By David Lindner, Chief Information Security Officer
August 16, 2021
High-profile, damaging cyberattacks continued unabated in May and June of this year. Many American consumers felt the impact of ransomware attacks on Colonial Pipeline and JBS USA—especially those on the East Coast. Both incidents caused operations to be suspended for several days, creating local shortages of gasoline and meat, respectively.
Elsewhere, the Irish Health System was shut down for nearly a week, endangering the well-being of the citizens of an entire country at a time when health systems are being strained, to say the least. Attacks on healthcare organizations extended from operational disruptions and outages to data breaches: Two million patient records, for example, were exfiltrated in a ransomware attack on CaptureRx.
Attacks on the application layer continued as well. In June, bad actors exfiltrated the source code behind several popular video games marketed by EA, including the soccer game FIFA 21, and sold copies on the black market. In another instance, 1.1 billion pieces of user information were scraped over eight months from Alibaba’s Taobao shopping site, apparently via an application vulnerability.
These incidents suggest that the application layer is still a favorite target of attackers, building on the success of the massive SolarWinds and Microsoft Exchange attacks—and the more recent Kaseya attack. Overall, Verizon’s 2021 Data Breach Investigations Report found that 39% of data breaches in the past year have been the result of an application vulnerability.
Security researchers continue to search out vulnerabilities in software as well, and they are often able to notify the application owners of what they find before attackers can use them to cause harm. In May, a vulnerability was announced in one of Peloton’s application programming interfaces (APIs) that enabled access to user account data. This vulnerability was patched, fortunately, before a successful attack was executed. This is a continuation of a busy year for security researchers, who have identified a new vulnerability type called dependency confusion and serious vulnerabilities in a number of applications, including Microsoft Teams.
In this environment, Contrast's Bimonthly Application Security Intelligence Report for May–June shows a continuation of several important trends, including a higher proportion of vulnerabilities that are serious and a record-high percentage of attacks that were probes. Contrast Labs produces these bimonthly reports to help readers prioritize their application security efforts around vulnerability and attack trends observed in the telemetry data from our customer base.
The report begins by updating the Contrast RiskScore™ Index for May–June. The biggest trend with our easy-to-understand enumeration of the relative risk of different vulnerability types is that it has been declining for a year. This is because of the dataset we are using—applications protected by the Contrast Application Security Platform.
Because they are “shifting left” and “shifting right” with their application security efforts, overall risk declines over time for Contrast customers. In May–June, 16 of the 19 vulnerability types we measure decreased compared with March–April. And the overall average RiskScore was 4.96 in this bimonthly period, down from 5.06 in the prior period and the lowest average so far.
The four highest RiskScores belonged to the same vulnerability types that appear almost always in those top spots—broken access control, cross-site scripting (XSS), insecure configuration, and sensitive data exposure. SQL injection moved into fifth place again after trading places with broken authentication for months. Two vulnerability types saw big increases—NoSQL injection and denial of service. Expression language (EL) injection, on the other hand, saw a massive decline from the last bimonthly period, though we predict its resurgence in the near future.
