This report summarizes Contrast Labs' analysis of real world application attack and vulnerability data from September 2019. It utilizes data from attacks that Contrast Security observed over the previous months and highlights the key trends found.
Developers, product owners, AppSec, and security engineers can use this information to better understand application security threats, adjust security controls, and improve their security posture.
Through reading this report on a monthly cadence, AppSec teams can gain a better understanding of the possible types and origins of attacks and attackers.
Visit our website to learn more about how Contrast Security continuously measures both vulnerabilities and attacks in parallel across your application portfolio.
KEY OBSERVATIONS
- The most prevalent serious vulnerabilities across the applications we observed were Cross-Site Scripting, XML External Entity Injection, and Cross-Site Request Forgery.
- Contrast Security saw a 40% increase in total attacks compared to August, returning to July levels.
- 1% of these attacks were connected to a vulnerability within an application, representing a .7% decrease from last month. The other 99% were probes and did not connect with a corresponding vulnerability within the target application -- a striking fact for security teams using tools that cannot distinguish between ineffective and effective attacks!
- The most common attack types were SQL Injection, Cross-Site Scripting (XSS), and Path Traversal for the second month in a row.
SUMMARY
- Custom Code Vulnerabilities: Applications had an average of 6 open, serious vulnerabilities in September.
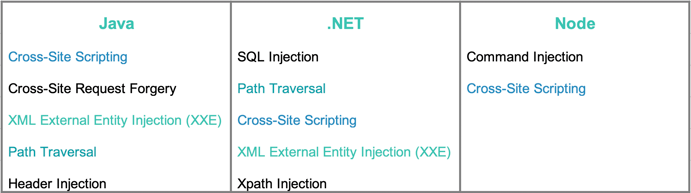
- Top Vulnerabilities by Language: Injection vulnerabilities dominated in September. Cross-Site Scripting is the most prevalent serious vulnerability for Java applications and in the top three for .NET and Node applications. SQL Injection and Command Injection vulnerabilities are the most common for .NET and Node applications, respectively.
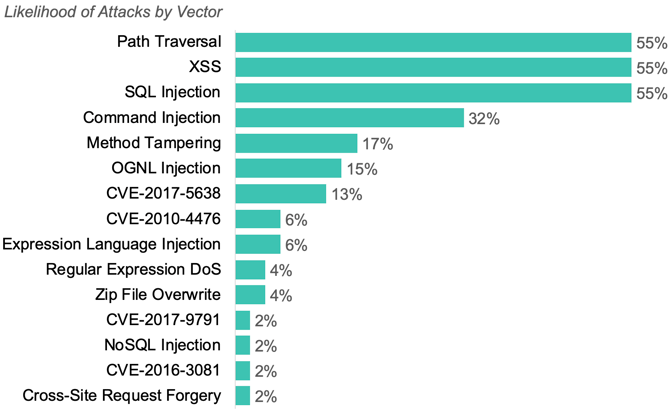
- Custom Code Attacks: We saw the continued dominance of attacks on custom code, making up 99% of attacks. The top attacks on CVEs were CVE-2017-5638, CVE-2010-4467, and CVE-2017-9791. SQL Injection, Cross-Site Scripting, and Path Traversal attacks, the top attacks on custom code, each targeted 55% of applications.
