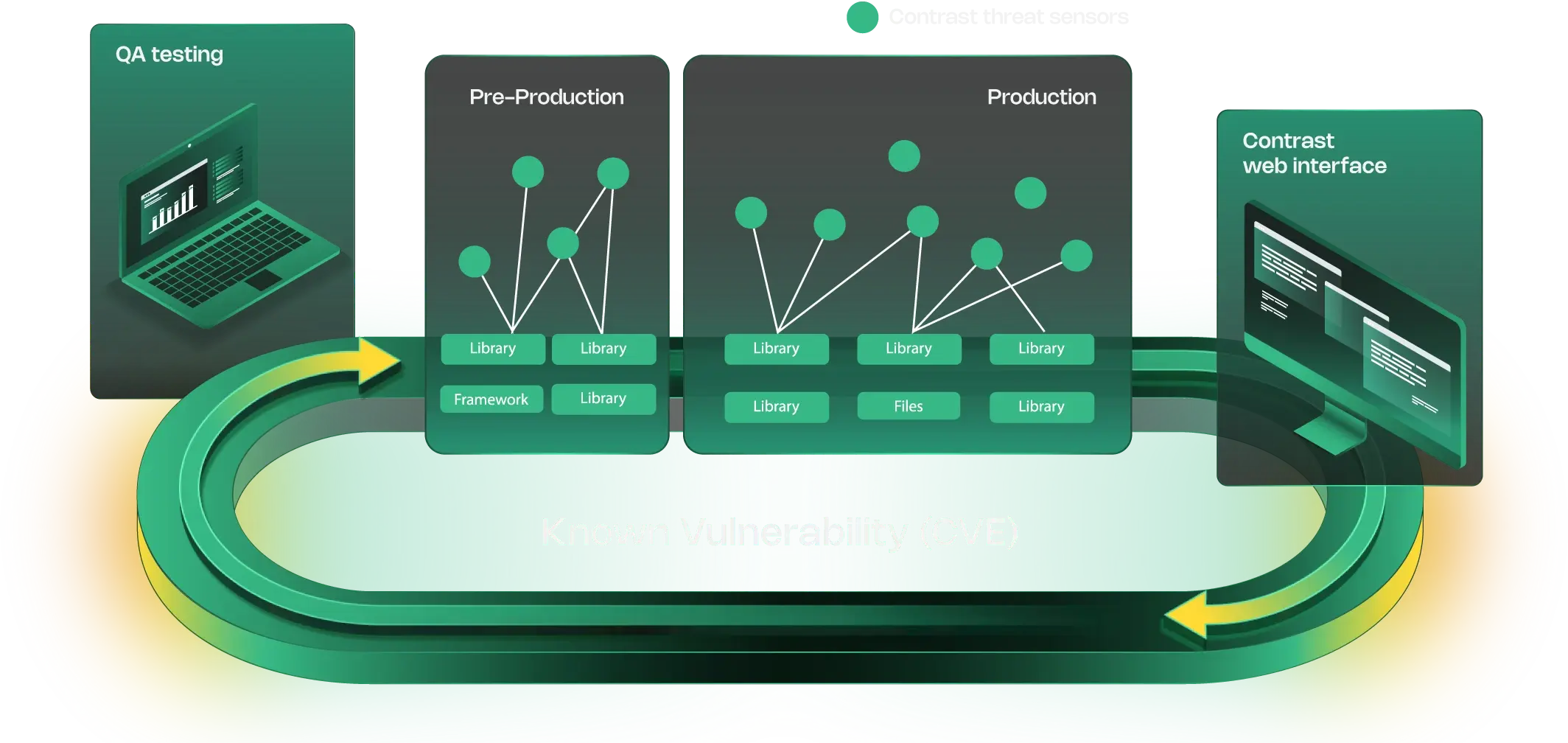



Support for over 30 languages and frameworks for static code scanning.
Learn MoreFind weaknesses in open-source code used in applications that hackers exploit.
Enables developers to fix issues before releasing applications into production.
Avoid accidentally violating license rules by helping developers track and manage third-party licenses.
Focus on building software without worrying about liabilities from use of open-source components.
Reduce the overhead of finding and fixing vulnerabilities by providing clear recommendations.
Integration to analyze a project's dependencies for vulnerabilities and detect vulnerable libraries.
Help developers follow processes and ensure that applications remain secure.

Managed runtime security powered by the people who built it
Learn more