By David Lindner, Chief Information Security Officer
October 18, 2022
There’s a new Common Vulnerability and Exposure (CVE) getting some buzz: Apache Commons Text, which is exploitable via the interpolation function CVE-2022-42889. The vulnerability, which affects versions 1.5 to 1.9, was announced on Oct. 13 on the Apache dev list and was originally reported by GitHub Security Lab Security Researcher Alvaro Muñoz, who discussed the vulnerability on Twitter.
Some initially thought this vulnerability was similar to Log4Shell, but the Contrast Security Labs Team’s research has determined that it’s not nearly as exploitable as perceived, given that very few people use the interpolator function of the library. Additionally, recent Java engines do not enable the Nashorn engine — required for the exploit — by default. However, the Java Nashorn engine requirement can be circumvented if your project includes dependencies that enable engines like Groovy or JEXL.
The vulnerability is being largely compared to Log4Shell for a few reasons. It’s found in an open-source library that is a very commonly included dependency in the software supply chain. The library itself is used for formatting text. Having a high-impact remote code execution (RCE) CVE found in it can be shocking. It will likely impact a wide variety of software applications that use this library without developers’ awareness.
CVE-2022-42889 is very similar to the prior CVE-2022-33980, which affected Apache Commons Configuration versions 2.4 to 2.7. Both of the CVEs were reported in March 2022 (Configuration, Text).
Exploitation of Apache Commons Text requires using the interpolation function in your code base. In order to check if you are doing so, a developer can look for usage of StringLookupFactory.INSTANCE.interpolatorStringLookup().lookup() or StringSubstitutor.createInterpolator().replace().
Invocation of these functions will utilize the vulnerable parts of the Apache Commons Text library; thus, it would be dangerous for them to accept user input.
For those using Apache Commons Configuration, exploitation also relies on the interpolation functionality. In such cases, be on the lookout for use of org.apache.commons.configuration2.interpol.ConfigurationInterpolator.
If your organization has direct dependencies on Apache Commons Text or Apache Commons Configuration, you should upgrade them. The fixed version of Apache Commons Text is 1.10.0. The fixed version of Apache Commons Configuration, where script interpolation is disabled by default, is 2.8.0. You should also review your software to see if Apache Commons Text and Apache Commons Configuration interpolation is in use and whether it can be avoided.
As of last night, Oct. 17, this CVE seems to have been overhyped. Most systems using the vulnerable library aren’t using the vulnerable class. A quick search on GitHub shows that very few open-source projects use Apache Commons Text interpolation. Also, a quick search shows that very few open-source projects use Apache Commons Configuration interpolation.
Those that are using the vulnerable class/method likely won’t be accepting data from user-supplied input.
This CVE probably won’t amount to much, as it's not like Log4Shell: The Log4j issue was much more exploitable, and the library in question — Log4j — was widely used, with ubiquitous applications accepting and logging user-controlled input. That input could then easily trigger the Log4j exploit, far more easily than CVE-2022-42889 or CVE-2022-33980 can be triggered. In contrast, the commons-text library is ubiquitous, but the vulnerable component is not commonly used.
