
Software affects virtually every aspect of an individual’s finances, safety, government, communication, businesses, and even happiness. Individuals need to trust software — and it makes one feel less safe when it is misused or causes harm to others. So, in response to these concerns, Contrast Security created interactive application security testing (IAST) software called Contrast Assess, that enables software applications to protect themselves against cyberattacks. Contrast Assess is accurate, easy to install, simple to use and scalable.
Application vulnerabilities are the leading cause of enterprise breaches and create major headaches for IT organizations. Traditional approaches to the problem, like penetration testing and code review, are too slow and error-prone to be effective in modern high-speed software development processes like Agile and DevOps. Unfortunately, vulnerability scanning tools — both static and dynamic — are spotty and require experts to run (see NIST study).
Contrast Security has invented a new instrumentation technology that uses sensors to passively monitor the behavior of applications and discover vulnerabilities quickly and accurately. Instrumentation provides developers with security feedback as soon as they write their code — not in weeks or months. This paper will explore the Contrast interactive application security testing technique and show how it can help organizations tackle application security without disrupting software development.
The NSA Center for Assured Software (CAS) Static Analysis Test Results are available at http://appsecusa.org/p/ nsacas.pdf. Results from the NIST SAMATE program are available at https://samate.nist.gov/docs/CAS_2011_SA_ Tool_Method.pdf.
Since 2002, Contrast Security experts have verified the security of hundreds of millions of lines of source code in thousands of applications, most of which are critical financial, energy, healthcare, defense, and government applications. To provide cost-effective reviews, Contrast invented a highly efficient manual approach that combines the best of threat modeling, architecture review, manual security testing, and security code review techniques. This method is effective because it focuses on extracting the business, technical, and application context that is necessary to identify vulnerabilities accurately, quickly, and cost-effectively.
Providing contextual information to static and dynamic scanning tools dramatically improves their performance. Based on this insight, Contrast Security invented a new way to perform fast and fully automated vulnerability analysis from within a running application. Contrast technology automatically extracts context and uses that information — along with both static and dynamic techniques — to identify vulnerabilities with accuracy and efficiency. This revolutionary new approach is called interactive application security testing (IAST).
Interactive application security testing (IAST) is performed inside the application while it runs and continuously monitors and identifies vulnerabilities. Contrast Security uses aspect-oriented programming techniques1 to create IAST “sensors” that weave security analysis into an existing application at runtime. These sensors allow Contrast to extract context, data-flow, and control-flow information from within the application and provide access to the actual data values passing through the running code. Because of this wealth of information, Contrast can identify problems that other tools cannot, and achieve an unprecedented level of accuracy without generating false positives.
For example, Contrast can identify credit card numbers extracted from a database and report when these credit cards end up exposed in a log file. It can identify a weak encryption algorithm specified in a properties file, or even data that flows from within an encoded cookie, through a data bean, into a session store, into a JSF component, and finally into a browser — indicating a Cross-site Scripting (XSS) weakness. Contrast can also see vulnerabilities spanning custom code, third party libraries, application frameworks, and the runtime platform itself. Static, dynamic, and even human security analysts have extreme difficulty finding these types of deep security flaws. Through the creation of Contrast Assess rules or “sensors” that become part of the organization’s immune system, Contrast makes it possible to deliver “security as code.” Application security experts can translate their research into new sensors in Contrast Assess, and deploy them into the development process.
Contrast correctly identifies 74% of the full suite of test cases in the NSA study, and 98% of those focused on web application vulnerabilities with ZERO false alarms. This means that Contrast can identify and provide remediation for vulnerabilities that otherwise may go undetected.
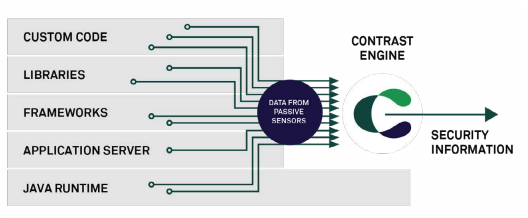
Contrast’s unique access to information about the application delivers unprecedented levels of speed and accuracy in identifying vulnerabilities as fast as applications run.
