August 10, 2020
The most shocking aspect of this transformation is that it took place in a matter of a few weeks or months. While digital transformation was already making an indelible imprint on businesses, the extent to which we have come in a matter of a few months would have taken years to transpire without COVID-19 and ubiquitous business implications.
Recognizing the digital engagement that applications offer, enterprises doubled down on existing application development programs and rapidly launched new ones. In order to achieve the agility, speed, and efficiencies needed to capitalize on these new digital initiatives, Agile and DevOps are crucial. A recent Agile report, published by Digital.ai, finds that 43% of organizations have increased their reliance on Agile in the wake of the pandemic, with 15% indicating it increased significantly. At the same time, the pandemic is propelling DevOps: 33% of organizations increased or expanded DevOps adoption, with 55% indicating they plan to increase their use over the next year.
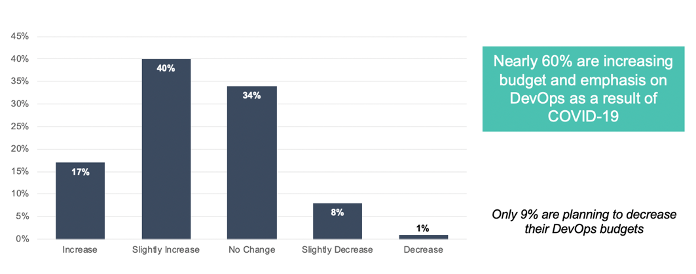
Contrast Security uncovered similar findings in a study we conducted in late June. Only 9% of respondents plan to reduce their DevOps budget, with almost 60% planning to increase or slightly increase their budget and resources for DevOps.
This is good news for developers and the organizations for which they work. But with this expanded charter also comes additional challenges. Many enterprise development teams did not work remotely before the pandemic. And like millions of other professionals, developers were not set up to work and code from home. Collaboration with other developers looks different. Testing, quality assurance (QA), bug tracking and resolution, and other development functions change as well.
The increased focus on Agile and DevOps also ratchets up the amount of pressure on development teams. Under pressure to move revenue streams online and to engage with customers, partners, and employees digitally, development teams are under greater pressure to write code faster and accelerate release cycles. The outcome is that developers are working harder and longer than ever before. A recent study by GitHub reveals that developers are working up to an hour longer per day since the pandemic started—and this includes working more over the weekends. When a comparison of 2019 to 2020 is analyzed, it shows nearly all developer activities are up—pull requests, pushes, and issues created per active user.
Exacerbating the situation is that finding and hiring developers with Agile and DevOps experience is a challenge. A survey by the DevOps Institute found 58% of respondents indicate they struggle to do so—and a little less than half have difficulty keeping them.
One final note regarding the use of open-source frameworks and libraries is worth mentioning as well. With application development on the rise, the number of open-source repositories created this year has grown accordingly—nearly 28% in March over the past year.
When these factors are combined with the fact that some developers may not be fully acclimated to writing code while working from home, the likelihood that vulnerabilities will creep into the software development life cycle (SDLC) increases. For those organizations waiting for the COVID-19 vaccine and for things to “return to normal,” they need to think again. Studies over the past several months indicate that neither organizations nor individual workers want to reconvene in centralized offices five days a week, eight hours a day.
Unfortunately, while vast segments of the global economy went into lockdown, cyber criminals did not do the same. Their attacks focused on both consumers and businesses—and have reaped rewards on both fronts. “Catastrophic events act as beacons to fraudsters and threat actors,” explains Samuel Willoughby, managing director and practice leader of investigations at Aon Cyber Solutions.
A primary area where cyber criminals are focusing their attention is the expanded attack surface. It is not simply one entry point on the attack surface but multiple entry points. Enterprise networks are simply easier to access from employee home networks and devices. Once they have gained access, bad actors are able to move laterally across the network and gain access to data repositories, systems, and applications.
Phishing and spear-phishing attacks have also skyrocketed. One study from a couple of months ago found that phishing-related attacks jumped an astounding 667% since January when the pandemic started.
Applications—both Software-as-a-Service (SaaS) and those developed in-house or via an outsource provider—are also in the crosshairs of cyber criminals. Data from Contrast Labs’ “Application Security Intelligence Report: March-April 2020” uncovered potential spikes in attacks that could be attributed to an increased focus on application attack vectors by cyber criminals. Cyber criminals continue to get more sophisticated in their application attack techniques. For example, bad actors that hacked an Asian media agency requested ransom from the firm to reveal the vulnerabilities used in the attack.
Application vulnerabilities in May-June increased to 98% over 97% in the March-April report and 96% over the past year. While these percentage increases seem relatively small, full percentage-point changes at volumes this high can be dramatic. Even more alarming is the increase in serious vulnerabilities, where one in three applications were found to contain at least one. This is a 27% jump from March-April. Albeit it is difficult to say if the above challenges developers are facing while writing code from home are a direct cause, one can speculate that they are a contributing factor.
May-June also reveals problems with vulnerabilities in Java applications, with 39% containing a serious vulnerability. The highest ratios of serious vulnerabilities per Java applications were broken access control (24%) and cross-site scripting (XSS) (23%). The report reconfirmed an XSS trend we saw at the beginning of the year, where for the fifth consecutive month it was found in fewer than 20% of applications (whereas it was over 20% throughout 2019). This might be due to changes in programming practices, where developers prefer to use application programming interfaces (APIs) and JavaScript in the browser instead of generating HTML on the server side. If this continues, and there is no indication to suggest otherwise, the severity of XSS vulnerabilities may continue to decrease.
The overall number of attacks hitting applications on average per month decreased significantly in May-June. And while the number of attacks is down, the number of attacks hitting a true vulnerability held steady at 3%. This is a likely indication that cyber criminals are simply becoming more targeted in their attacks.
The number of applications experiencing SQL injection attacks spiked. More than four in five applications saw a SQL injection attack in May-June. And with more than twice the number of applications with SQL injection vulnerabilities (7% versus the overall average of 3%), this trend should be a red flag for those tasked with application security. Media reports certainly indicate that SQL injection vulnerabilities were exploited during the time frame, with remote learning and operational technology as prevalent targets.
.NET applications came into greater focus for bad actors in May-June. Five vulnerability categories in .NET saw double-digit increases in the percentage of applications impacted—and three of them experienced increases between 25 and 40 percentage points. Further, only one application attack vector for .NET decreased during the same time frame. For development teams writing and deploying code in .NET, they need to heed these increases and ensure they have the right application security testing (AST) protocols in place to ensure the code is free of vulnerabilities.
The May-June report contains a number of other highlights and insights. Threat intelligence reports like our “Application Security Intelligence Reports” are valuable compasses for security, development, and operations teams interested in staying on top of application vulnerability management and attack trends.
Many of the above areas from the report are covered in a new Inside AppSec podcast. For the entire report, readers can download a copy today:
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.