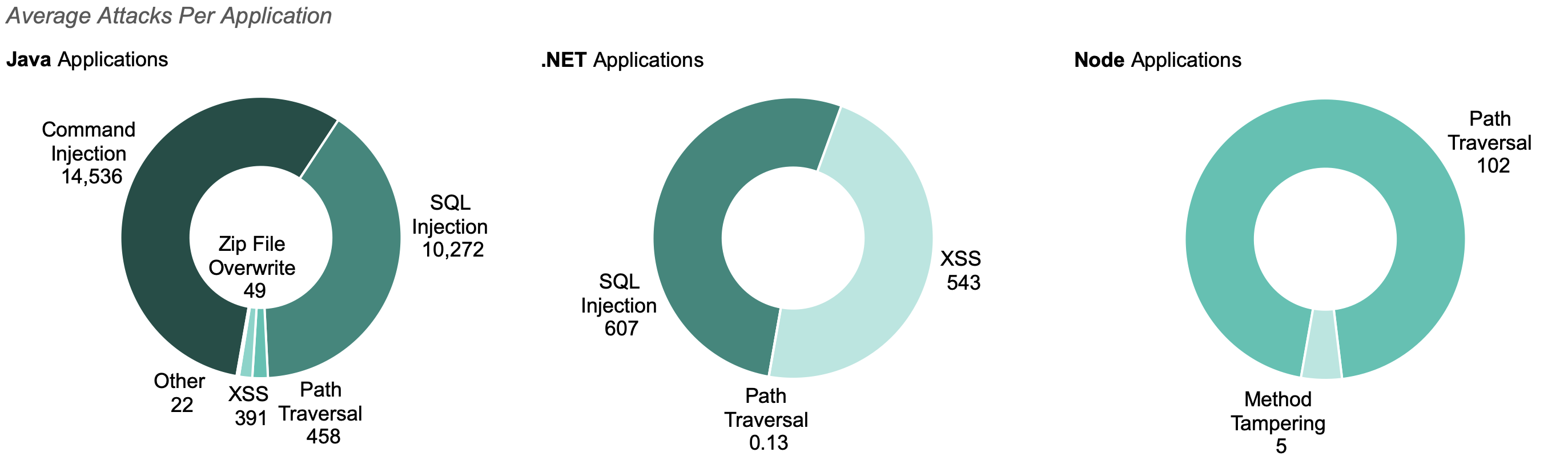
- Top Attack Vectors by Language: Injection attacks continued to dominate, with Java applications targeted the highest number of Command Injection attacks and .NET applications targeted by the highest number of SQL injection attacks.
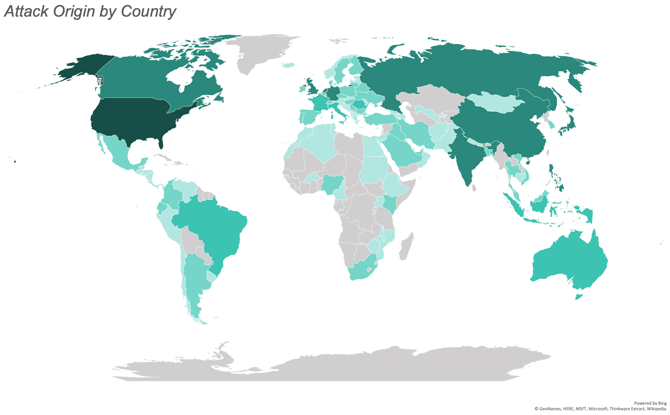
- Geo Location: Attacks originated across the globe in September, with the most attacks originating from North America, specifically the United States. India and the Netherlands were the next most common origin countries.
CUSTOM CODE VULNERABILITIES
The top more prevalent serious vulnerabilities found in custom code during September:
- Cross-Site Scripting (XSS): Vulnerabilities that occur when untrusted data ends up an HTML page without proper validation and escaping.
- XML External Entity Injection: Vulnerabilities exist when external entities are processed during XML.
- Cross-Site Request Forgery: Vulnerabilities that allow a malicious actor to force a user to complete unwanted commands.
- Path Traversal: A vulnerability that allows users to control which files are opened and read by an application.
- SQL Injection: Vulnerabilities exists anytime a developer takes untrusted data (like something you submit in a URL or a web form) and concatenates it into a database query.
TOP SERIOUS VULNERABILITIES BY LANGUAGE
CUSTOM CODE ATTACKS
The three most common attack types in September:
- SQL Injection
- Carefully crafted inputs that alter the SQL queries an application uses in order to steal data or execute code.
- Represented 42% of all attacks in September, down from 55% of attacks in August.
- Targeted 55% of applications.
- Cross-site Scripting (XSS)
- XSS attacks inject malicious scripts into benign and trusted websites.
- Represented 4% of attacks in September, returning back to the levels we saw earlier this summer
- Targeted 55% of applications.