Getting great results one application at a time isn’t good enough. To help organizations meet application security challenges, technology must scale to the entire application portfolio. Contrast brings the power of intrinsic analysis to hundreds of thousands of applications. In some ways, Contrast is like analysis platforms New Relic or Google Analytics. Millions of websites use these powerful tools to extract performance and marketing information from running applications. Both services work by instrumenting running applications, sending findings to a server, and using that data to create useful reports and dashboards.
Since Contrast doesn’t require a compute farm or large scanning engine, it’s easy to add it to all application servers. As applications are tested and run, Contrast reports critical security information over a secure channel to the Contrast Team Server.
Contrast provides application security analytics by employing a similar model. When Contrast’s security plugin is installed into application servers, it automatically and invisibly instruments them with simple passive sensors and a powerful rule engine. Getting up and running typically takes less than five minutes and requires no enterprise security skills. As applications run normally during quality assurance and testing, Contrast automatically reports vulnerabilities to the Central Contrast Team Server.

All of your applications are presented in a clear, understandable dashboard. Each application also gets its own dashboard with a score for both security and coverage.
Security analysis results appear automatically in a real-time dashboard of critical security information, vulnerabilities, and remediation advice across all of applications. The Contrast dashboard displays charts, trends, metrics, and full vulnerability traces for security, development, and test teams. Each application receives an easy-to-read and understand letter grade for security based on both security and analysis coverage.
The Team Server also explains vulnerabilities to those that need to understand and fix them. Contrast’s innovative Security Trace format pinpoints exactly where a vulnerability appears in the code and how it works. All the results above were captured by Contrast after only a few minutes of browsing WebGoat, a deliberately flawed, vulnerable open source application donated to OWASP to assist developers with application security.
The SQL Injection example illustrated above explains to the developer exactly how untrusted data flows through the application and gets embedded in an SQL query without either validation or parameterization. Contrast “speaks the developer’s language,” and provides remediation guidance that is easy to understand and implement.

Contrast vulnerability reports include all of the details needed to understand the problem, find it in the code, and remediate it correctly. The simple “trace” format shows exactly how the vulnerability works with real data.
Using Contrast doesn’t disrupt ordinary software development cycles. Developers receive continuous feedback on the exact code that they are testing in their development environment. QA testers can identify security vulnerabilities and file bug reports without extensive application security experience. Application Security experts can stop wasting time chasing vulnerabilities and false positives and focus on strategic security initiatives. Because Contrast provides continuous vulnerability detection, security analysis does not have to be a large cumbersome effort at the end of the software development lifecycle. Instead, security happens naturally, continuously throughout the development process. Issues are addressed on- the-spot, quickly and efficiently.
Contrast provides complete coverage of the OWASP Top Ten and beyond. Because Contrast works inside the application, it identifies all complex variants of each vulnerability type.
Contrast provides coverage over most common vulnerabilities, including the OWASP Top Ten. Unlike tools that claim coverage for a category when they only find a few simple examples, Contrast’s coverage is extensive. Note that there are no rules for: Insufficient Transport Layer Protection (A6) and Security Misconfiguration (A9), since these are typically enforced outside of the Java environment.
| SQL injection (A1) | Weak encryption algorithm (A7) |
| Blind SQL injection (A1) | Authorization missing (A8) |
| Command injection (A1) | Arbitrary forward (A10) |
| Reflected XSS (A2) | Unchecked redirect (A10) |
| Stored XSS (A2) | No size limit on data read |
| Session ID disclosure (A3) | File download injection |
| Path traversal (A8) | HTTP header injection |
| Insecure direct object reference (A4) | And more... |
| Weak hash algorithm (A7) |
Contrast automatically gathers all application portfolio information that can be so difficult to gather manually. Upto-date information is available on what applications are in use, including metadata like lines of code, libraries in use, component technologies, architecture, and back end connections.
