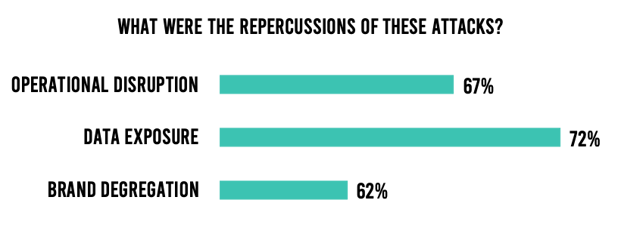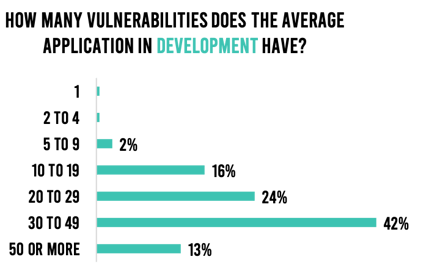Findings and Insights from Contrast Security’s 2020 State of DevSecOps Report
I recently spoke with the CISO of a global Fortune 500 company about his team’s renewed focus on application security in 2020. When I asked him what drove this decision, he indicated external reports such as Verizon’s Data Breach Investigations Report—which showed that breaches tied to an application vulnerability more than doubled over the past year—along with internal intelligence from the company’s security operations center (SOC).
Application Security Ratchets Up in Priority
Such a significant increase should provide cause for pause for many CISOs and other C-suite leaders charged with application security. Why did we see such a large jump in the past year? What type of risk does this pose? And what can be done about it?
These were some of the questions that we had in mind when we commissioned the survey for our State of DevSecOps Report earlier this year. We surveyed 250 development, security, and operations professionals globally to attain their insights on various issues related to DevSecOps. The latest research findings from Verizon were not only corroborated but accentuated. An astounding 95% of survey respondents admitted that their organizations had experienced at least one successful application exploit in the past 12 months—and 61% of them reported three or more (Figure 1).
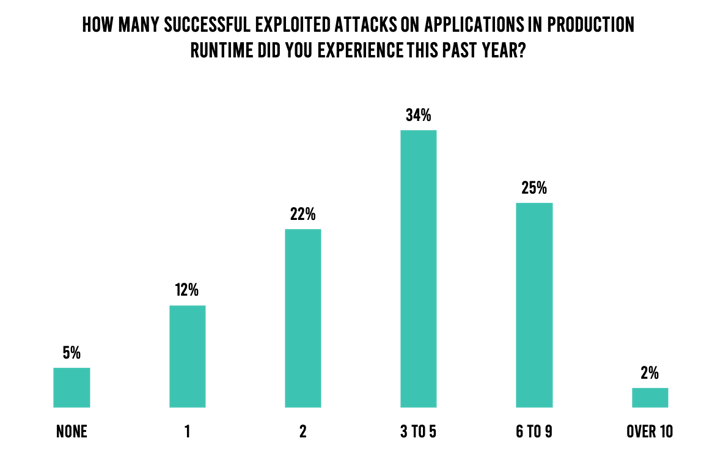
Figure 1. Respondents who experienced a successful application exploit in the past year.
Repercussions of Successful Application Exploits
Wanting to know more specifics on these successful exploits, we asked survey respondents to spell out the actual repercussions of these successful exploits. 72% of them said they lost critical data. While we didn’t ask them to delineate data types such as intellectual property (IP) or personally identifiable information (PII), this level of data leakage can have serious repercussions. Another 67% indicated they experienced an operational disruption, and 62% said they saw brand degradation (Figure 2). These are all alarming numbers, and I’m sure provide the CISO with whom I spoke further substantiation that his team’s recent investments in application security are warranted.
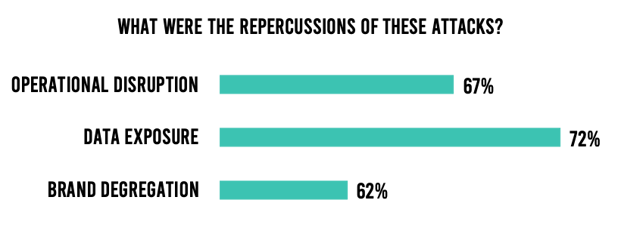
Figure 2. Repercussions of successful application exploits.
Seeking the Causes for the Increase in Successful Application Exploits
Now that we understand the problem, it is important to peel back the skin of the banana to reveal the causes.
More Applications in Development
As a starting point, there are a lot of applications in development—from enhancements to new ones—than a few years ago. The assertion of Microsoft CEO Satya Nadella last year is apropos: “Every company is now a software company.” The COVID-19 pandemic accentuated this new reality, and digital transformation only accelerated. A majority of survey respondents indicated they are investing more in DevOps initiatives than before the pandemic.