- Path Traversal
- Attacks fool a web application into reading and consequently exposing the contents of files outside of the document root directory of the application or the web server.
- Represented 3% of all attacks in September, down from 17% of attacks in August.
- Targeted 55% of applications.
87% of applications were targeted by one of these three types during the month.
The majority of attacks (50%) targeted Command Injection vulnerabilities, though these attacks only targeted 32% of applications.
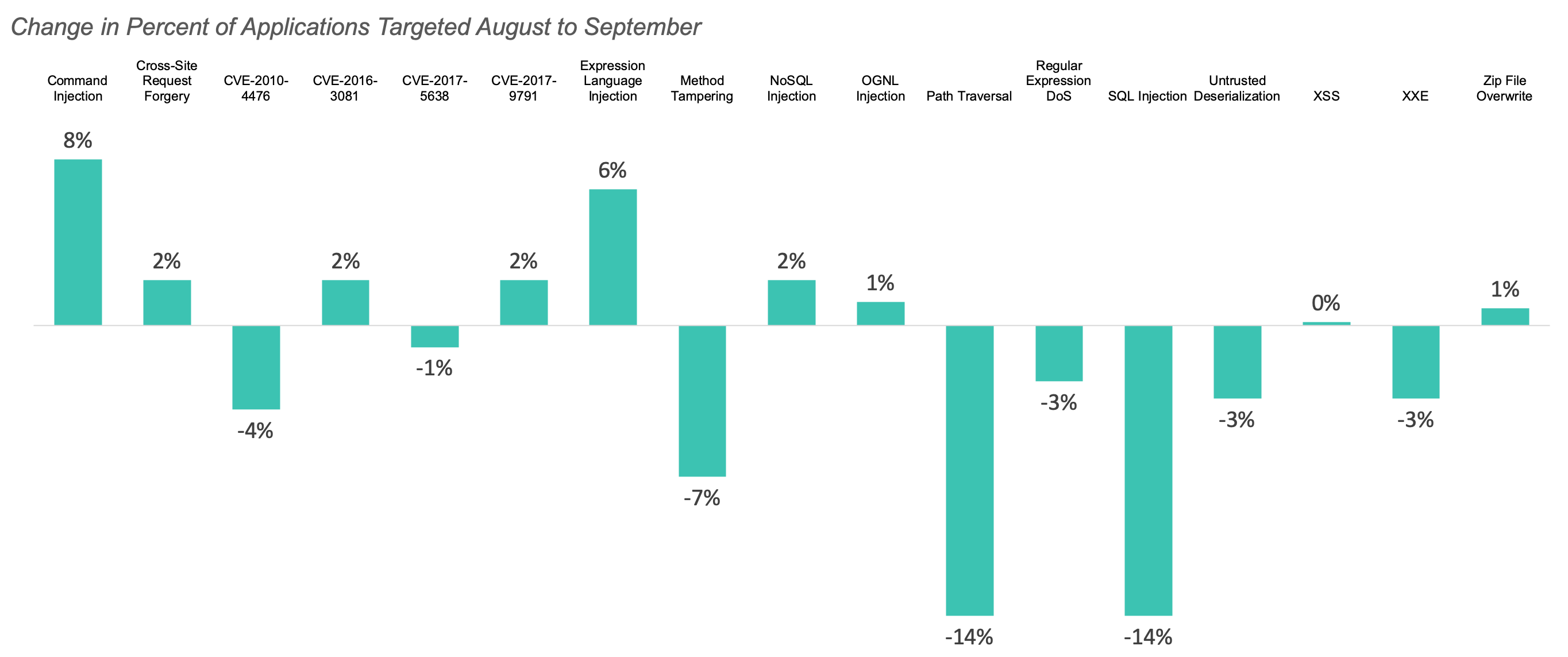
TOP ATTACK VECTORS BY LANGUAGE
ATTACKS BY GEOLOCATION
September saw attacks from 119 countries. The greatest number of attacks originated from the United States, India, the Netherlands, Canada, and the UK.
The map below illustrates the number of attacks originating from each country with the most saturated color representing the most attacks and the least saturated representing the least attacks. We observed no attacks from the countries filled in gray.