By Jeff Williams, Co-Founder, Chief Technology Officer
August 4, 2021
Application Security Observability Report Shows Developers Write More Secure Code the More They Use the Contrast Platform
One way that organizations can speed their development cycles while improving the security of their applications is for developers to learn how to avoid specific vulnerability types as they write custom code. This results in fewer vulnerabilities over time and presents organizations with the opportunity to reduce existing security debt.
But this is easier said than done. Developers are overwhelmed with aggressive release cycles and do not have the time to take months off work to attend comprehensive security training. And it is difficult to teach these concepts in a theoretical classroom setting anyway. Equally challenging is figuring out a way for corporate trainers—or even engineering managers—to teach the concepts using projects currently in progress.
Fortunately, analysis of telemetry data from all the applications protected by Contrast Assess, Contrast Protect, Contrast OSS, and Contrast Scan shows that our customers are improving the security of their coding after being on the platform for a relatively short time. More on that later, but first some discussion of vulnerabilities and attacks in general—which illustrates why this is such an important achievement.
Per our just-released 2021 Application Security Observability Report, a significantly higher percentage of applications had serious custom code vulnerabilities this year than last year—34% this year compared with 26% last year. Overall, 13% of applications have one or two serious vulnerabilities, while 3% have more than 100.
Just as concerning is the percentage of all vulnerabilities that are serious (High or Critical)—39% this year compared with 28% last year, a 39% increase! A greater share of serious vulnerabilities means increased risk for organizations and greater urgency to speed up remediation.
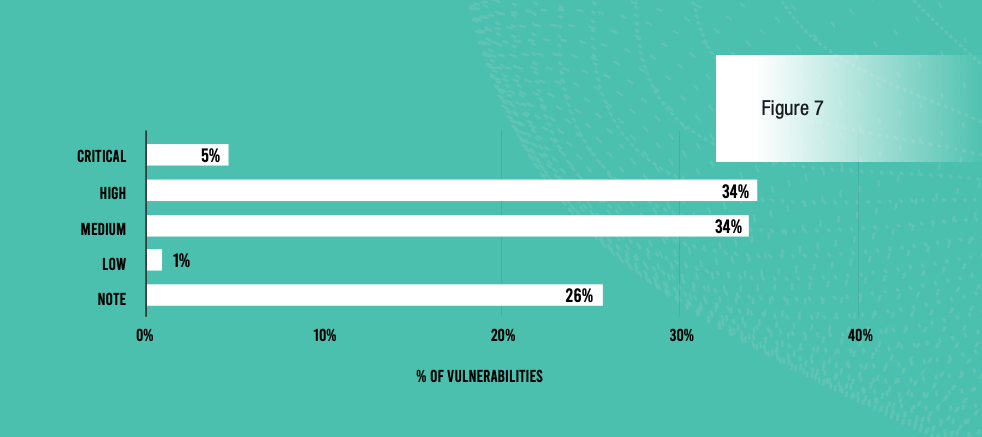
Nearly 4 in 10 vulnerabilities identified in the past 12 months were High or Critical.
Broken access control and cross-site scripting (XSS) continued to be the top two vulnerability types in terms of the percentage of applications they impact, and both impacted 18% of applications—a significantly bigger share than last year. Broken access control garnered a 35% increase, while XSS saw a 20% jump. Also noteworthy—and a cause for concern—was the percentage of applications with insecure configuration vulnerabilities, which quintupled from 1% to 5%.
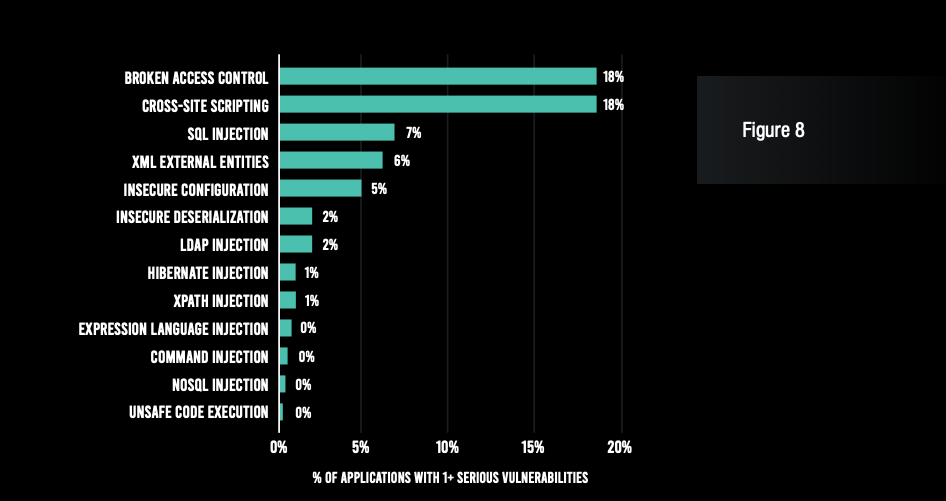
Broken access control, cross-site scripting (XSS), and insecure configuration vulnerabilities impacted a significantly larger share of applications this year.