More APIs Communicating with Applications
Proliferation of application programming interfaces (APIs) is another area that is contributing to the problem. Various organizations recognize that APIs are a great way to extend new and enhanced services to customers, partners, and employees. For example, as part of its Digital Accelerator program, Charles Schwab doubled down on the development of APIs to extend new information and services to clients. In our survey, almost 9 in 10 respondents said they utilize more than 500 APIs across their applications (Figure 3). Despite the benefits of APIs, legacy application security tools struggle when it comes to securing them.
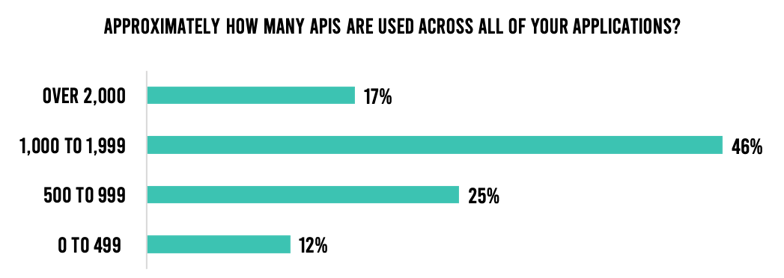
Figure 3. Number of APIs in use.
Push for Speed Accelerates Beyond Application Security
Survey respondents indicate they deploy code to production multiple times per week. One would assume this is perceived as good news and placates the need for greater business speed and agility. However, almost 8 in 10 respondents indicate they are under pressure to shorten release cycles further. And this number jumps when it comes to the C-suite: 90% of CEOs, CIOs, and CTOs report that their current rate of releases is insufficient. The end result is that security checks get skipped: 55% of organizations sometimes or occasionally skip security scans to meet deadlines (Figure 4). This makes sense; after all, developers are not measured based on security but the amount of code they write and release.
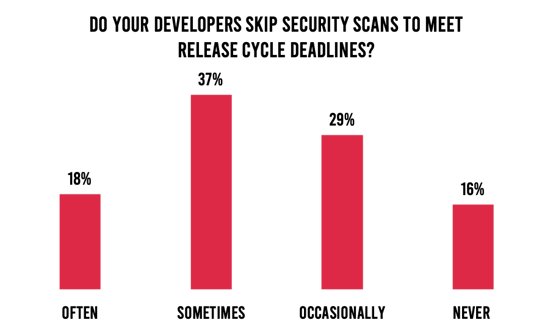
Figure 4. Frequency of security checks being skipped to meet release cycle deadlines.
Security Debt Compounds the Problem—Increases Risk
We have addressed this issue of security debt in past research reports and blog posts. The State of DevSecOps Report accentuates the problem once again. Organizations that fail to continuously address vulnerabilities early in development struggle to keep up and increase the likelihood that vulnerabilities will slip into production. Almost 8 in 10 respondents admit to 20 or more vulnerabilities in development in the average application. Over 99% say the average application in production has more than four vulnerabilities. If this doesn’t clearly articulate the problem, then nothing will do so (Figure 5).
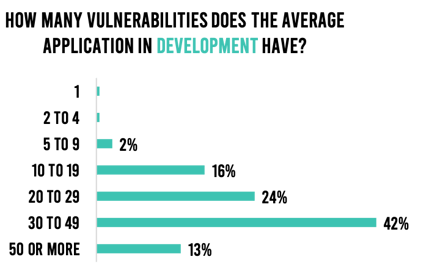
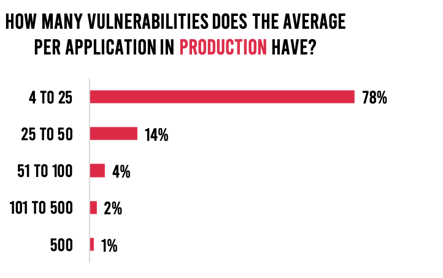
Figure 5. Average vulnerabilities in development and production.
Time To Find, Triage, Diagnose, and Remediate Vulnerabilities
Part of the problem behind security debt is the huge amount of time that it takes to find, triage, diagnose, and remediate vulnerabilities. For organizations that haven’t shifted their application security programs left, they compound the problem. They expend even more time trying to detect and remediate vulnerabilities than those that have shifted left. But even those organizations that have shifted left struggle. And when vulnerabilities slip into production, the risk becomes viable and a potential target for cyberattacks. Modern software development life cycles (SDLCs) demand application security that can scale to the speed of release cycles that happen daily or even faster. The reality is that traditional approaches cannot do so.
State of DevSecOps Report: Provoking Thought
The 35-page report contains a plethora of data on the above and other topics. Readers will want to register to attend this week’s webinar, “Why DevSecOps Is Challenged by Modern Software Development,” featuring three expert panelists from Delta Dental, Kaizen Gaming, and Contrast Security. We will be looking at some of the key findings from the report and discussing insights and recommendations from the panelists. Make sure to reserve your spot today.
Readers can also listen to the new Inside AppSec Podcast interview that I conducted with Contrast’s CTO and Co-Founder Jeff Williams, “State of DevSecOps Report: 95% of Organizations Experienced a Successful Application Exploitation in the Past Year.”