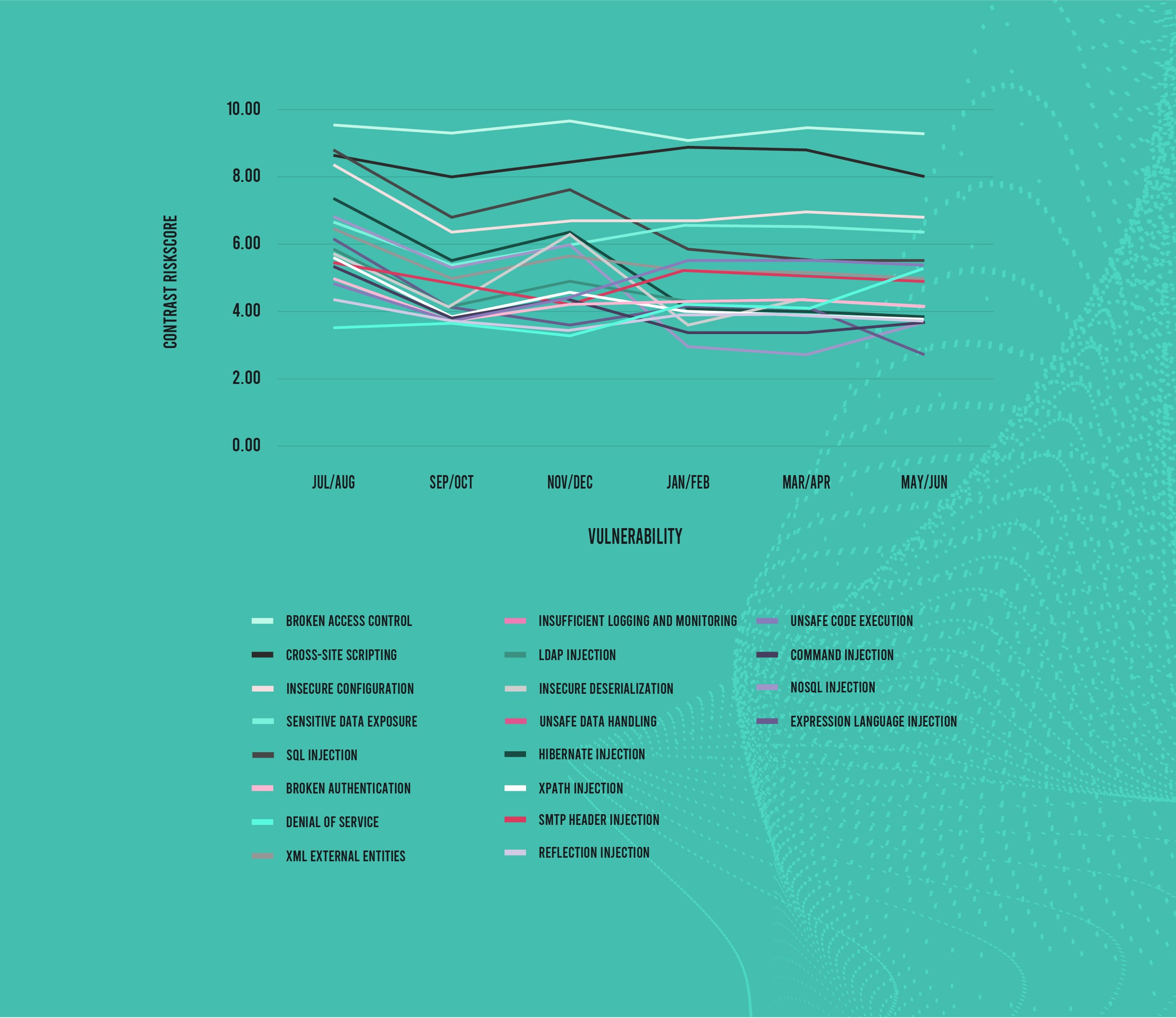
The average RiskScore has declined over time, with 16 of 19 vulnerabilities down from the previous bimonthly period.
Custom-code vulnerabilities continue to impact almost all applications, but the percentage of applications with at least one serious vulnerability decreased to 31% from 32% in March–April, something of a reversion to the mean. But when one looks at the whole universe of vulnerabilities, a bigger percentage of them—41%—are rated as Critical or High. That number has been steadily increasing for a year, up from 28% last July–August and 38% in March–April of this year.
Also concerning is the fact that applications that have any serious vulnerabilities tend to have a lot of them—59 to be exact. XSS and broken access control continued to be present in a far higher percentage of applications than any other type. At least fewer applications had more than 100 serious vulnerabilities—2% versus 3% in March–April. This suggests that some organizations are making headway on their security debt—something that we also reported in our just-published 2021 Application Security Observability Report.
More Java applications continued to see serious vulnerabilities than .NET ones, 28% to 24%—an increase in one percentage point in both cases.