Notwithstanding, the risk presented by a vulnerability depends heavily on the impact it would have on the business if it were exploited. Contrast Labs rates each vulnerability type as high, medium, or low impact. For example, SQL injection is high impact because it can result in a full takeover of a database. When looking at the prevalence of higher-impact vulnerabilities, it is possible to create a matrix of likelihood and impact like the one below.
Given these ratings, it is instructive to see which medium and high-impact vulnerabilities have medium and high prevalence. The three boxes closest to the upper left in the illustration below—high likelihood/high impact, medium likelihood/high impact, and high likelihood/medium impact—covered 40% of vulnerabilities this year compared with just 28% last year. This should get the attention of anyone involved in application security. Along with the higher proportion of vulnerabilities that are serious, these findings accentuate the need to reduce security debt and prioritize remediation according to risk.
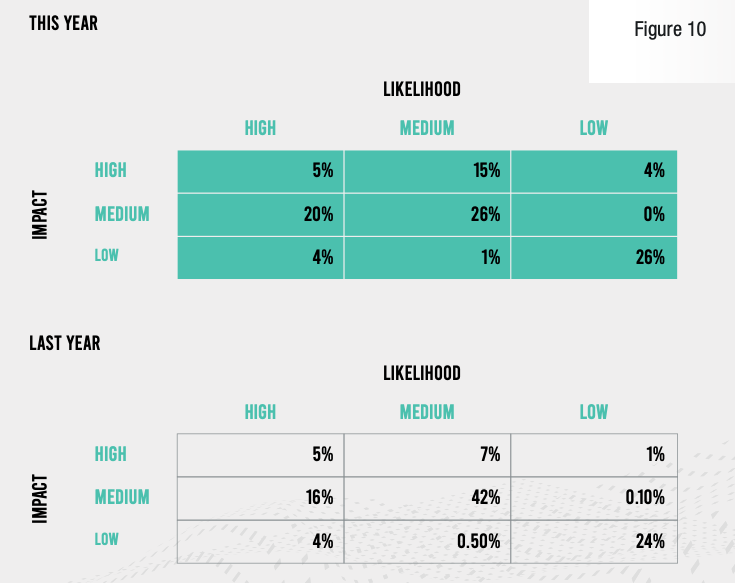
A combination of high likelihood/high impact, medium likelihood/high impact, and high likelihood/medium impact vulnerabilities increased this year.
Looking at attack data from our customer base, the typical organization was pummeled with 25,343 attacks per month over the past year, so the volume remains relentless. But an even smaller share of those attacks was viable—that is, hit an existing vulnerability—than last year. In fact, the viability rate was cut in half, from 2% to 1%.
While this is good news in the short term, the 99% of attacks that were “probes” are not totally useless to attackers: Information gleaned from them can help bad actors narrow down the spots on an attack surface that are most vulnerable.
In terms of attack types, several impacted a significantly higher share of applications than last year, including SQL injection, broken access control, XSS, command injection, and expression language (EL) injection.
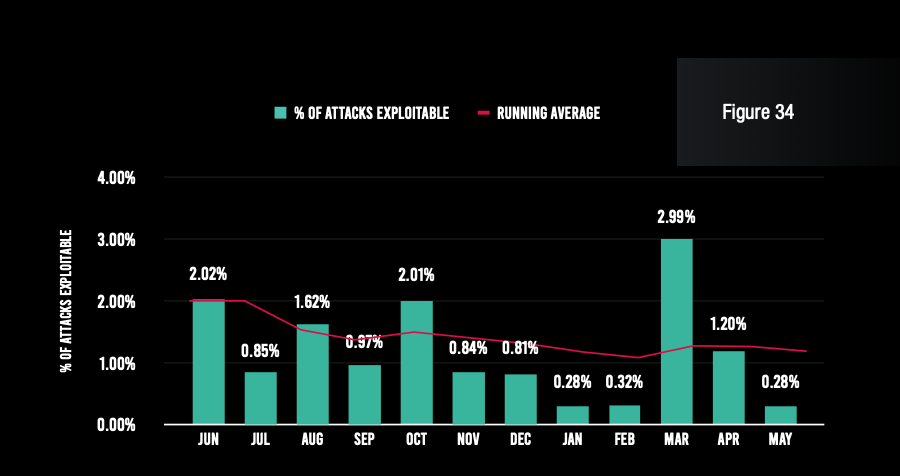
The running average for the percentage of attacks that were viable steadily declined, reaching 1% for the past 12 months.