Like icebergs, 80 percent of the code in modern applications is “beneath the surface,” lurking in libraries, frameworks, and other components. Applications often have 50 or more of these libraries, comprising millions of lines of potentially vulnerable code. We released a study2 detailing findings from 113 million downloads of the 31 most popular Java frameworks and security libraries from more than 60,000 organizations. Contrast Assess automatically analyzes these libraries and provides a detailed dashboard.
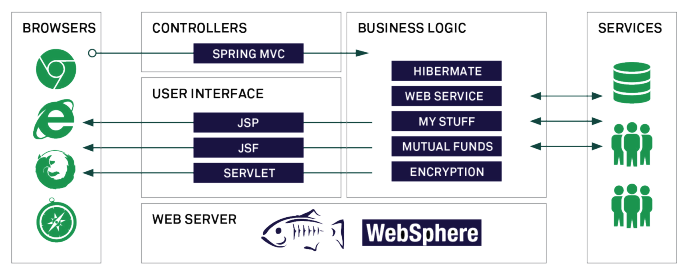
Understanding an application’s architecture is extremely helpful when performing security analysis. Contrast gathers information from within the running application about the software architecture and connected components. Contrast automatically generates simple diagrams that illustrate the application’s major architectural components. This information helps the developer quickly identify the meaning of a vulnerability that Contrast pinpoints. In this example, Contrast has correctly identified that the WebGoat application has three backend connections: an LDAP directory, a web service, and a database. Contrast lists the frameworks being used within the application: Spring, JSF, and Hibernate. Imagine the benefit of having up-to-date architectural information available, on demand, across entire application portfolio.

In an extensive study, we discovered that 29.8 million (26%) of open source library downloads in 2011 had known vulnerabilities. Further, more than half of the Global 500 use software built using components with vulnerable code. Read the rest of the study at: https://www.aspectsecurity.com/blog/theunfortunate-reality-ofinsecure-libraries
Contrast monitors Java and .NET code execution, data flow, configurations and more to quickly find dangerous vulnerabilities with virtually no false positives. Code-level pinpointing eliminates guesswork while context sensitive guidance enables quick remediation.
Contrast transparently automates application security to support application portfolios of virtually any size. New applications are discovered automatically as they are run. Executive-level portfolio dashboards display the entire portfolio security posture in real-time.
It takes minutes to go from zero to resolving application security issues using Contrast’s SaaS service. Contrast can also be hosted and administered on-site, enabling a completely administered private service.
As much as 80 percent of software code comes from open source and third-party libraries. Contrast automatically discovers third-party libraries, alerts to the known (and unknown) risks they may bring with them, and provides critical versioning and usage information that helps remediate risks.
Continuous integration and deployment require fast and continuous security. Scriptable silent installers, automated updates, and a REST API enable Contrast to deliver security as fast as applications change.
Contrast Assess is a new application security solution that provides a fast, accurate, easy, and scalable way eliminate the most serious risks facing enterprises today.
Organizations using Contrast Assess receive continuous, always-on visibility into the security of all their applications. Contrast analyzes every line of code, in every application, for visibility from the inside. By knowing what’s happening across the entire application portfolio, organizations can prioritize their development and operations teams to remedy the most critical risks right now, and reduce friction throughout the entire software lifecycle.
Unlike tools that create bottlenecks through periodic or serial application portfolio testing, Contrast uses a highly scalable architecture that empowers every application to analyze, enforce and communicate about application security. Contrast strengthens an organization’s immune system to defeat vulnerabilities across the entire application portfolio, rather than only for a chosen few.
1 https://en.wikipedia.org/wiki/Aspect-oriented_programming. Or, for an easy example of how aspect-oriented programming works, see: http://www. infoworld.com/article/3040557/application-development/my-two-cents-on-aspect-oriented-programming.html
Schedule a demo and see how to eliminate your application-layer blind spots.
Book a demo
