Contrast Labs' analysis of real world application security data from March 2018. We're going to change it up a bit this month by expanding our coverage to include:
Observations: Vulnerabilities
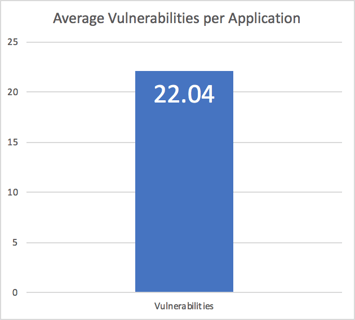
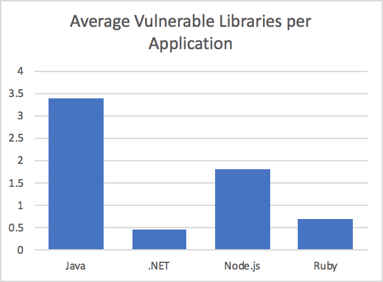
Table 1 - Top Custom Code Vulnerabilities by Language
| .NET | Java | Node.js |
| log-injection | reflected-xss | unvalidated-redirect |
| event-validation-disabled | log-injection | hardcoded-key |
| compilation-debug | sql-injection | hardcoded-password |
| request-validation-disabled | redos | reflected-xss |
| max-request-length | trust-boundary-violation | cache-controls-missing |
| reflected-xss | crypto-bad-mac | clickjacking-control-missing |
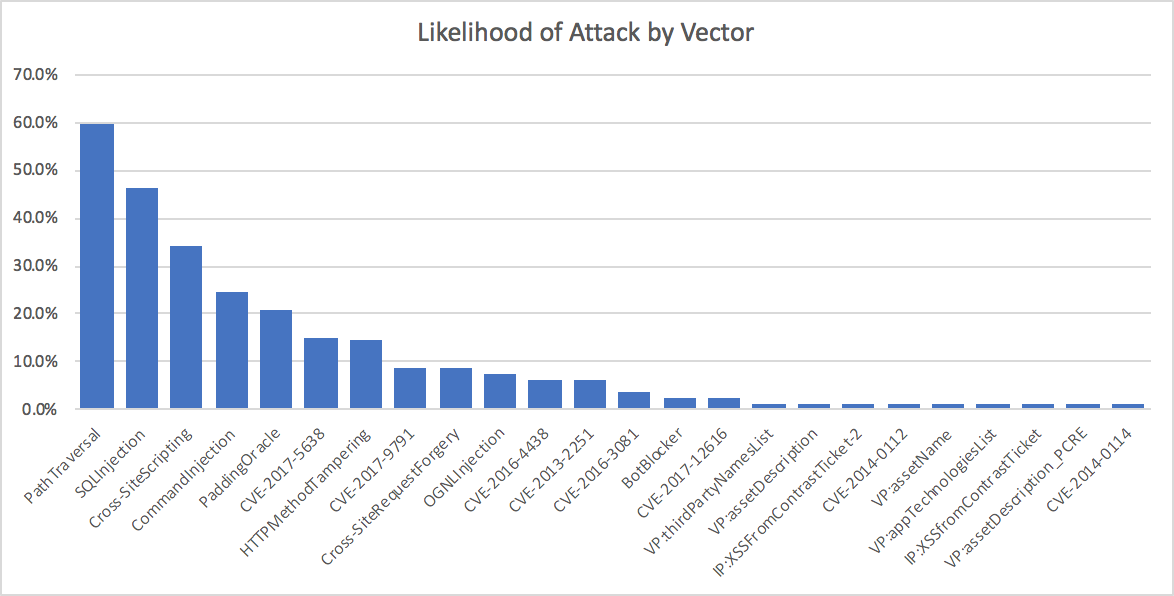
Observations: Attacks
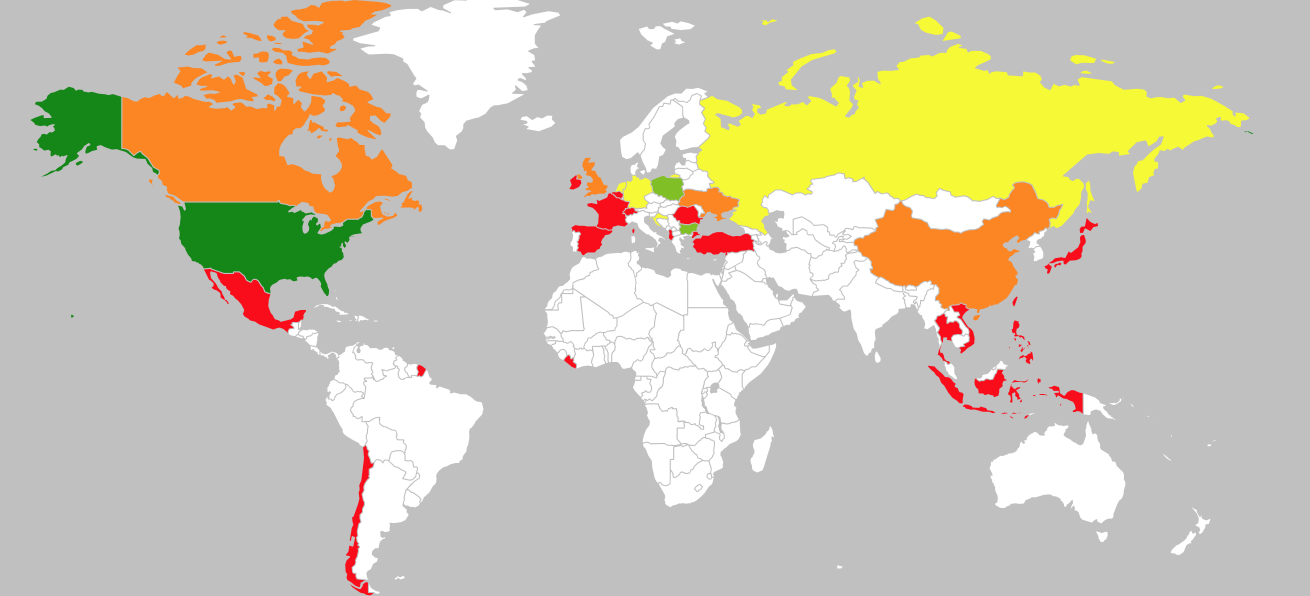
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.