Initial analysis shows Contrast Protect blocked the attack providing zero-day protection without any changes with Object-Graph Navigation Language (OGNL) rules enabled. Contrast Labs will continue its analysis in order to confirm this more broadly. For now, customers can update their libraries and look for the previously mentioned vulnerable classes to determine if they may have a vulnerable path by examining the class usages within the Contrast Platform for the commons-text library, as seen here:
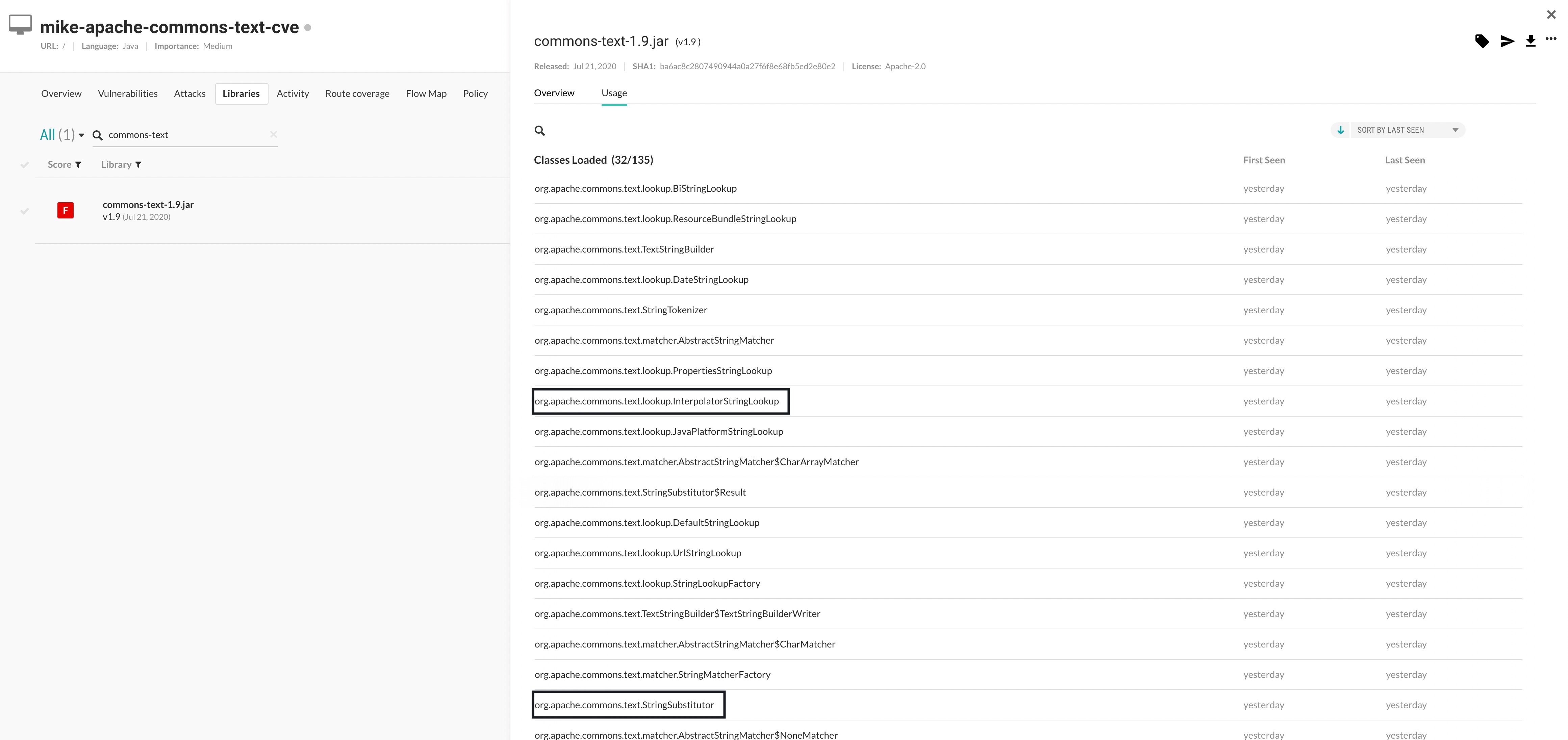
Contrast’s software-as-a-service (SaaS) server — TeamServer — does use the Apache Commons Text library, but we do not use the interpolation class. TeamServer has been updated to the newest version of commons-text to 1.10 as of Sept. 29, 2022.
Enterprise on Premise (EOP) — a local install of a Contrast server for customers that want more control of their data — uses the Apache Commons Text library, but we do not use the interpolation class. EOP version 3.9.8 is already using the fixed version 1.10 of commons-text, and the previous version of EOP, 3.9.7, is using the vulnerable version 1.9 of commons-text. However, we are not using the vulnerable components, so customers on older versions of EOP should not be concerned.
The Java Agent uses the Apache Commons Text library for test cases, but we do not use the interpolation class. We are in the process of updating the commons-text library to 1.10, and an updated agent will be released next week.
Contrast will continue to monitor the situation and will keep customers informed as more details become known, and/or if the severity of this vulnerability changes.

David is an experienced application security professional with over 20 years in cybersecurity. In addition to serving as the chief information security officer, David leads the Contrast Labs team that is focused on analyzing threat intelligence to help enterprise clients develop more proactive approaches to their application security programs. Throughout his career, David has worked within multiple disciplines in the security field—from application development, to network architecture design and support, to IT security and consulting, to security training, to application security. Over the past decade, David has specialized in all things related to mobile applications and securing them. He has worked with many clients across industry sectors, including financial, government, automobile, healthcare, and retail. David is an active participant in numerous bug bounty programs.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.