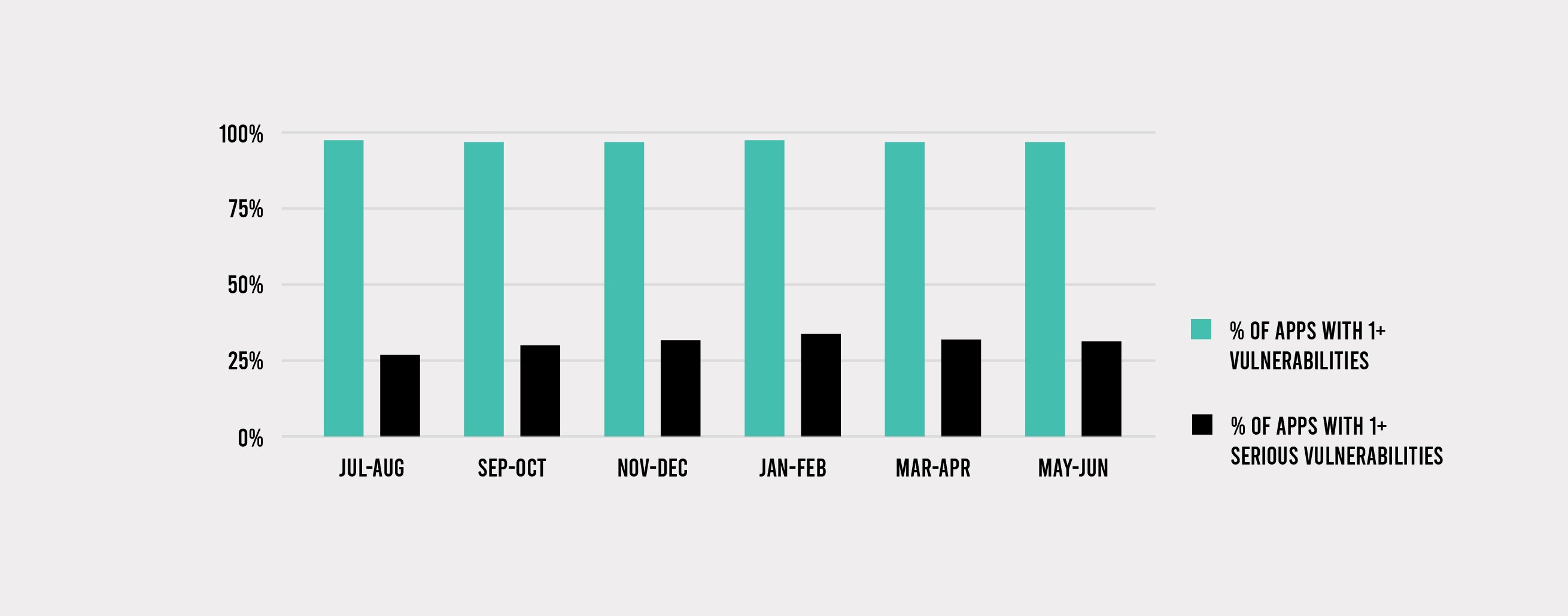
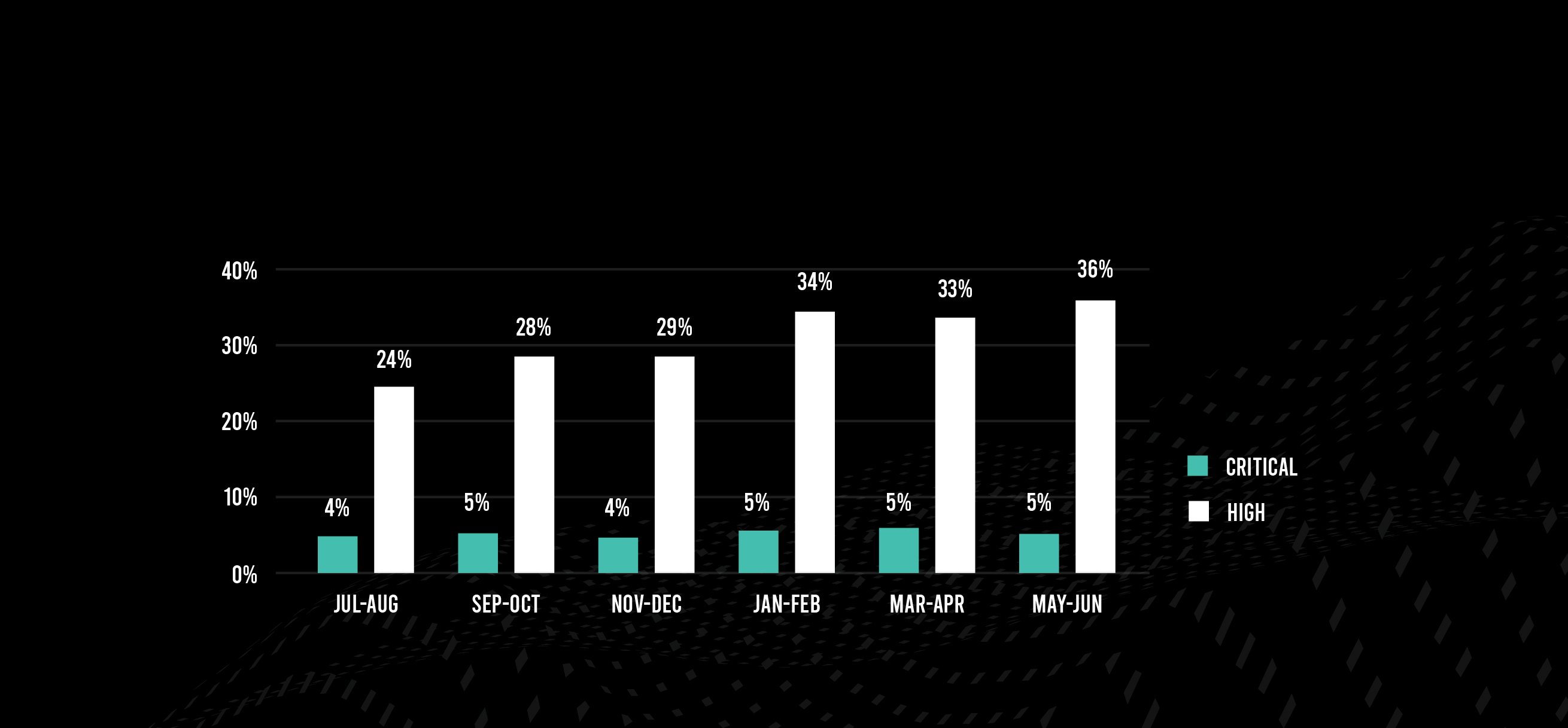
The percentage of applications with a serious vulnerability declined slightly, but the percentage of vulnerabilities that are serious increased.
The biggest story on the attack front is the extremely low percentage of viable attacks in May–June. Specifically, just 0.2% of attacks hit an existing vulnerability in an application, the lowest figure we have observed. This is a big drop from the 3% we reported in March–April but closer to the 0.3% seen in January–February. The 99.8% of attacks that were probes were not useless for bad actors, however; they provide intelligence that can inform future successful attacks.
Command injection attacks were popular in May–June, impacting 57% of applications compared with 33% in March–April, a 73% increase. But EL injection, remote file inclusion, and vulnerability scanner saw big declines on a percentage basis. Looking at attack types by language, more than 75% of Java applications experienced SQL injection, broken access control, XSS, and command injection attacks. For .NET applications, 84% saw broken access control attacks, while SQL injection attacks only hit 21%—a decline of 45 percentage points compared with March–April.
