A new joint solution from Contrast Security and Kenna Security enables organizations to manage vulnerabilities in one location with fewer false positives to simplify application security programs on both custom and third-party code.
This open-source integration (available on GitHub) can import results from Contrast Assess and Contrast OSS and then synchronizes them within Kenna.VM. Security teams can then consolidate results from multiple tools and techniques and report on the overall success of the security program. Success is measured in terms of remediation rather than just scanning or finding. The results are dramatic, with a new study showing that developers fix Contrast issues about 29 times faster than issues reported through other tools.
A report between Kenna and the Cyentia Institute evaluated the path that vulnerabilities take between obtaining a CVE number and being patched or exploited. While a few common paths exist, there is no single path that vulnerabilities take to become a CVE if they become one at all. Further, most vulnerabilities in custom code never receive a CVE number. As a result, with CVE identifiers focused on vendor software and libraries, organizations must work to locate their own vulnerabilities in custom code. By reporting custom code vulnerabilities and CVE-impacted libraries into Kenna, Contrast helps developers produce secure applications while enabling security teams to scale their expertise through self-service tools.
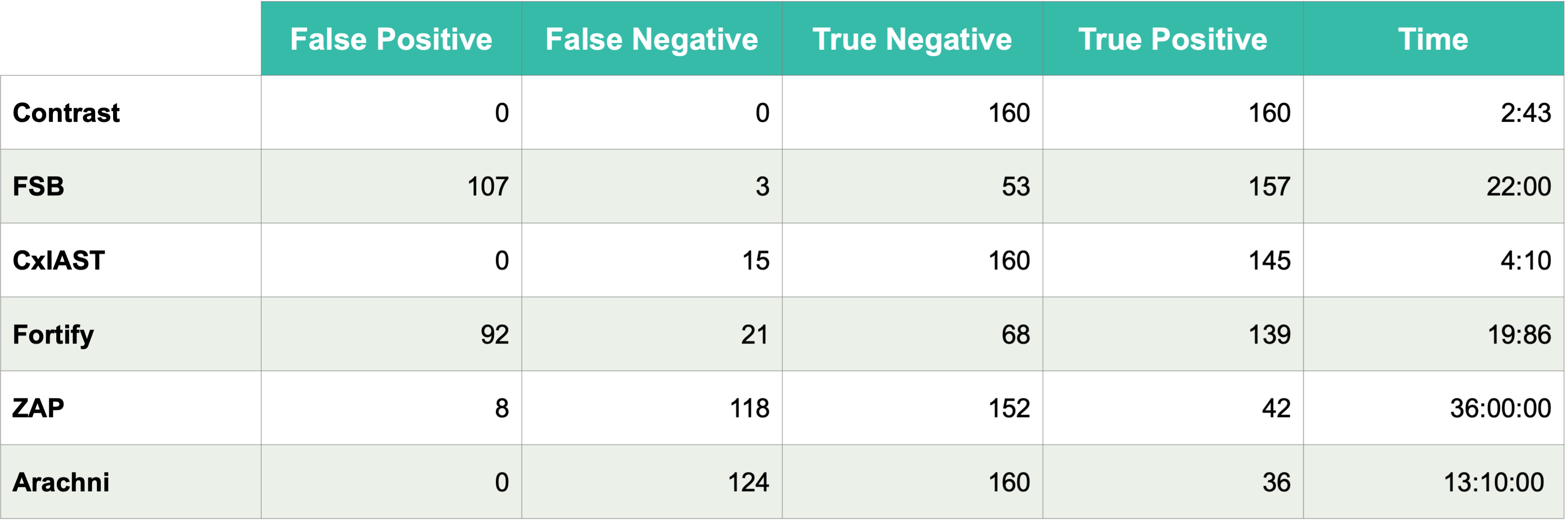
In 2020, the Department of Computing and Technology at Cameron University and Escuela Superior de Ingeniería y Tecnología, Universidad Internacional de La Rioja performed a study to combine static, dynamic, and interactive testing to evaluate the speed and efficacy of each analysis type using over 320 test cases. This independent test benefits Kenna users because it ensures that impactful security results appear quickly while minimizing the number of issues that are tracked, reported, and disputed with development teams.
Page 11 reports the false positive/negative and true positive/negative tests:
Integrating results between Contrast and Kenna
Sharing results between Contrast and Kenna solutions requires obtaining relevant access keys and automating how often users want to run the synchronization. Once results are shared, Kenna becomes the single pane of glass for reporting and visibility, while Contrast manages the state of each vulnerability to determine if/when remediation has occurred or to provide its own contextual “how-to-fix” insights.
Getting started with the Contrast integration into Kenna.VM is fast and easy:
Ensure that Docker is available on your system to run the tools.
Obtain the image following the instructions: docker pull kennasecurity/toolkit
Locate your Contrast Security keys by expanding your name at the top right and clicking User Settings. Locate your keys.
