Contrast and NowSecure Discuss Application Security Challenges and Best Practices
In a recent webinar, “Accelerating DevOps with Autonomous Security Observability,” Brian Reed, chief mobility officer of NowSecure, spoke with Jeff Williams, co-founder and CTO at Contrast Security, on how autonomous security can power DevOps teams and take continuous integration/continuous deployment (CI/CD) pipelines to the next level. I highly recommend listening to the full webinar—it has many insights both for developers and security teams. In the following, I will tease out the highlights of their conversation and extract some key takeaways.
While Contrast focuses on application security for web applications, NowSecure specializes in protecting apps that run on mobile devices. In this conversation, Brian and Jeff discuss the unique challenges of mobile apps and their web-based back ends.
Brian, who has been working with mobile apps for 15 years, spends a lot of time talking to customers about mobile technology’s role in their digital transformations. He laments what he sees as a mismatch between the huge investment in securing software and the less-than-stellar security outcomes. For example, organizations spent $3.2 billion on application security in 2020 and are projected to spend $4.5 billion in 2024 (according to this Gartner report) and yet …
Jeff echoes those sentiments when he talks about web applications. Scanning the data from the tens of thousands of applications monitored by the Contrast Security Platform, Jeff found that almost all of them (96%) have at least one vulnerability; the average is 35 per web application! Vulnerabilities come from both custom and open-source code. Some of the latest research from Contrast Labs confirms his assertion. A few highlights include:
Takeaway: Vulnerabilities put applications at risk; few are entirely safe.
Due to the adoption of DevOps and Agile development processes and a plethora of open-source libraries and application programming interfaces (APIs), development teams are “steamrolling” their applications through the pipeline, as Brian puts it. As a consequence, both the front end and the back end of applications are riddled with vulnerabilities that hackers readily exploit.
Security teams need to detect these vulnerabilities, but Jeff says security is still somewhat in the dark ages. Beyond the manual intervention required for tools like code scanners and modifying web application firewalls (WAFs), which are significant problems themselves, legacy application security tools have a variety of challenges. Here are just a few:
Takeaway: Application security tools that take too long to work and require manual intervention thwart efforts to deliver secure, high-quality mobile/web applications.
According to Brian, developers and security teams have a common interest in overcoming these challenges. Contrast and NowSecure agree that the best approach is to build autonomous security observability into the application code—for both web-based and mobile application security.
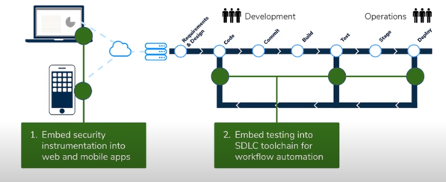
For security instrumentation, Jeff explains that when an application starts up, an agent automatically places sensors at specific locations within the application code (including libraries, frameworks, and application servers). As the application runs, the sensors observe how the binary (runtime code) responds to various inputs and requests and can spot potentially malicious behavior.
By embedding instrumentation into the application itself, as shown on the left side of the illustration above, you get much better visibility into what’s going on inside the code. Instead of looking at the HTTP traffic or the source code, which is an abstraction of what the application is doing, you can monitor it while it’s actually running, so it’s significantly more accurate. You can see the transactions and all the security-relevant activity. At the same time, you can detect application vulnerabilities without having to exploit them.
Takeaway: Making application security observable enables you to make informed decisions about risk, without incurring risk.
In addition to accuracy, instrumentation delivers speed and scalability. By embedding instrumentation-based security into the development pipeline (see the right part of the illustration), you don’t have to disrupt development; testing just becomes part of the process. Meanwhile, security experts stop being part of the process, so they don’t hold things up. Instrumentation-based application security can run across hundreds and thousands of applications in parallel, rather than scanning one application at a time.
Takeaway: Empower developers to do security testing as part of their normal pipeline. This keeps security experts out of the critical path and gets clean code to production faster
Brian says for mobile apps, it’s important to have visibility into what happens in production, especially because of all the open-source libraries that these apps use. The average mobile app uses dozens to a hundred APIs, which are dynamically loaded, so you wouldn’t see their effect just by scanning the source code.
With autonomous security observability in production, you can see what’s actually going on, and better yet, you can block it, which you wouldn’t be able to do with a perimeter-based tool like a WAF. Contrast calls this runtime application protection and observability.
The real value of instrumentation-based application security is that it ties all the security testing together, eliminating the silos created when different teams perform source-code scans, penetration tests, software composition analysis (SCA), and so on. Automating this instrumented security reduces friction in the pipeline, while delivering more accurate feedback, increasing both the velocity and scale of application development, ultimately resulting in great DevSecOps ROI.
Takeaway: Removing the roadblocks to security best practices increases the chance that everyone will adopt them, creating a culture of security across the organization.
In the webinar, both Jeff and Brian cite two real-world case study examples. Jeff describes the case of a Fortune 100 insurance company that was spending millions on security annually, but its experience of application security was anything but positive; developers found that it impeded every application they were trying to build. By deploying Contrast’s Application Security Platform on its application server, the Fortune 100 insurance company instrumented about 750 applications. As a result, the company eliminated over 10,000 vulnerabilities, fixing half of them in less than a week. For incumbent SAST tools, it takes about four months to achieve the same results. The insurance company also reduced the number of open-source libraries with known vulnerabilities to 17% of the industry average, and prevented over 10,000 attacks per month.
To illustrate mobile app security, Brian relates the case of a coffee company with typical challenges such as slow pipelines, slow feedback, and manual testing. With NowSecure, within 120 days, the company went from a quarterly to a monthly release cycle—and it is aiming for a two-week agile cycle. It also realized an 80% improvement in security test coverage, as well as a 30% reduction in breach potential. Finally, the client reached a 10x boost in team productivity and a 10x gain in predictability of secure release dates.
The Contrast Application Security Platform protects 30,000 applications in some of the world’s largest companies, while NowSecure has analyzed millions of applications used by organizations with industry security benchmarks. Watch the webinar—”Accelerating DevOps with Autonomous Security Observability”—to get the full story on autonomous security observability, as well as access to free informational resources from both companies.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.