WAFs have Key Limitations
We consistently hear growing frustrations from customers about their WAF implementations and have made a commitment as a software security company to help them address those limitations, whether they continue using their WAF or not. The limitations we constantly hear are:
- WAFs miss “hard to signature” attacks - (e.g., XXE, Regular Expression DoS, Java Deserialization)
- Their SOC is overwhelmed with alerts from the WAF and do not know what to prioritize
- They see no data beyond the HTTP request, so it is hard for the SOC or Application Security to get context about a specific piece of suspicious activity
- Constant tuning – WAFs struggle in environments with frequent code changes. We see this with customers practicing agile / lean development and DevOps and doing regular code deploys. Web application developers are incentivized to push new code as often as possible. Code changes and new functionality often violate existing policies, so unless someone updates the whitelist of approved application requests for every application change, a WAF will block legitimate requests.
- Difficult to scale to cloud deployments. Some of our key customers approached us to support the move of their core apps into public cloud infrastructure. Some customers used a WAF that did not offer a suitable cloud deployment. In other cases, the customer could not scale their WAF policies easily with their application. With each instance or code change, they had to modify rules manually or deploy additional devices.
Our customers approached us as a path to address these limitations and strengthen the security around their production applications.
Contrast Protect + WAF = Full Application Security Monitoring
Working with our customers, we crafted an Application Security Monitoring (ASM) solution that will allow everyone to get the most out of their WAF investment without adding head count.
Application Security Monitoring with Contrast Protect + WAF
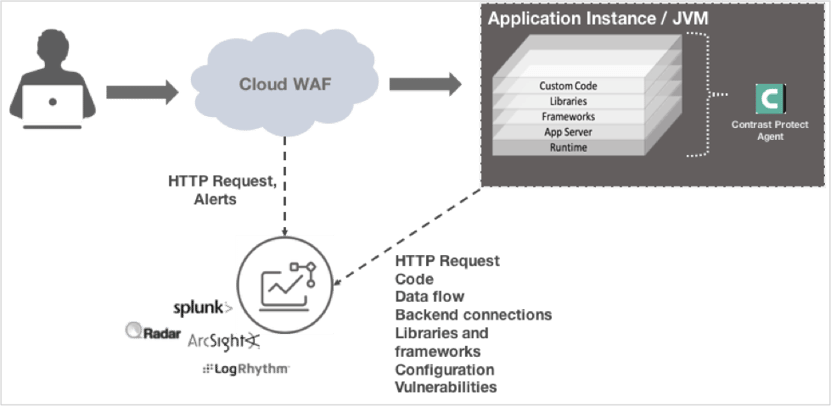
Benefits: Specifically, we complement our customers’ WAF solution as follows:
- “Hard to signature” & WAF by-pass attacks: There are application layer attacks that WAFs struggle to pick up. These include, but are not limited to: XXE, Regular Expression DoS, Java Deserialization. These include the recent exploits discovered related to Apache Struts 2 – the source of the Equifax breach. At a broader level, WAFs are constantly a step behind any exploit against a regular expression based framework like Struts 2. Contrast’s ASM solution covers customers out of the box fundamentally because of what we inspect within the application and how we do just-in-time protection.
- Correlation with WAF alerts: Contrast ASM’s “in-app” approach is fundamentally more accurate. This results in fewer, but more critical alerts with deeper information and actionable guidance on how to fix. This implies less alert fatigue for the SOC and faster response and remediation.
- “Attack” vs “Probe”: Contrast is able to differentiate between a truly exploitable attack and “spray and pray” attempt at an exploit. For example, we see attempts to exploit the Equifax Struts 2 vulnerability (CVE 2017-5638), even though we do not use Struts 2. Contrast ASM will identify this attempt as a “probe” that can never be exploited. This enables Application Security teams to de-prioritize or ignore WAF alerts that arise from probes.
- Open source & library CVE protection: Contrast ASM is able to inventory and assess the risk of all the open source libraries used by an application. This implies that the application is now fully protected against vulnerabilities in custom code as well as libraries without touching WAF rules. Without Contrast, the alternative would be for the Application Security team to manually inventory (or use a Software Composition Analysis tool) to identify all libraries and frameworks used by the application and then work with the WAF admin to create specific rules for each vulnerability.
- Line-of-code as well as full-exploit detail: With our “in-app” instrumentation, we can go deeper into the stack. This allows you to:
- Protect the full application stack
- Gather detailed information about an attack as it happens
- Block the attack instantly
This makes it easier to understand context behind suspicious activity, quickly understand the root cause, and remediate faster.
For a full list of data points Contrast ASM collects and reports click here >>

Key Questions to Ask
If you like your WAF, but would like to maximize the value of your investment without adding headcount, I would ask the following questions:
- What do I know about the state of my production app?
- Am I protected against the vulnerability that was used at Equifax?
- How am I going to protect my apps that move to public cloud infrastructure?
- Is our SOC and Incident Response effective during application attacks?