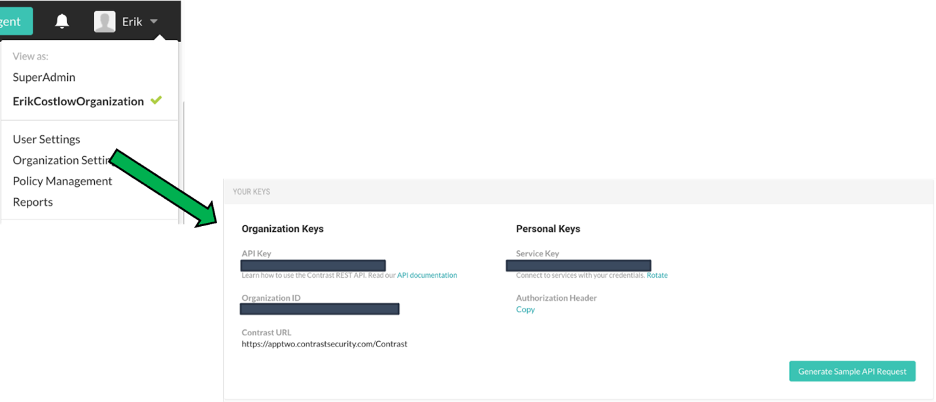
Locating keys in the Contrast dashboard
In the Kenna UI, locate your Connector ID.
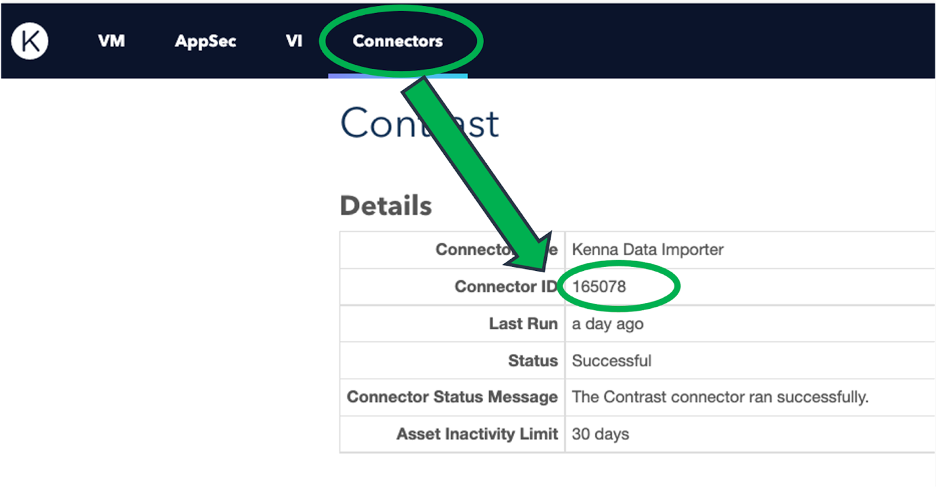
Locating the Connector ID number in Kenna
Decide if you want to import everything from Contrast into Kenna, or to mark specific sources with a tag. The reason for using a tag would be to avoid importing sources from Contrast that include test or sandbox data. The tag can allow you to keep that information out of Kenna entirely. You must then ensure that this tag is applied to relevant projects in Contrast. A common tag name that many use for this is simply “kenna.”
Many groups run this nightly or weekly through crontab. If you are using contrast_application_tags, then periodically monitor Contrast to ensure the tag is correctly applied per your intentions and policies.
Run a command that looks like this:
docker run -it --rm toolkit:latest \
task=contrast \
contrast_host=YOUR_CONTRAST_HOST \
contrast_org_id=YOUR_CONTRAST_ORG_ID \
contrast_api_key=YOUR_CONTRAST_APY_KEY \
contrast_auth_token=YOUR_CONTRAST_TOKEN \
contrast_application_tags=IF_YOU_WANT_TAGS_COMMA_ONLY
kenna_api_host=YOUR_KENNA_HOST \
kenna_api_key=YOUR_KENNA_API_KEY \
kenna_connector_id=YOUR_KENNA_CONNECTOR
Look at results inside the Kenna AppSec tab.
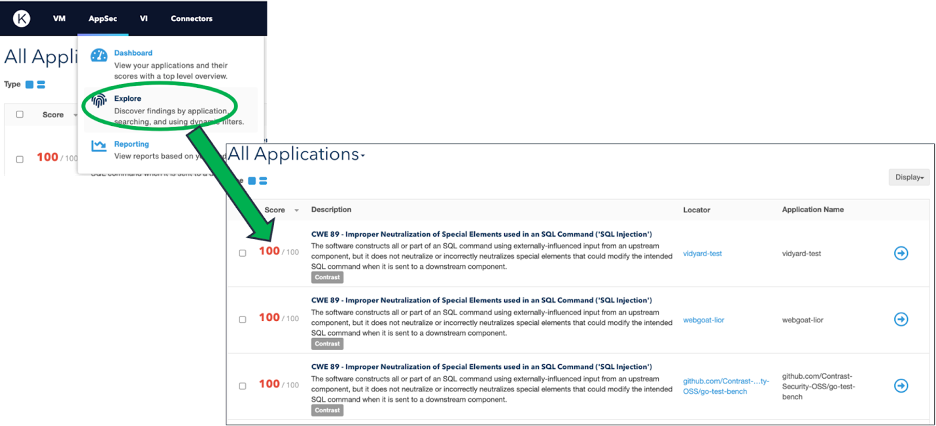
Locating Contrast Assess results in the Kenna AppSec tab
After running the above, results from Contrast will appear inside Kenna for visibility and reporting. Teams should continue to use Contrast Assess to locate new vulnerabilities and track remediation of existing issues.
Fixing a vulnerability gets more expensive as the development process gets further from where the error was introduced. The combination of Contrast and Kenna provides better application visibility, accurate risk scoring, and contextual “how-to-fix” guidance to help organizations remediate issues earlier in the development cycle.
Users can integrate Kenna and Contrast together now at no additional cost or license. To learn more about solution capabilities, be sure to read the Contrast and Kenna joint solution brief. Or if you would like help with the integration, please reach out to me for assistance.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.