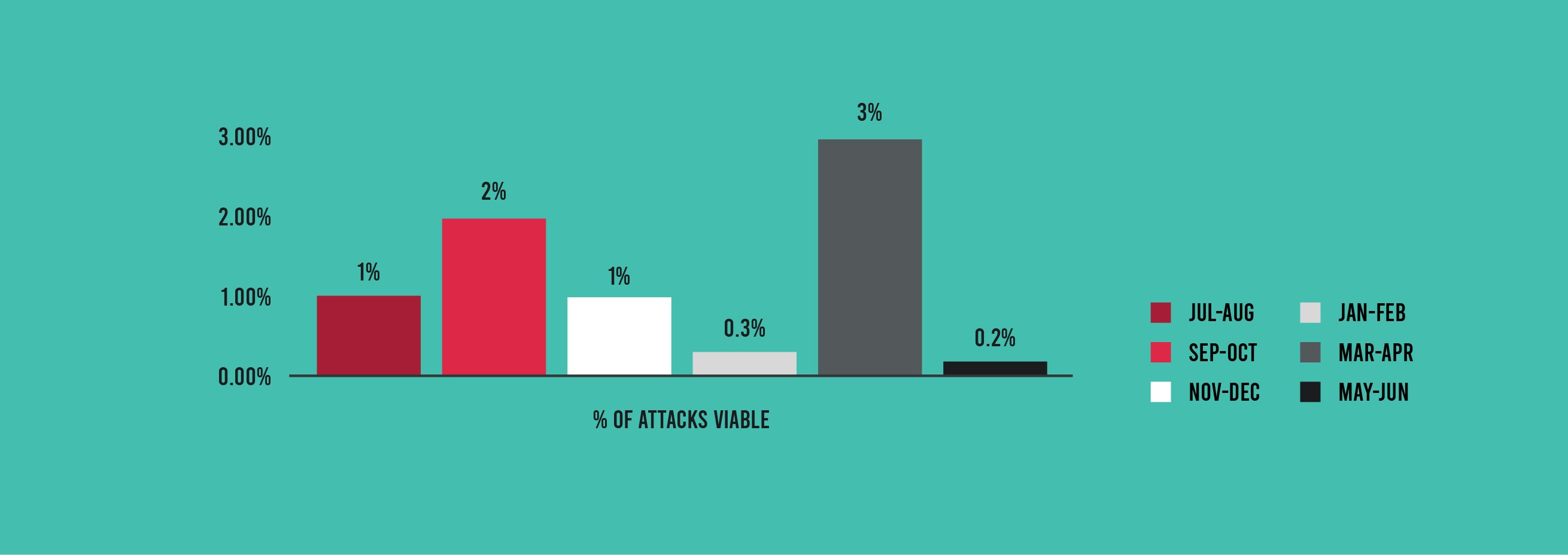
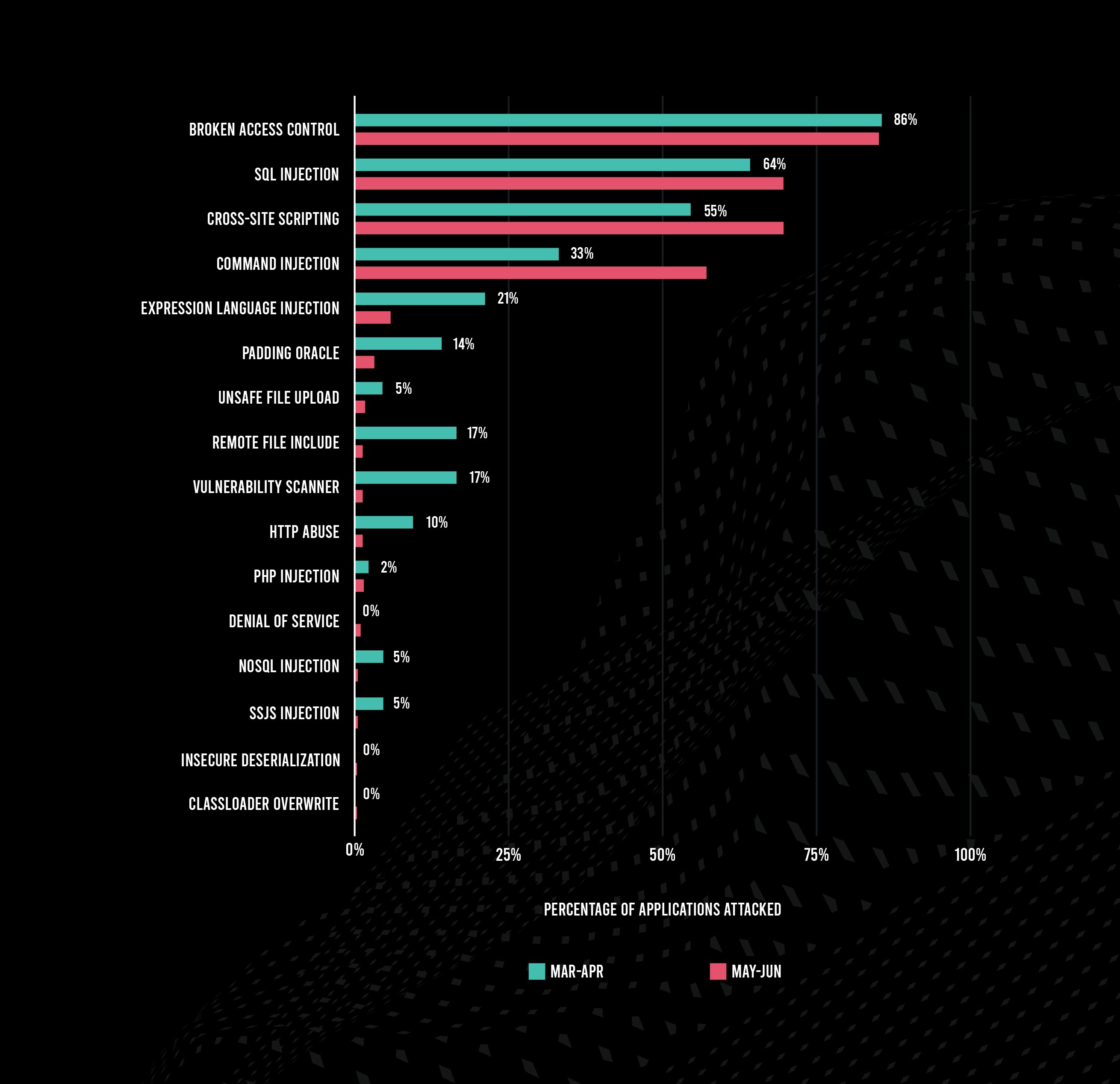
The percentage of attacks that were viable decreased to a record-low 0.2%, and command injection and XSS impacted a growing percentage of applications.
The biggest benefit of our bimonthly Application Security Intelligence Reports is that the data comes from real-world applications protected by Contrast Security. As a result, readers can gain insight into the vulnerabilities and attacks that are out there while seeing in real numbers how the Contrast Application Security Platform helps organizations mitigate risk.
Vulnerability trends stabilized in May–June after some numbers were elevated earlier in the year. Nevertheless, the increasing proportion of all vulnerabilities that are a must fix means that organizations need to focus on resolving those cases quickly and reducing security debt. Attackers returned to an extremely high percentage of probes, with just 0.2% of attacks hitting an existing vulnerability, but applications continued to be pummeled with thousands of attacks.
But whatever the details in a given bimonthly period, one thing we see consistently in our research is that the Contrast Application Security Platform provides protection for our customers that other organizations do not have. Security instrumentation enables continuous security testing from within the application, and this in turn makes full observability of an organization’s entire application security posture. It enables organizations to “shift left” to catch and repair vulnerabilities earlier in the process, and also to “shift right” to protect applications in production with runtime protection.
Cybersecurity is becoming an even more vital concern for governments and other organizations around the world. The White House recently issued an executive order that aims to set more effective standards for cybersecurity, and application security is a big part of that action. As attacks intensify and become more sophisticated, organizations must achieve a continuous, “always-on” approach to application security.
REPORT: Contrast Labs Application Security Intelligence Bimonthly Report for May–June 2021
PODCAST: Serious Vulnerabilities Per Application Jump in Latest Bimonthly AppSec Intelligence Report

David is an experienced application security professional with over 20 years in cybersecurity. In addition to serving as the chief information security officer, David leads the Contrast Labs team that is focused on analyzing threat intelligence to help enterprise clients develop more proactive approaches to their application security programs. Throughout his career, David has worked within multiple disciplines in the security field—from application development, to network architecture design and support, to IT security and consulting, to security training, to application security. Over the past decade, David has specialized in all things related to mobile applications and securing them. He has worked with many clients across industry sectors, including financial, government, automobile, healthcare, and retail. David is an active participant in numerous bug bounty programs.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.