Now, back to the idea of helping developers learn to write more secure code. Fortunately, there is some good news on that front. Overall, our findings indicate that the longer an application is on the Contrast Application Security Platform, the fewer new vulnerabilities it reports. In the first two months, the typical application sees 12 new vulnerabilities—6 of them serious. After a year, a piece of software sees just one non-serious vulnerability.
We call this the vulnerability escape rate (VER), and it declines by 92% over a 12-month period. It is a subset of the defect escape rate (DER), a common metric used to measure the number of defects caught post-production compared with those caught in pre-production by QA teams and developers.
The reduction in VER is the result of the immediate feedback that developers receive from the Contrast platform when a vulnerability occurs, along with contextual information on how to fix it. This provides contextual, on-the-job security training for developers, helping them to avoid the same mistake in the future. After a year, most developers will have gone through this process for most major vulnerability types, resulting in much more secure custom code because developers learned how to avoid a mistake just after they made it.
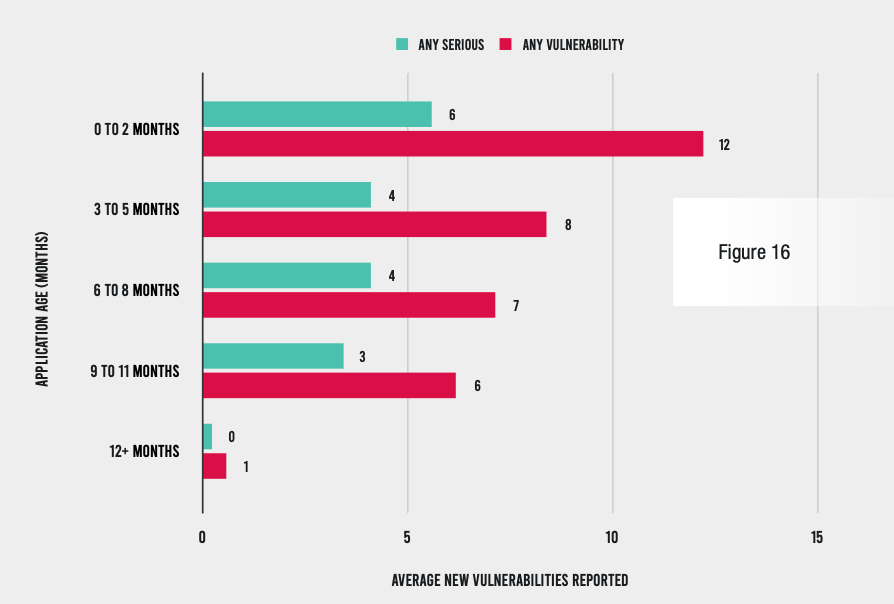
The vulnerability escape rate (VER) declined from 12 in the first two months to just 1 after 12 months.
The vulnerability and attack data in the 2021 Application Security Observability Report reveals the advantage that users of the Contrast Application Security Platform have when it comes to getting on top of vulnerabilities. Important takeaways include:
This blog post just covers a portion of the findings of Contrast’s flagship annual report on the state of application security. I hope you will download and read the entire report. Other highlights include:
REPORT: 2021 Application Security Observability Report
PODCAST: Key Insights on Application Vulnerabilities and Attacks (New Report)
WEBINAR (Register): Key Insights and Benchmarks From Contrast’s 2021 Application Security Observability Report
VIDEO: Introducing Contrast’s 2021 Application Observability Report
.jpg)
Jeff brings more than 20 years of security leadership experience as co-founder and Chief Technology Officer of Contrast Security. He recently authored the DZone DevSecOps, IAST, and RASP refcards and speaks frequently at conferences including JavaOne (Java Rockstar), BlackHat, QCon, RSA, OWASP, Velocity, and PivotalOne. Jeff is also a founder and major contributor to OWASP, where he served as Global Chairman for 9 years, and created the OWASP Top 10, OWASP Enterprise Security API, OWASP Application Security Verification Standard, XSS Prevention Cheat Sheet, and many more popular open source projects. Jeff has a BA from Virginia, an MA from George Mason, and a JD from Georgetown.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.